Security services provider alert the IT world that malware might infiltrate to their infrastructure facilities. However their cyber defense mechanism looks fall into asleep. So strange? Over 140 enterprises in 40 countries affected. Dubbed that fileless or invisible cyber attack common are in three types. They are memory resident, Rootkits and Windows registry. Refer to anti-virus expert interpretation, It evades detection by reducing or eliminating the storage of any binaries on disk and instead hides its code in the registry of a compromised host. The naming convention base on above criteria. Can you still remember W32,Duqu malware? He is the descendants of Stuxnet. We all knew Stuxnet is the famous malware which responsible for causing substantial damage to Iran’s nuclear program identify in 2010. Regarding to the technical articles, Stuxnet and W32.Duqu specification equivalent fileless malware algorithm. Coincidentally, the fileless malware target Windows OS . But this matter would like to bring to our attention is the infectious media. Nowadays enterprise company installed advanced cyber defense facilities. The detective control can effectively quarantine the malicious network activities once infected device going to download the payload file. Such malware download action nearly 99% is a execution file. And therefore no difficulties on malware detector on this direct approach attack today.
Refer to analysis report, W32.Duqu make use of true type font as a infection media. The first time I heard this infection technique looks surprise me. We understand now that a true type font can contain a malware then directly exploits vulnerabilities in the Windows Kernel. The attack method was that crafted True Type Font (TTF) files, such TTF file allowed the malware to escape a user-mode sandboxed environment implemented by the Microsoft Word process and compromise the host. Since nobody else discover more details information on CVE-2011-3402 till exploration kit open the secret in Oct 2012.
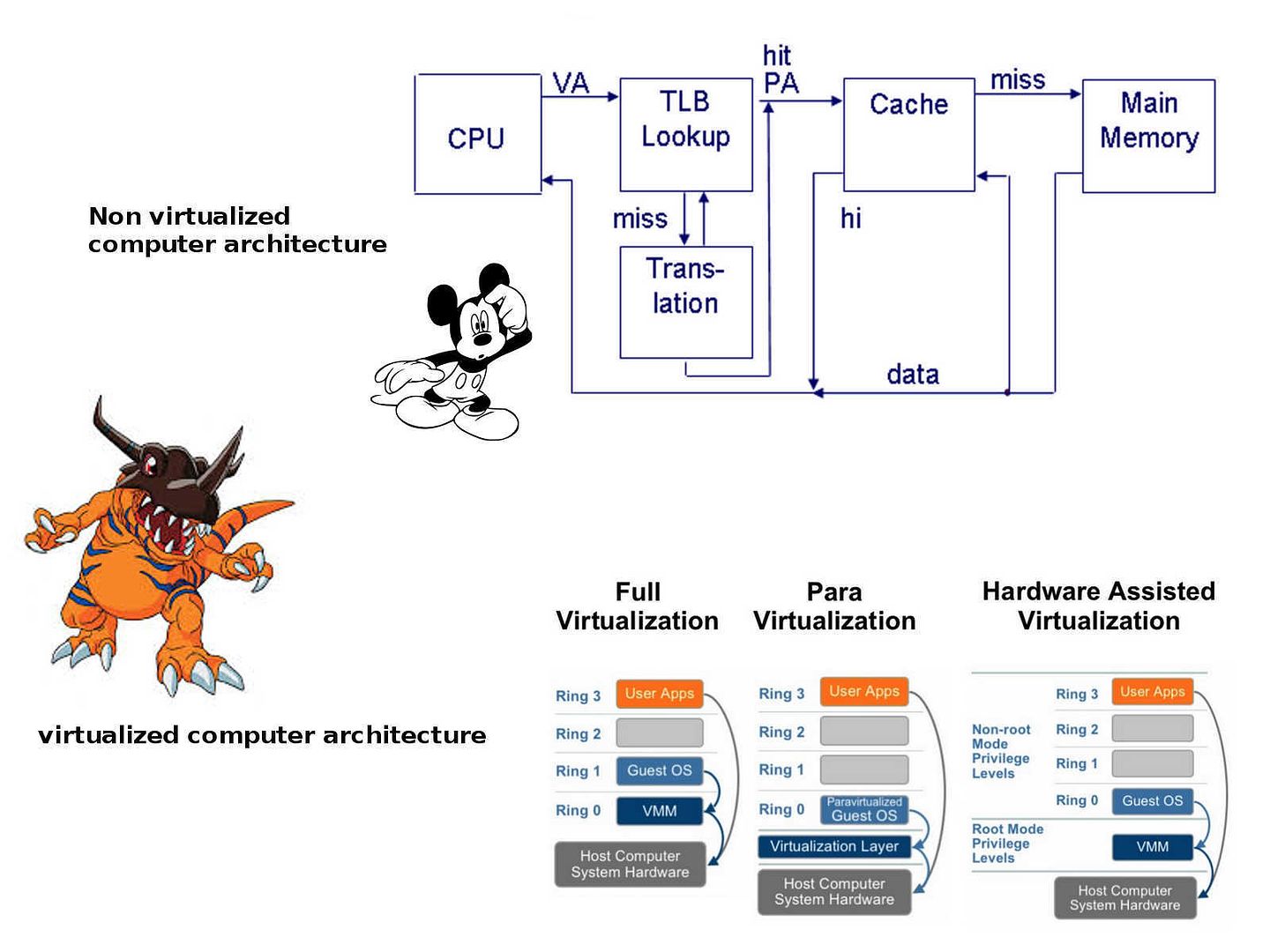
Security Experts found win32k.sys truly a instigator. They dig out that Microsoft products most likely is the major target of such attack. From logic point of view, the users coverage of Microsoft is the largest in the world. Since the objective of Stuxnet malware outbreak targets Iraq nuclear facilities Microsoft operating system workstation. The security expert point out the design weakness of win32k.sys. Details is shown as below:
- Windows executes true type font programs
- Rendering bitmaps
- Win32K operate in Kernel area (Ring 0)
Remark: A kernel-mode object database (part of win32k.sys) that marshals commands from the application to the composition engine.
As time goes by, Google Project Zero summarizes all the details and related information.
https://googleprojectzero.blogspot.com/2015/07/one-font-vulnerability-to-rule-them-all.html
https://googleprojectzero.blogspot.com/2016/06/a-year-of-windows-kernel-font-fuzzing-1_27.html
https://googleprojectzero.blogspot.de/2016/07/a-year-of-windows-kernel-font-fuzzing-2.html
Vulnerabilities relate to win32k.sys and True type font looks like a never ending story. See below table break down list for reference.
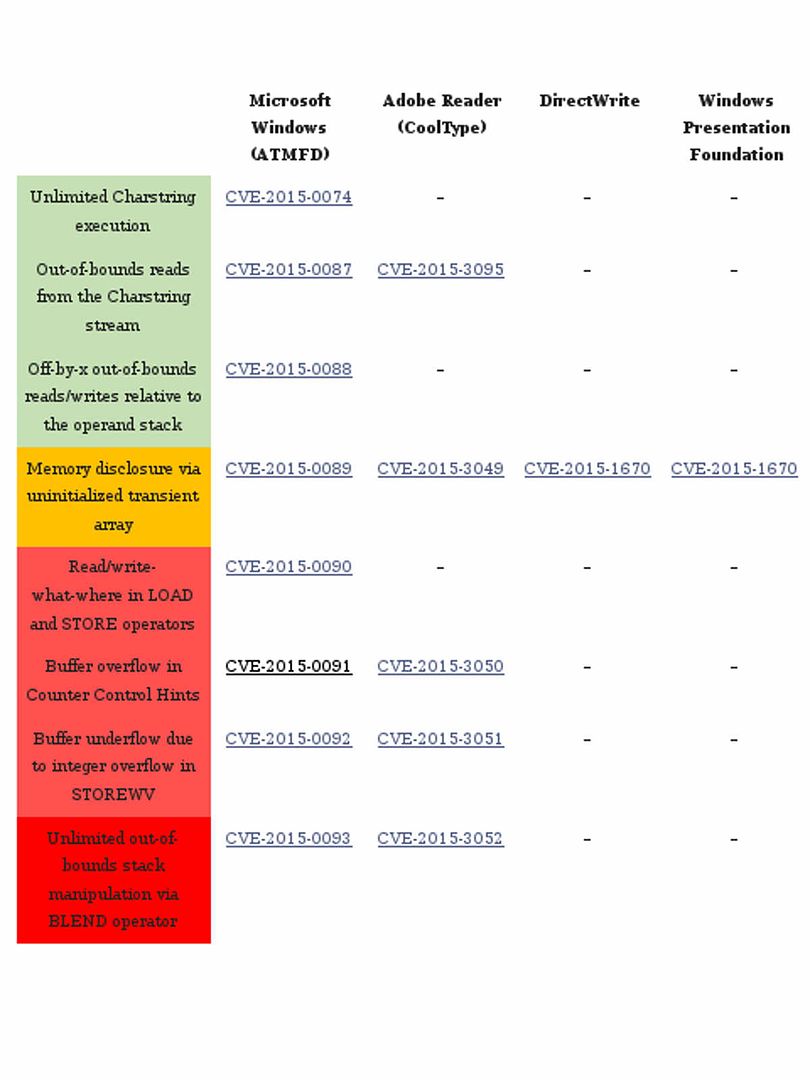
Remark: TrueType fonts (made by Microsoft) live in your windows fonts folder.
The BLEND vulnerability (CVE-2015-0093, CVE-2015-3052)
Impact Type: Allows unauthorized disclosure of information; Allows unauthorized modification; Allows disruption of service
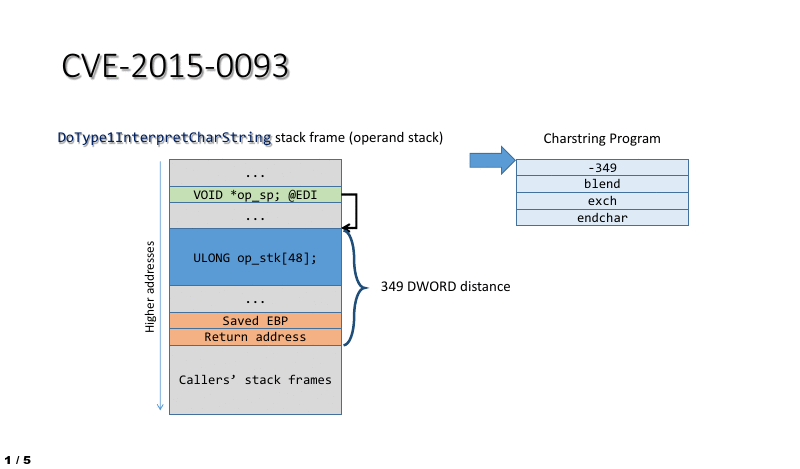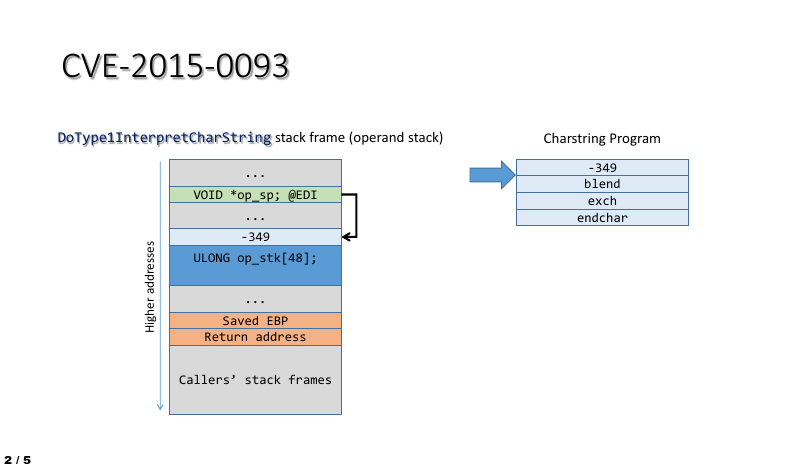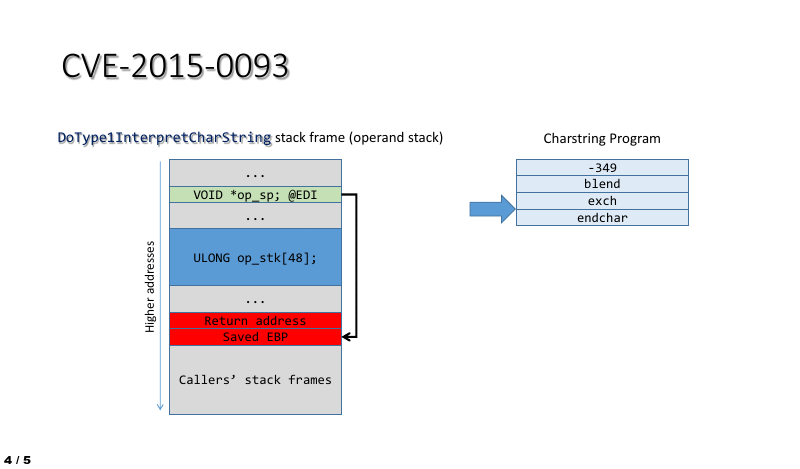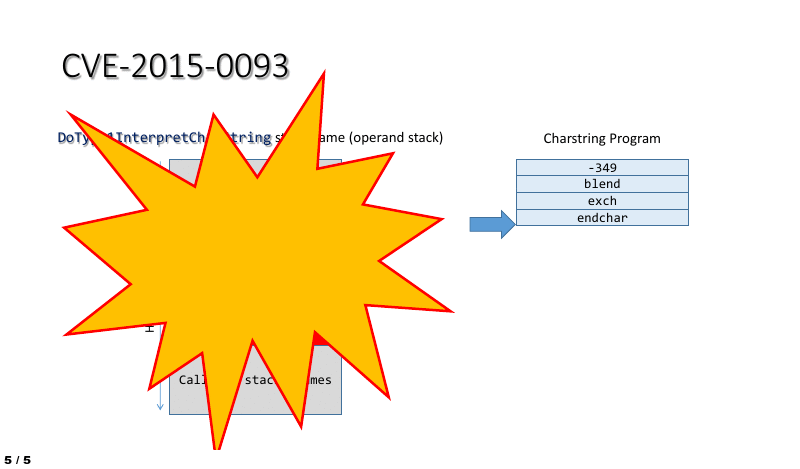
- CVE-2016-3029 confirm that vulnerability allows remote attackers to bypass the ASLR protection mechanism via unspecified vectors, aka “True Type Font Parsing Information Disclosure Vulnerability.” The ASLR (Address space layout randomization) is the major protection feature on virtual machine especially VMware. In the sense that the specify vulnerability like flooding. It now effect virtual machine environment.
- True Type Font Parsing Elevation of Privilege Vulnerability – CVE-2016-7182. The vulnerability is in the cjComputeGLYPHSET_MSFT_GENERAL function of the Win32k.sys system module. This is the design limitation due to improper processing of crafted TrueType fonts (TTF). The vulnerability is due to improper handling of objects within memory.
We did analysis tones of documents of vulnerabilities on True type font (TTF) so far. May be you have question? What is the overall impact of TTF vulnerability today? Does all the vulnerabilities has been fixed? We are all on virtual machine environment. Is there any impact on virtual machines once a single VM compartment compromised?
- What is the overall impact of TTF vulnerability today?
It looks that true type font design limitation integrate with Graphics display mechanism on computer hardware causes never ending vulnerabilities. See below graphic state summary table, it shown that a auto flip mechanism will be apply to graphics state variable.
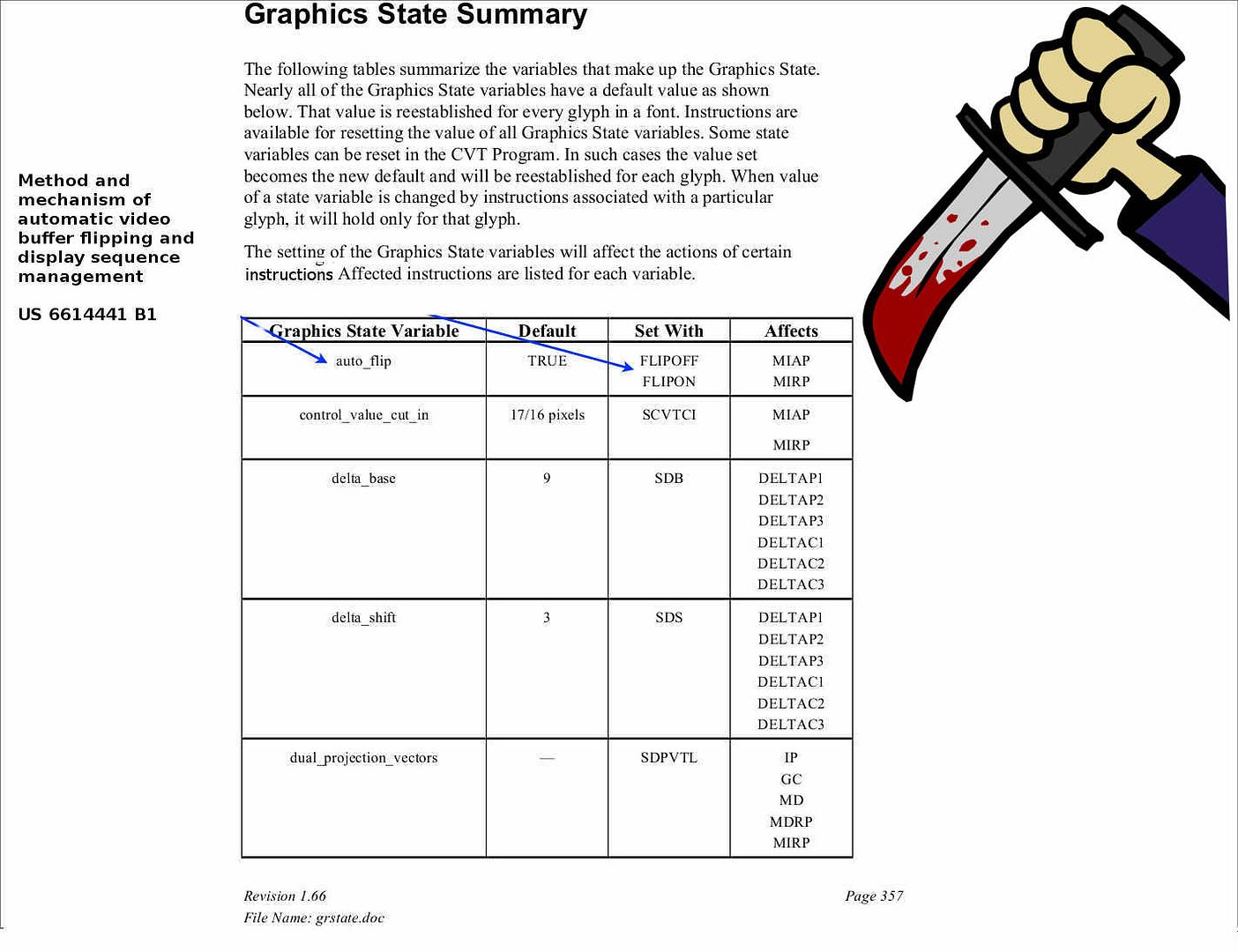
- a bank of shift registers arranged to synchronize the video capture parameters from video capture engine and temporarily store those parameters; and
- a control block arranged to control proper “flipping” events based on the sequence of input video capture parameters from the video capture engine registered in the shift registers, said control block comprising a Truth Table for maintaining predetermined display setting values for different auto-flip operations based on the sequence of the video capture parameters from the video capture engine and overlay control signals from the video overlay engine.
It looks that above issues are the fundamental problem of hardware display architecture. Since memory address of temporarily store memory no bounds checking. And therefore malware can make use of this vulnerability. So the impact of TTF (Ture type font) vulnerabilities are still inherent today.
2. Does all the vulnerabilities has been fixed?
Refer to above information details, it looks that it is hard to draw into conclusion today!
3. We are all on virtual machine environment. Is there any impact on virtual machines once a single VM compartment compromised?
CVE-2016-3029 confirm that vulnerability allows remote attackers to bypass the ASLR protection mechanism via unspecified vectors, aka “True Type Font Parsing Information Disclosure Vulnerability.” The ASLR (Address space layout randomization) is the major protection feature on virtual machine especially VMware. In the sense that the specify vulnerability like flooding. It now effect virtual machine environment.
Predictions:
I strongly believed that hackers or governance enforcement team will relies on these vulnerabilities to develop different malware to satisfy their objective. Stay tune!
Comments:
Some test I didn’t complete yet. If you are interested of this topic, you can drill down a little bit more. The related hints might found on visual studio documents. Related hints displayed as below:
Refer to visual studio documentation, The ushort keyword indicates an integral data type that stores values according to the size and range (0 to 65,535)……….