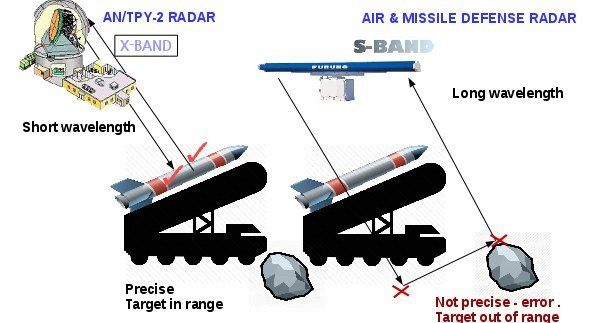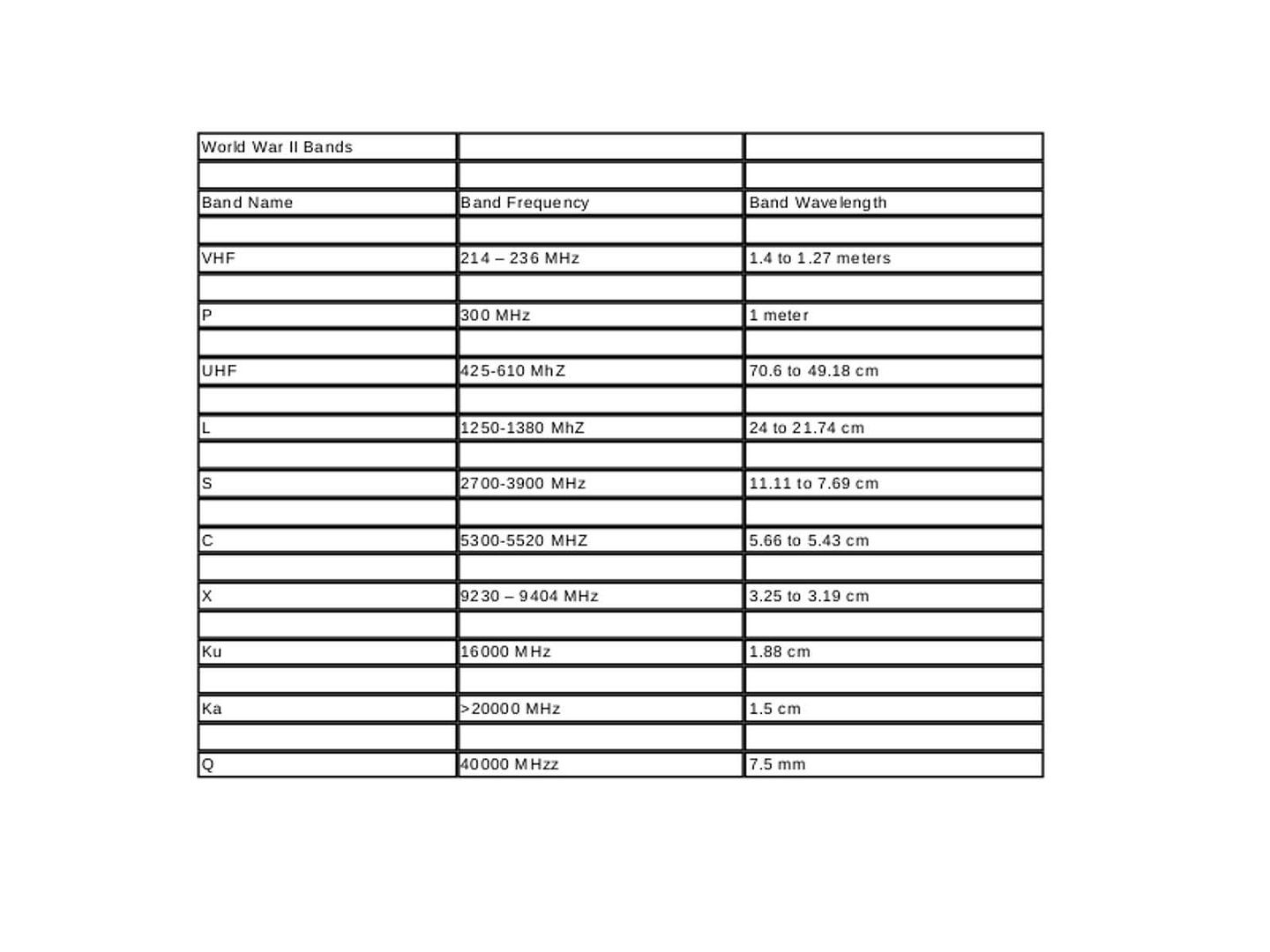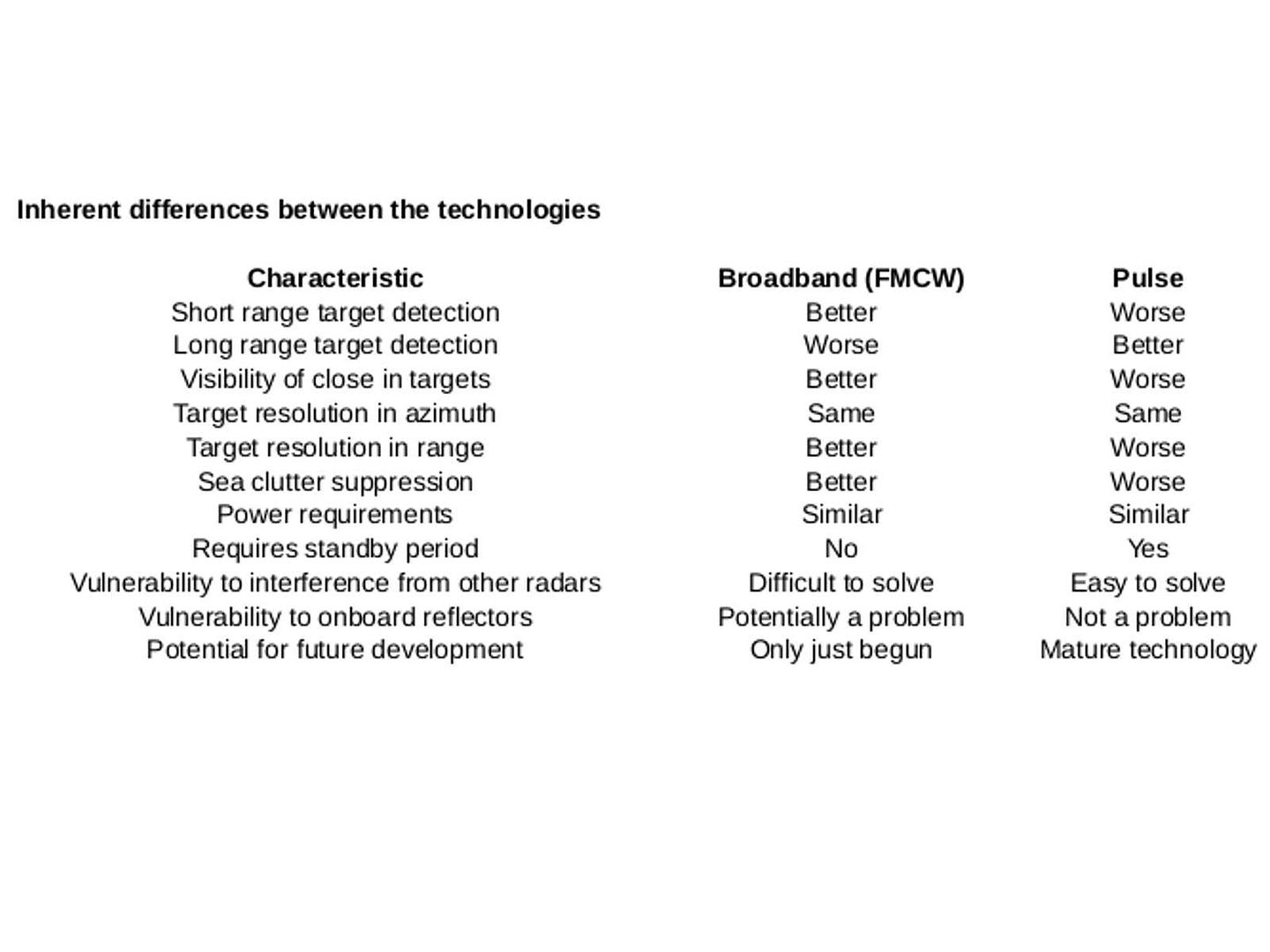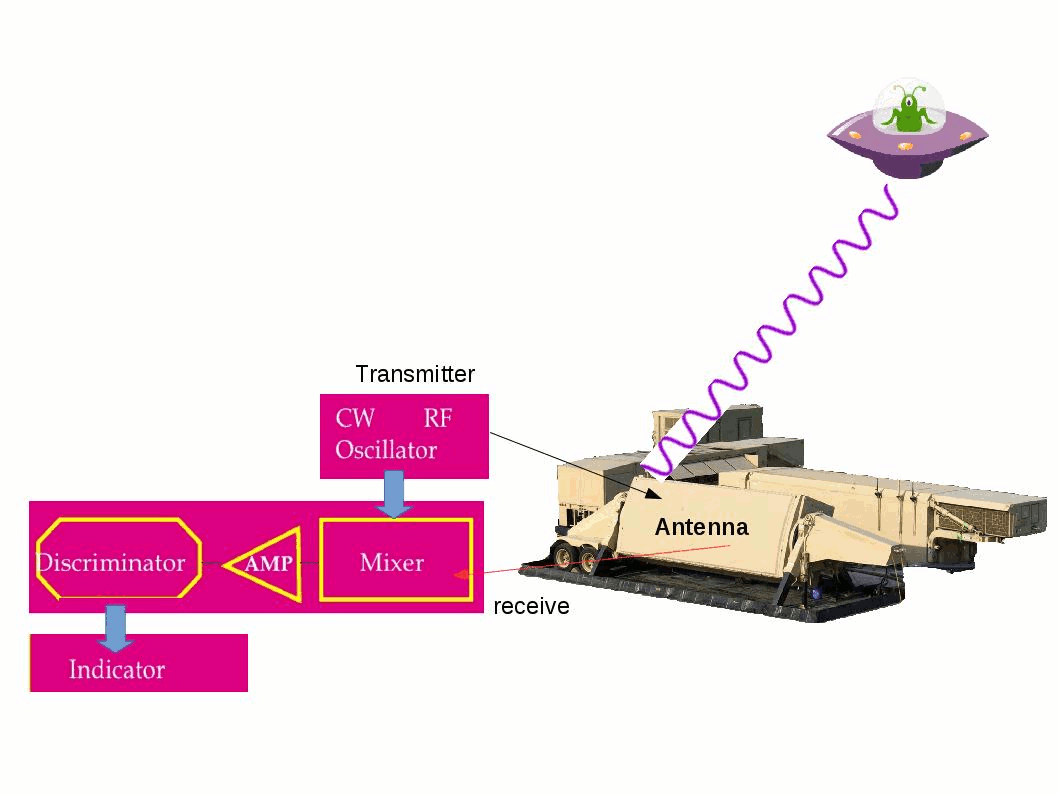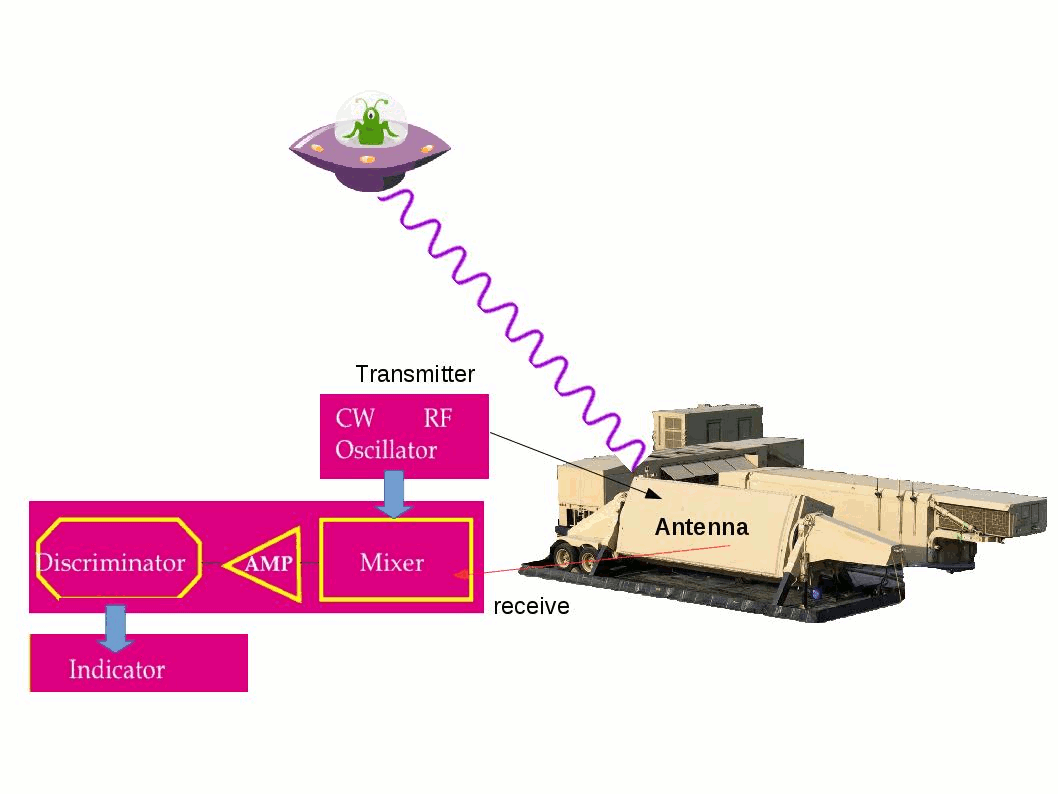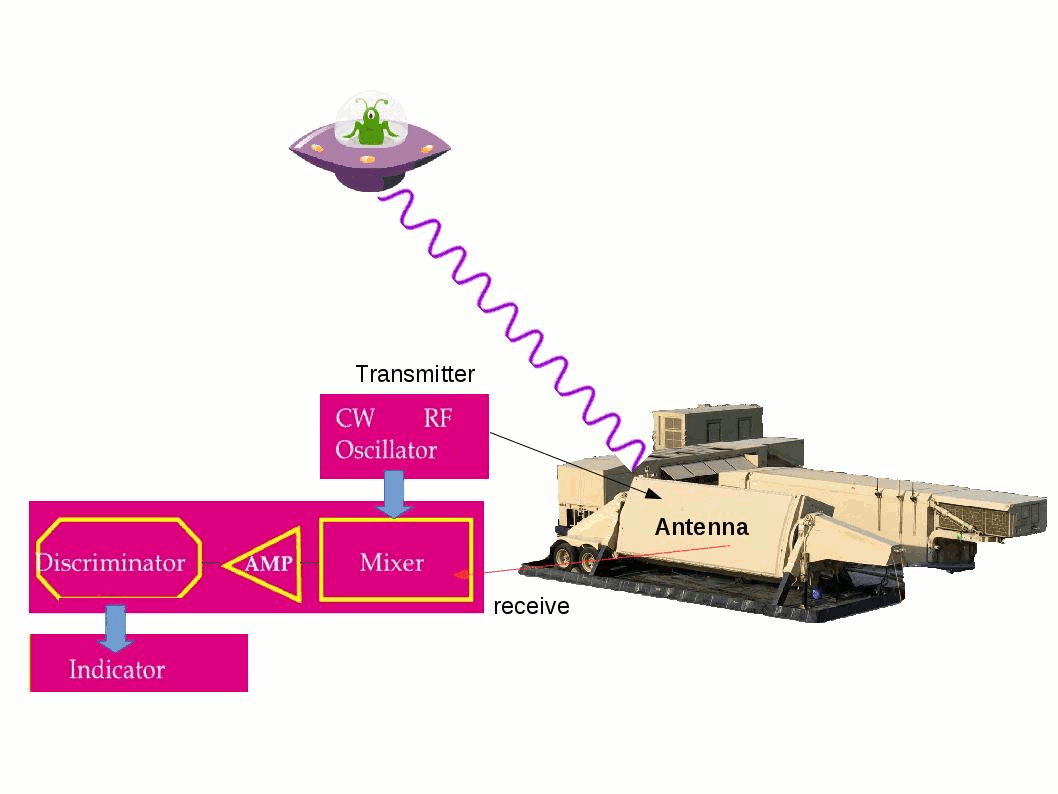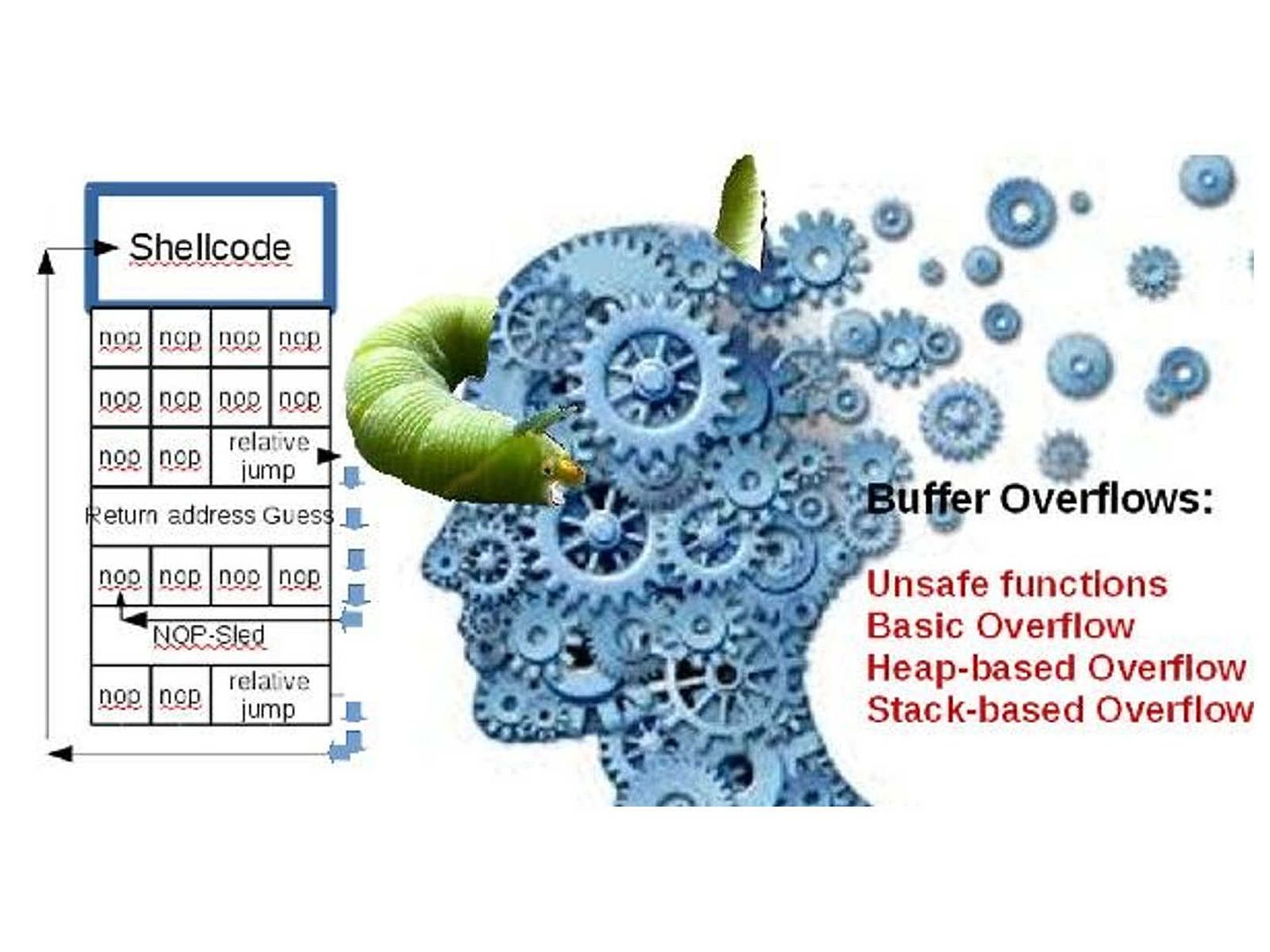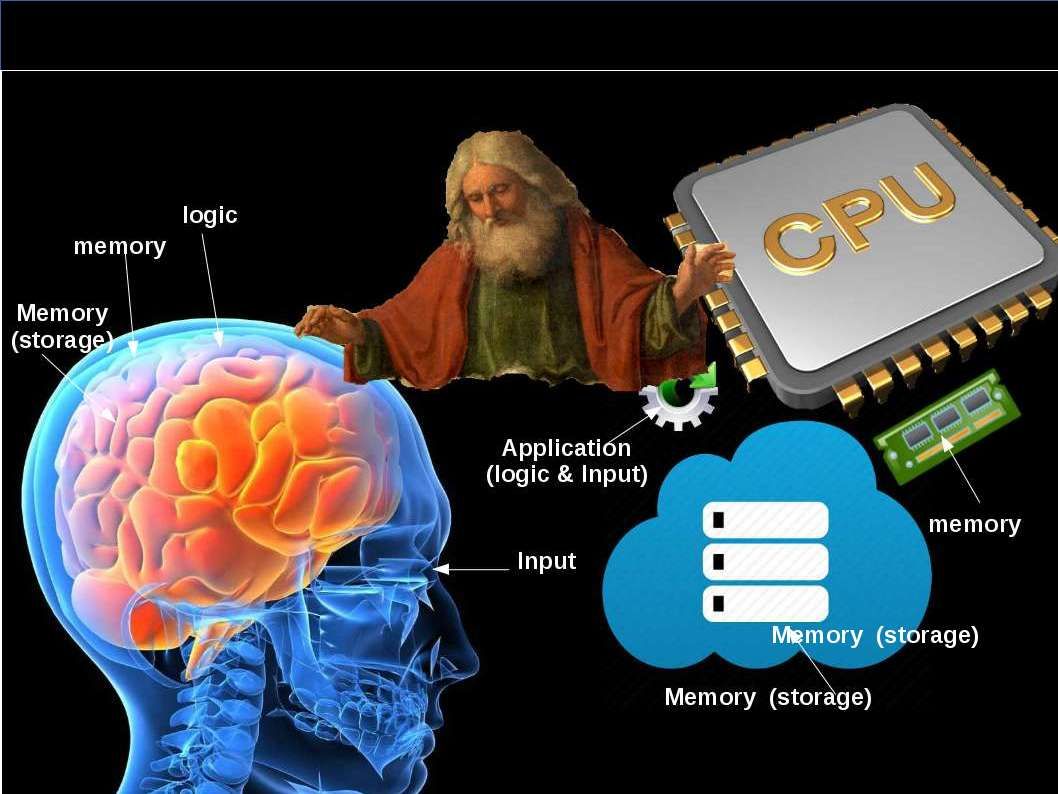
Did you read science fiction book? For instance Terminator, Matrix …etc. The overall idea of the story reminded that computer system is the governor of human being finally. Human being under their control. Can nightmare come true?
Computer technology growth rapidly after year 2000. Still remember that our team concerns thousand years worm interfere the computer clock during that day. But wake up next morning feeling that the technology go to new century.
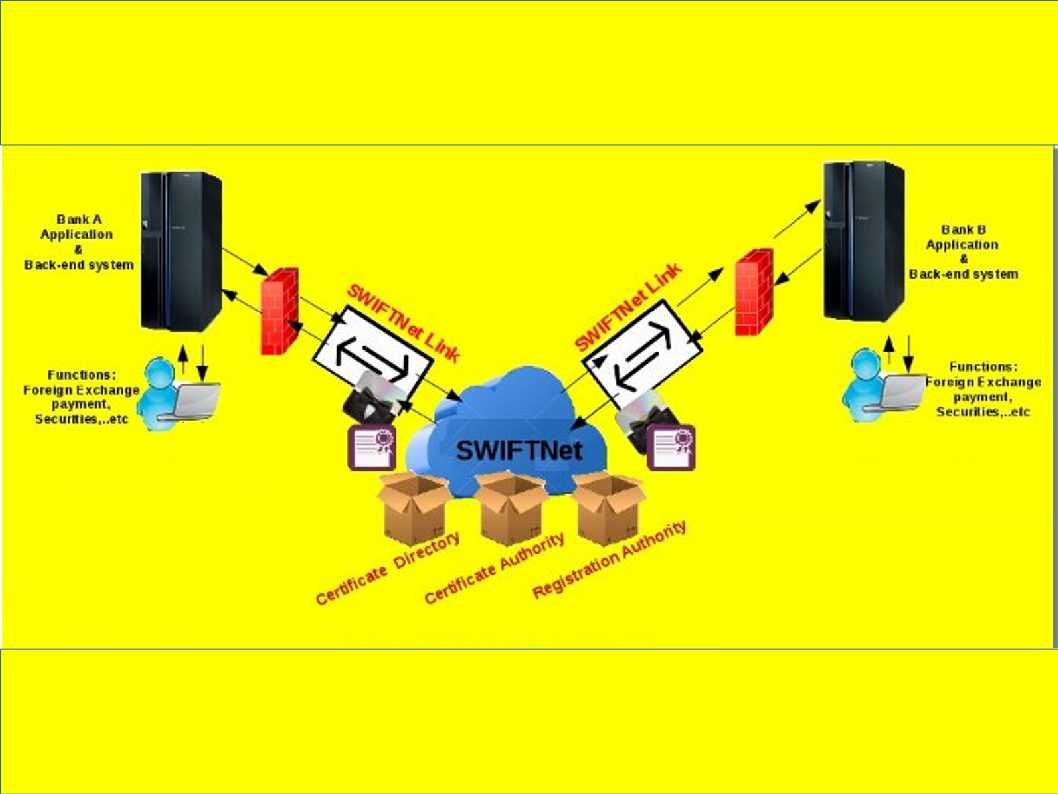
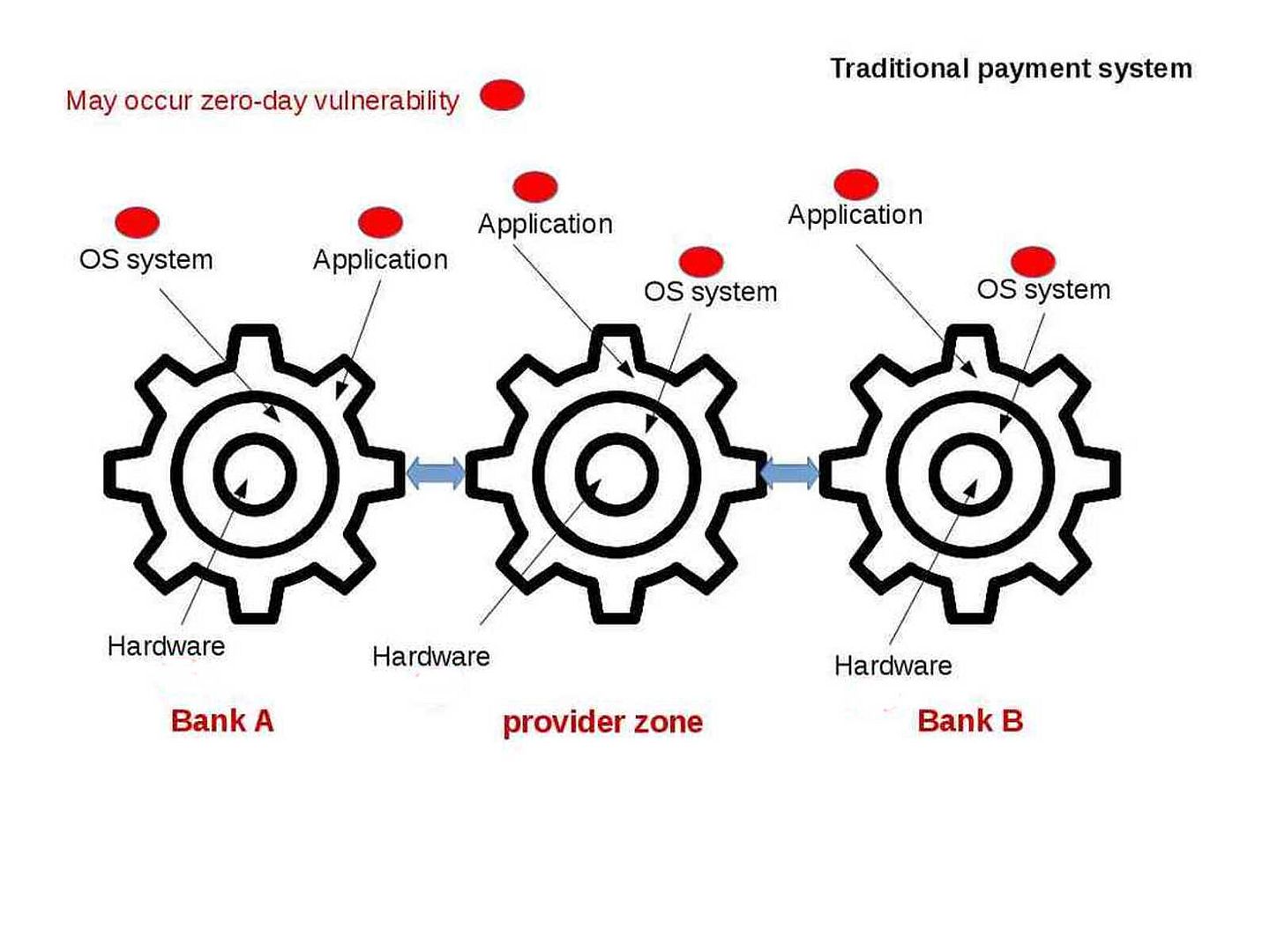
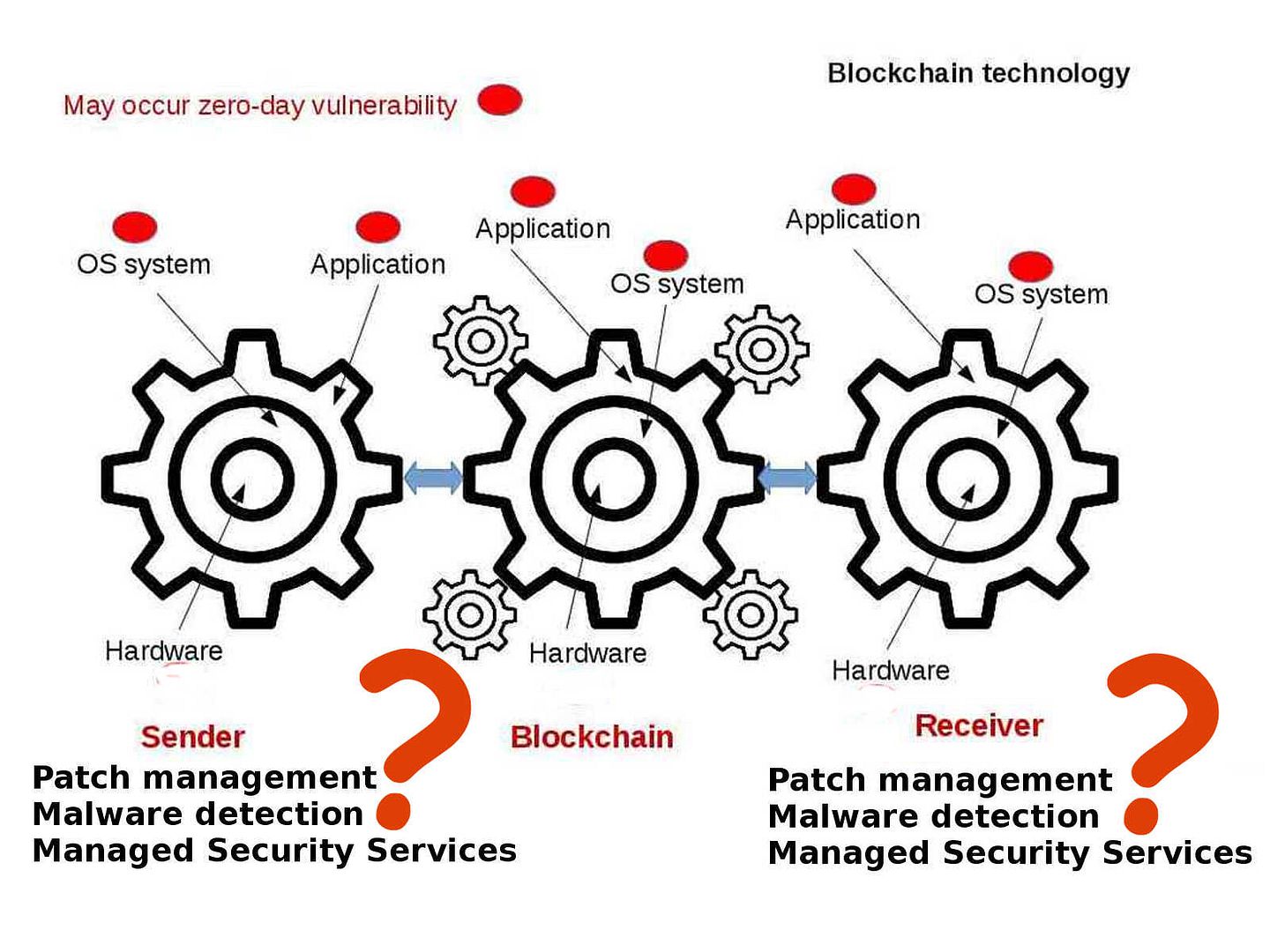
This topic brings to my attention and the informations pulling myself go to science technology instead of IT technology. The digital DNA term I heard from HB Gary. Yes, he is the former malware hunter. Their services provides advance detection and prevention solutions to government sector and financial institution. But the nature of digital DNA here looks have difference. This element (digital DNA) is equivalent to human being component. As we know, the origin of human life through chemical evolution. Two important of points drawn to biological evolution shown as below:
- Living things descended from a common ancestor and thus have common chemistry.
- Living things adapt to their environment.
Without DNA, it would be impossible to pass on adaptations, and evolution would be virtually non-existent.
Genesis element – DNA or digital DNA

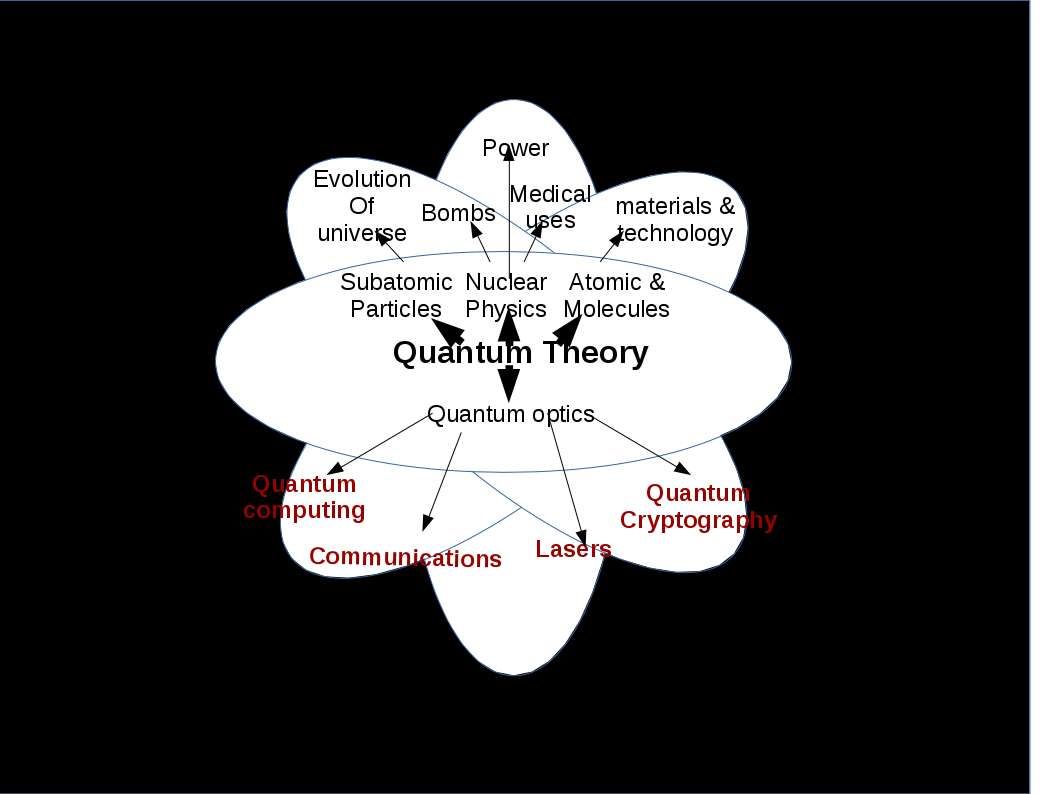
Genesis element – Quantum
Quantum theory distributed in major IT technology domains. They are network communications, encryption and quantum computing. The major component of quantum computing is quantum bits. One of the great challenges for scientists seeking to harness the power of quantum computing is controlling or removing quantum decoherence – the creation of errors in calculations caused by interference from factors such as heat, electromagnetic radiation, and material defects.
Read more at: http://phys.org/news/2015-04-scientists-critical-quantum.html#jCp
Genesis element – Adaptation
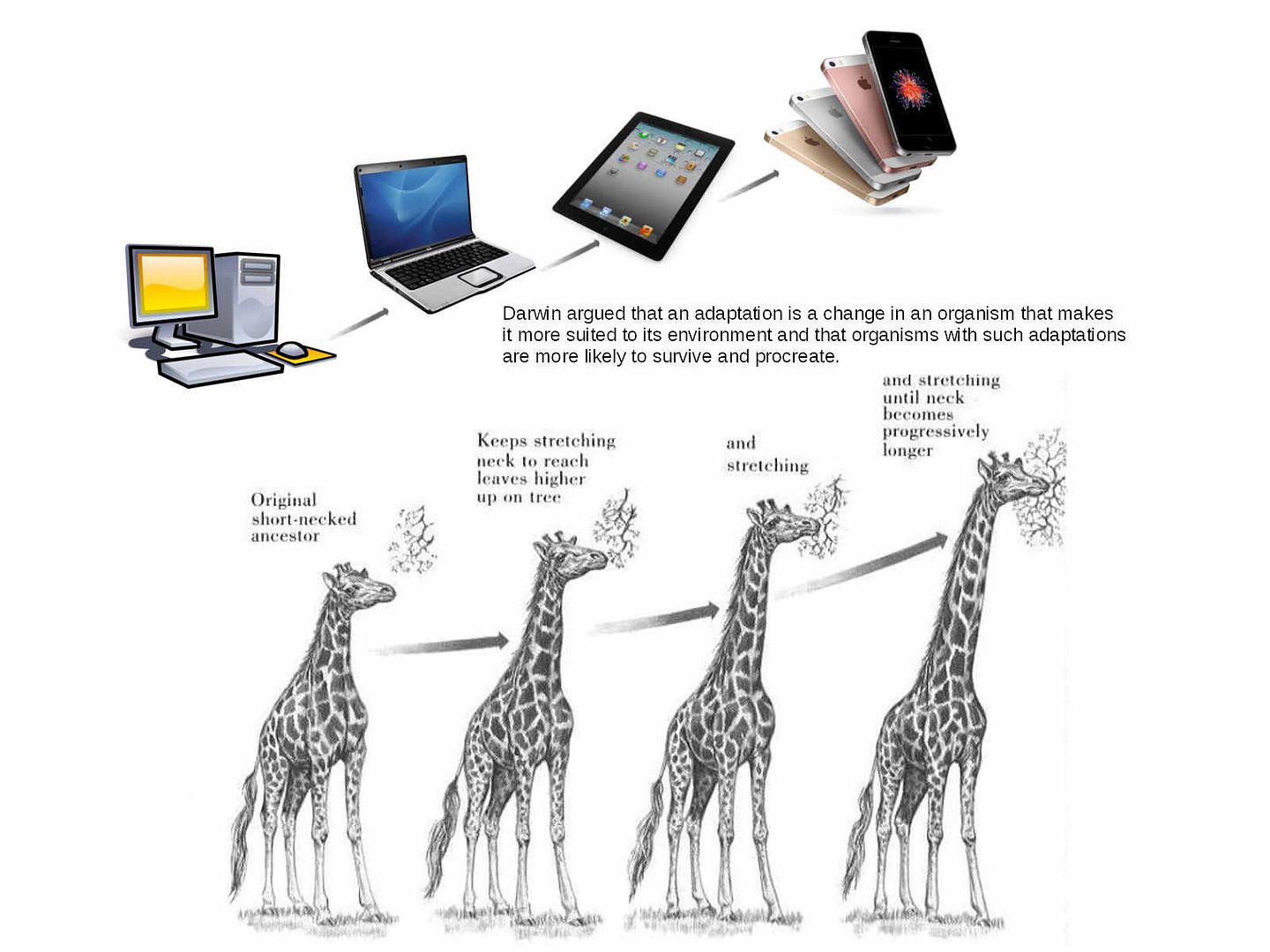
Adaptation: a characteristic that makes an organism to survive and reproduce in its environment. The adaptations are more likely to survive and procreate. Without DNA, it would be impossible to pass on adaptations, and evolution would be virtually nonexistent.
Up until now, artificial intelligence growth rapidly. 3 major elements has been established. In fact it is not mature today. However nobody know how fast developing in this area. Since some of the technologies are the intellectual proprietary. The simple we can say, …
who have privileges to governance in earth, all depends on intelligence.