.jpg)
Preface: Vendor insists to fix the cyber security weakness of CVE-2020-27929 & CVE-2020-27930. However, this iOS upgrade action was caused the specify iPhone product encounter operation difficulties especially 6s.
Observation 1: On 5th November, 2020, apple implement security update to enhance the cyber security protection on their products. This enhancement including an remediation action to two different vulnerabilities. However quite a lot of user including myself encountered technical problem. For instance, the touch screen service on iPhone 6s suspended intermittent.
Observation 2: When I connect my iPhone 6s to my notebook. The touch screen service malfunction problem not been happen in frequent But still occur intermittent. The symptom looks that it is related to a daemon (com.apple.mtmergeprops.plist). Do you think this problem cause by missing a step to check ios device chip model (A9 or a10). Whereby causes memory mapping problem occurs.
Reference: Apple security updates on 5th Nov 2020 – https://support.apple.com/en-us/HT211940
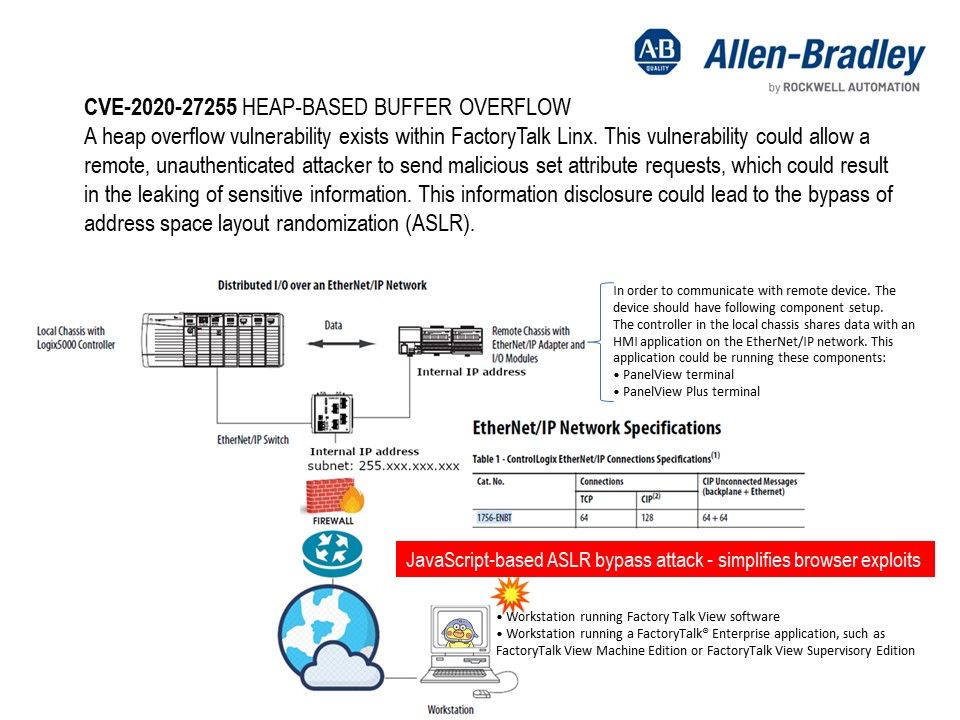
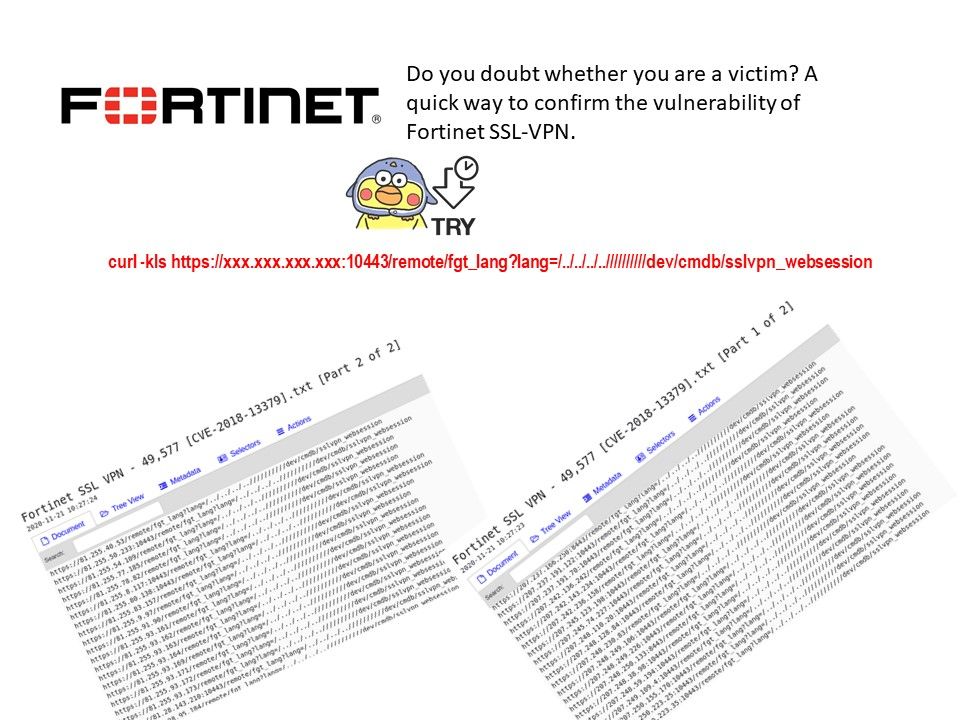
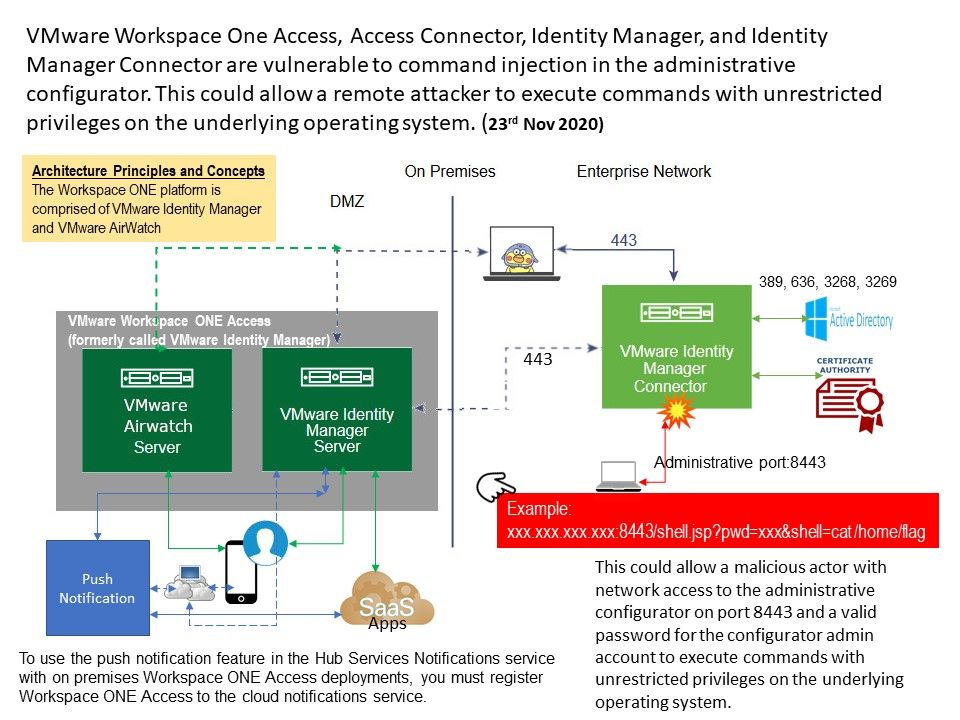
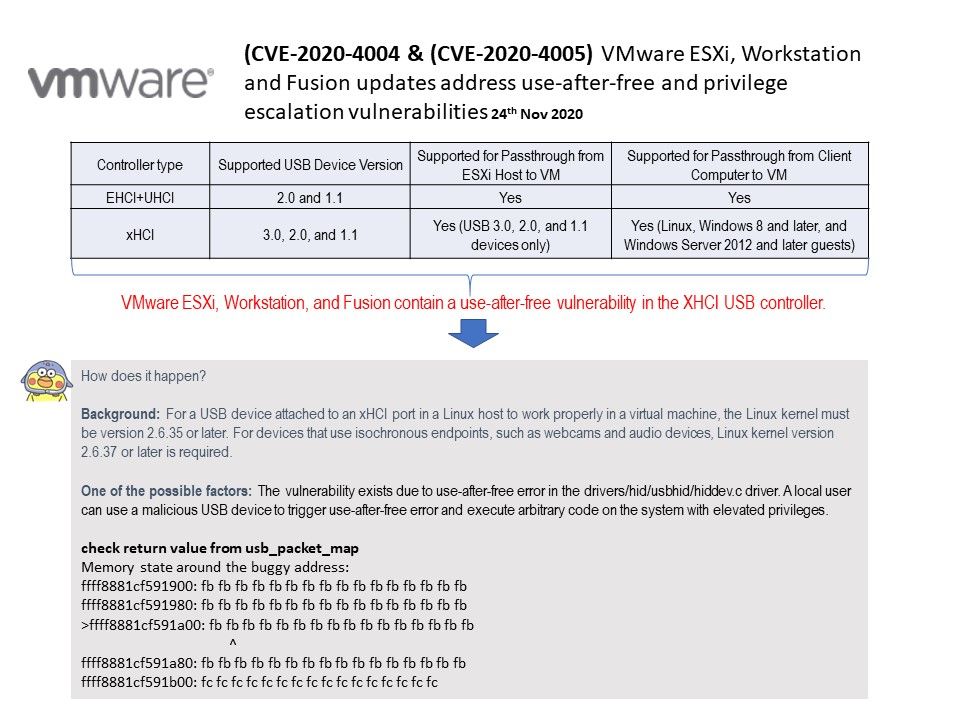
.jpg?width=1920&height=1080&fit=bounds)