Preface: Since the software device will be customized by the manufacturer. So-called OS and even web server hardening will be done by the manufacturer. If the web server and SQL packages contain design flaws (so-called multiple vulnerabilities). Sometimes there is no workaround. Need to be patched. But manufacturers of cyber defense utilities were quick to react. Their product design weaknesses will be fixed immediately.
Background: By w3techs.com statistics, Apache is used by 31.4% of all the websites whose web server we know. What is SonicWall Global Management System?
SonicWall Global Management System (GMS) solves these challenges. GMS integrates management and monitoring, analytics, forensics and audit reporting. This forms the foundation of a security governance, compliance and risk management strategy.
Security Focus: CVE-2023-34124 – The authentication mechanism in SonicWall GMS and Analytics Web Services had insufficient checks, allowing authentication bypass.
Tomcat become web server of GMS/Analyze by design. It can straight seen as administrator front end console/dashboard. When vulnerabilities occurs in Tomcat. It is hard to avoid burden the downstream services.
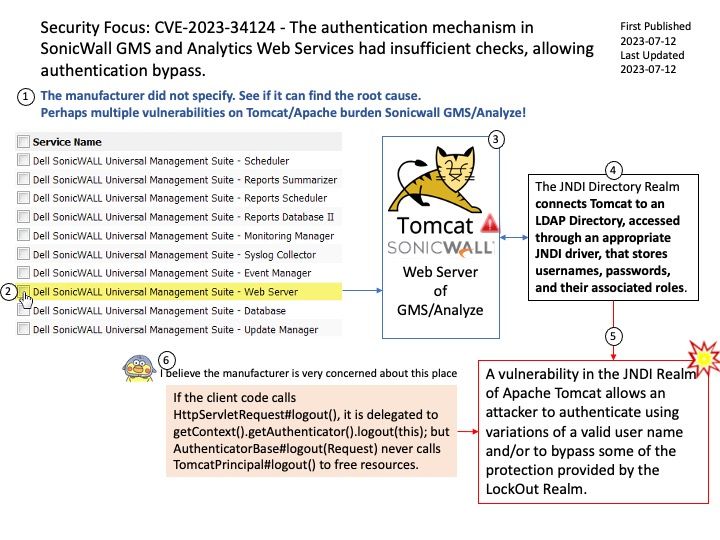
The manufacturer did not specify. See if it can find the root cause.
Perhaps multiple vulnerabilities on Tomcat/Apache burden Sonicwall GMS/Analyze!
Below is my observation:
A vulnerability in the JNDI Realm of Apache Tomcat allows an attacker to authenticate using variations of a valid user name and/or to bypass some of the protection provided by the LockOut Realm.
I believe the manufacturer is very concerned about this place. If the client code calls HttpServletRequest#logout(), it is delegated to getContext().getAuthenticator().logout(this); but AuthenticatorBase#logout(Request) never calls TomcatPrincipal#logout() to free resources.
Vulnerability details: SonicWall has identified four critical vulnerabilities (CVE-2023-34124, CVE-2023-34133, CVE-2023-34134, and CVE-2023-34137) that could allow an unauthenticated attacker to bypass authentication and potentially access Sensitive information on vulnerable websites. An on-prem system running GMS 9.3.2-SP1 or earlier and Analytics 2.5.0.4-R7 or earlier.
Official announcement: For details, please refer to the link – https://www.sonicwall.com/support/notices/urgent-security-notice-sonicwall-gms-analytics-impacted-by-suite-of-vulnerabilities/230710150218060/