Flash Player has a wide user base, and is a common format for games, animations, and graphical user interfaces (GUIs) embedded in web pages. However the trend of HTML 5 is going to replace his duty on market. Google stop running Flash display advertisement on Jan 2017. The e-newspaper (Digital journal) foreseen that the Adobe’s Flash expected to be dead and gone by 2018. However, the software vendor Adobe release Flash Player 25 on Mar 2017. Before the discussion starts, , lets go through the current market status of Flash player. Below picture show the current market position of Flash. It looks that a significant drop of the market share today.
Market position 2017
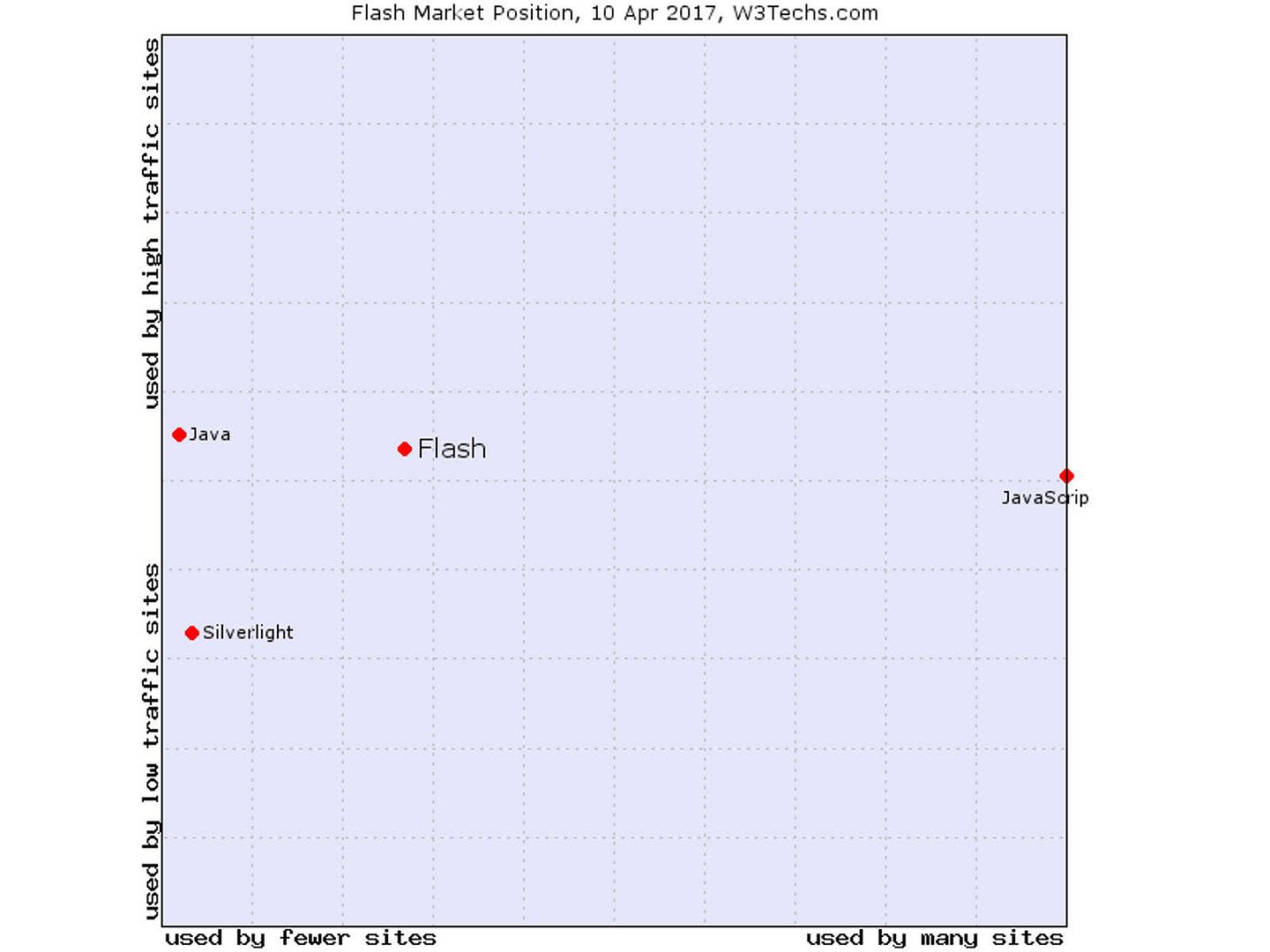
A question you may ask? If the market share of the product dropped, it is not necessary to discuss a low popularity product. But my concerns on Adobe Flash application still valid. The fact is that even though you are not going to use. However Flash Player installed on your machine have inherent risk. Ok, make it simple. Let jump to our main topic now. It is the real-time media flow protocol from Adobe.
What is the Real-Time Media Flow Protocol (RTMFP)?
The Real-Time Media Flow Protocol (RTMFP) is a communication protocol from Adobe that enables direct end user to end user peering communication between multiple instances of the Adobe® Flash® Player client and applications built using the Adobe AIR® framework for the delivery of rich, live, real-time communication.
The evolution of Adobe system design
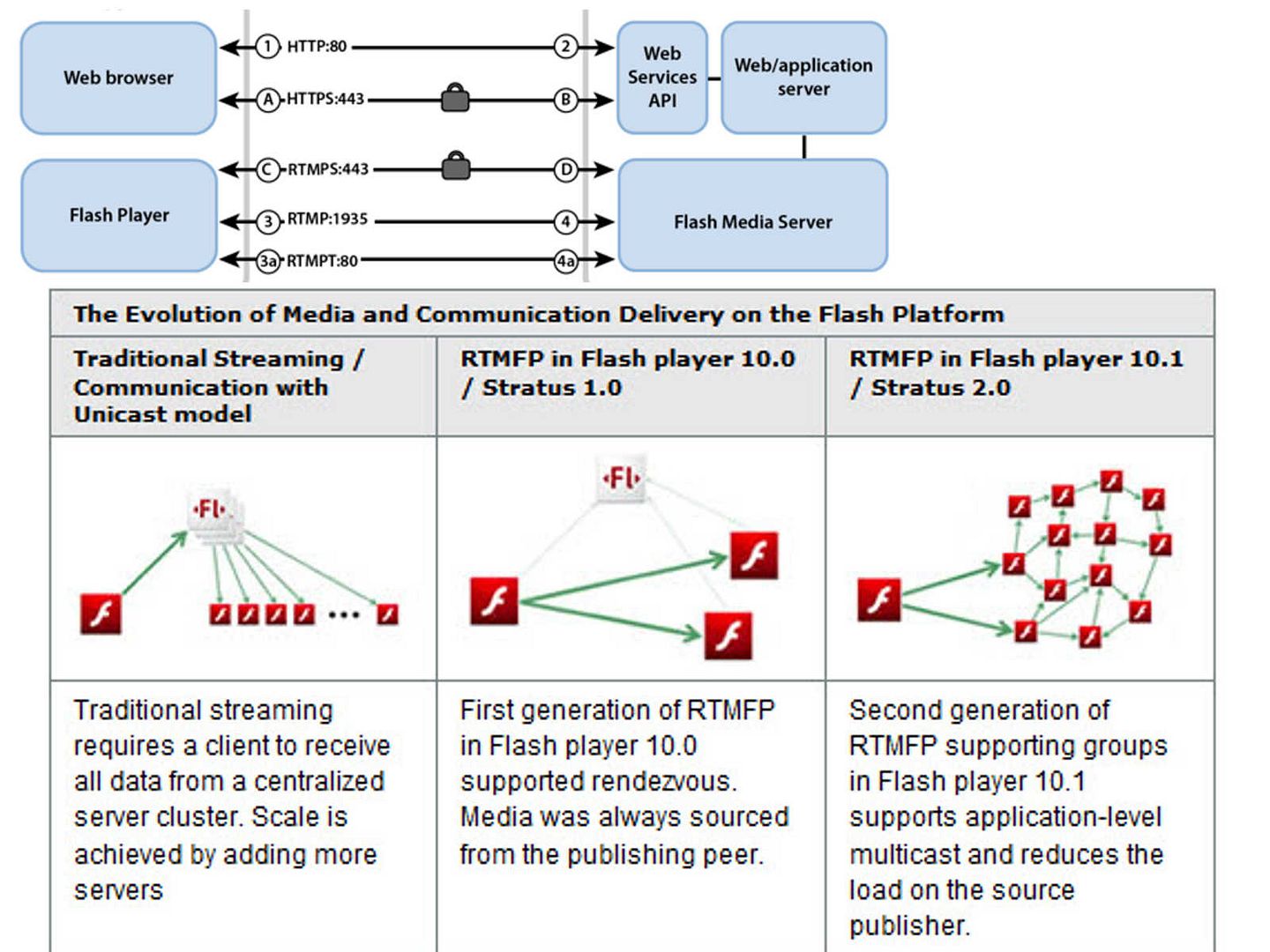
The IETF technical articles issued on Dec 2014 has following security consideration.
Cryptographic aspects of RTMFP architecture:
RTMFP architecture does not define or use a Public Key Infrastructure (PKI). Clients should use static Diffie-Hellman keys in their certificates. Clients MUST create a new certificate with a distinct fingerprint for each new NetConnection. These constraints make client identities ephemeral but unable to be forged. A man-in-the-middle cannot successfully interpose itself in a connection to a target client addressed by its fingerprint/peer ID if the target client uses a static Diffie-Hellman public key.
Servers can have long-lived RTMFP instances, so they SHOULD use
ephemeral Diffie-Hellman public keys for forward secrecy. This
allows server peer IDs to be forged; however, clients do not connect
to servers by peer ID, so this is irrelevant.
For more details on above matter, please visit IETF techincal articles https://tools.ietf.org/html/rfc7425#page-46
Our observation today
- Since RTMFP is based on UDP. UDP (User Datagram Protocol) connectionless state which decreased latency and overhead, and greater tolerance for dropped or missing packets. RTMFP supporting groups in Flash player support multicast feature. If hacker counterfeit a malicious swf format file and deploy with spear phishing hacking technique. Since it is a multicast structure and therefore it is hard to located the original source file.
2. CVE-2017-2997 exploits vulnerability in the Primetime TVSDK that supports customizing ad information. Successful exploitation could lead to arbitrary code execution. However a design weakness looks appear on TVSDK , an out-of-bound read vulnerability found by FireEye on May 2016.
3. Besides, The AVM (Action script virtual machine) implements certain core features of ActionScript, including garbage collection and exceptions, and also acts as a bridge between your code and Flash Player. The use-after-free memory feature in AVM is protect by OS system. Even though implement Address space layout randomization (ASLR) and Data Execution Prevention (DEP) but still have way by-pass by attacker. Windows 8.1 Update 3 Microsoft introduced a new exploit mitigation technology called Control Flow Guard (CFG). CFG injects a check before every indirect call in the code in order to verify if the destination address of that call is one of the locations identified as “safe” at compile time. However overwrite Guard CF Check Function Pointer with the address of a ret instruction will
let any address pass Guard CF Check Function, and thus bypass CFG.
Overall comments on above 3 items:
It looks that Flash contained fundamental design limitation, may be there are more hidden risks does not discover yet. As far as I know, law enforcement agency relies on Flash vulnerabilities to implement the surveillance program (Reference to vulnerability on 2012). My suggestion is that it is better uninstall the Flash on your web browser especially enterprise firm IT operation environment. Since Information security is a continuous program, so stay tuned, update will be coming soon!
Flash Architecture
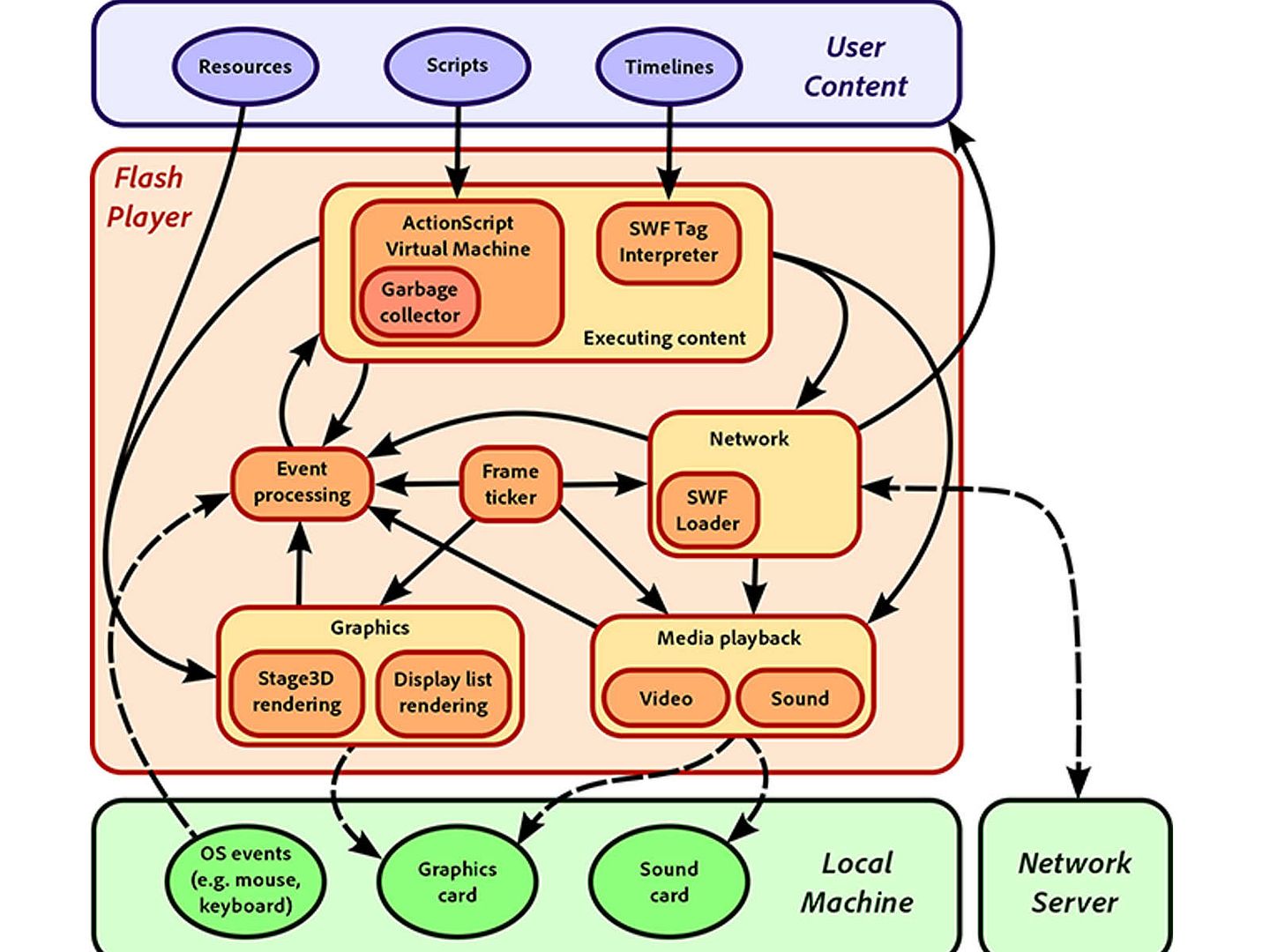
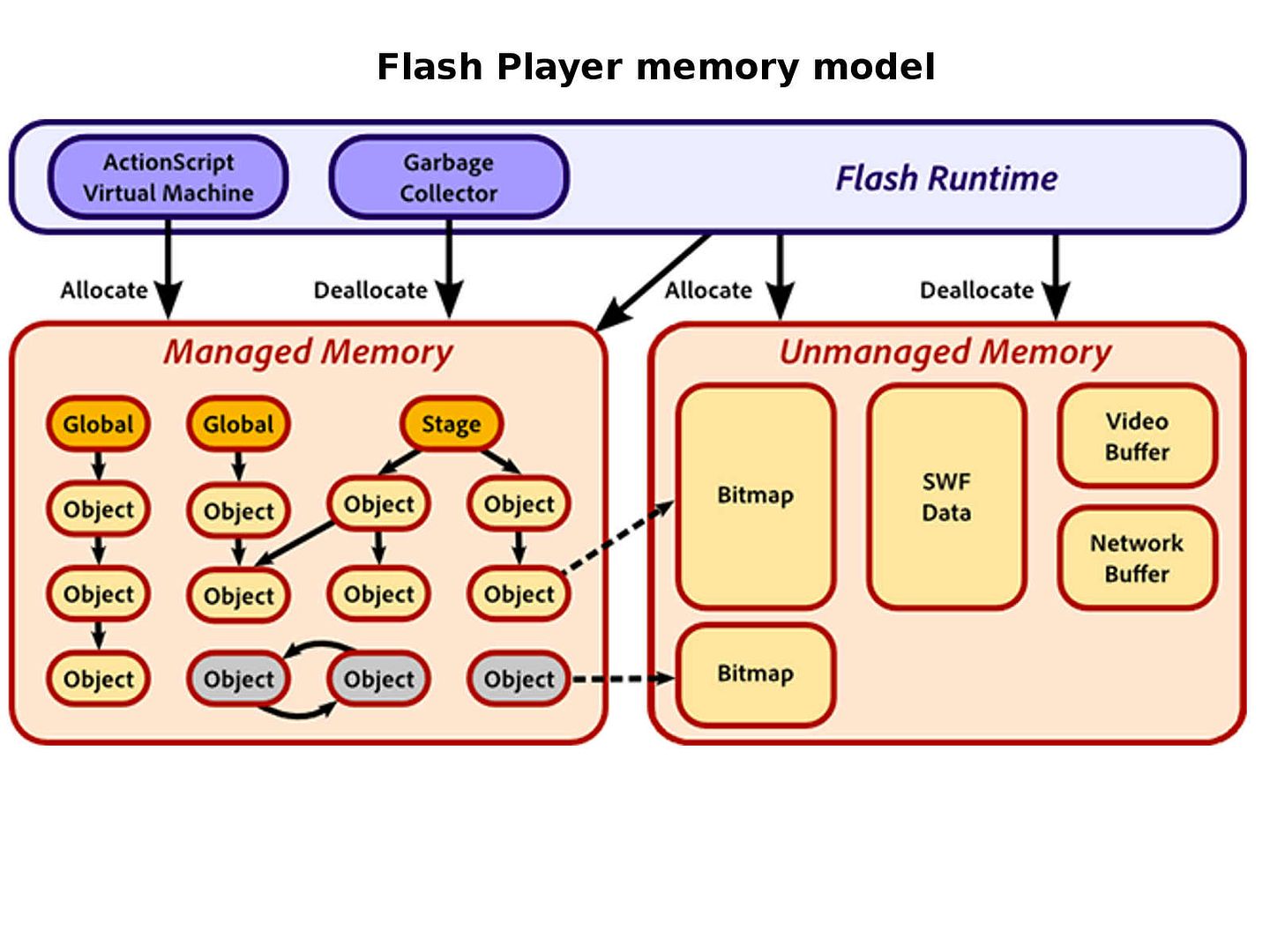
Remark: out-of-bounds definition – This typically occurs when the pointer or its index is incremented or decremented to a position beyond the bounds of the buffer or when pointer arithmetic results in a position outside of the valid memory location to name a few. This may result in corruption of sensitive information, a crash, or code execution among other things.
Application platform – Language C and C++
The chronology of attack
2012: The malicious documents contain an embedded reference to a malicious Flash file hosted on a remote server. When the Flash file is acquired and opened, it sprays the heap with shellcode and triggers the CVE-2012-0779 exploit. Once the shellcode gains control, it looks for the payload in the original document, decrypts it, drops it to disk, and executes it. Symantec detects this payload as Trojan.Pasam. The malicious files we have observed so far are contacting servers hosted in China, Korea, and the United States to acquire the necessary data to complete the exploitation. This attack is targeting Adobe Flash Player on Internet Explorer for Windows only.
2015: SWF file is used to inject an invisible, malicious iFrame
2017: (CVE-2017-2997, CVE-2017-2998,CVE-2017-2999,CVE-2017-3000,CVE-2017-3001,CVE-2017-3002 & CVE-2017-3003)
A buffer overflow vulnerability that could lead to code execution (CVE-2017-2997).
Memory corruption vulnerabilities that could lead to code execution (CVE-2017-2998, CVE-2017-2999).
Random number generator vulnerability used for constant blinding that could lead to information disclosure (CVE-2017-3000).
unpatch vulnerabilities lead to code execution (CVE-2017-3001, CVE-2017-3002, CVE-2017-3003)