Preface: AI-powered systems analyse the severity of the vulnerability, potential impact, and exploitability and prioritise patches based on the criticality of the vulnerability. Perhaps AI contains self diagostic and do remedy by himself!
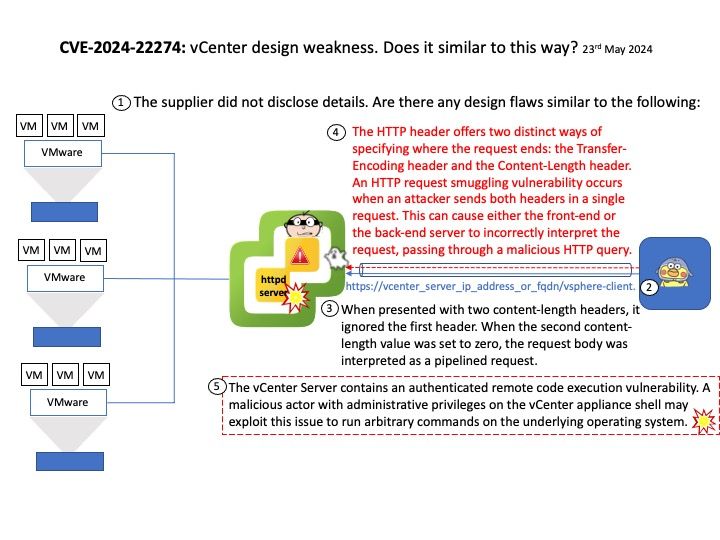
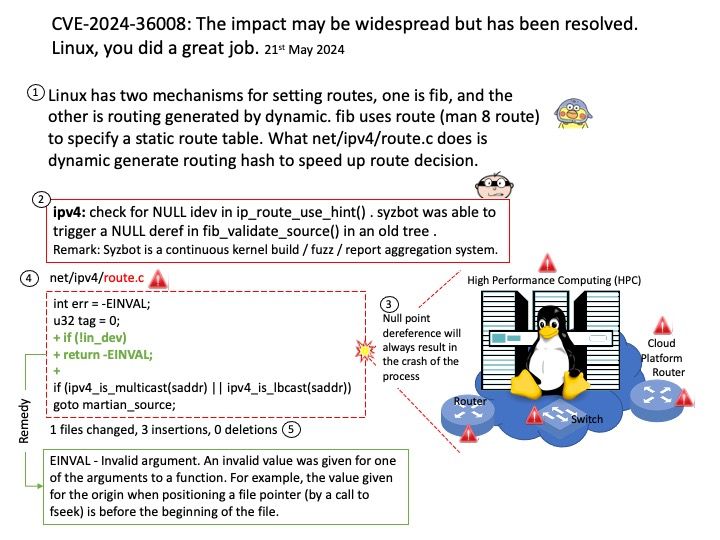
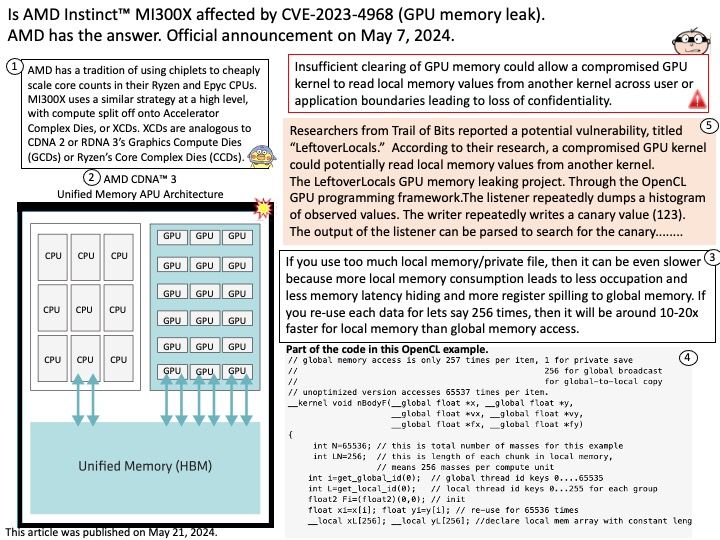
Background: An open-source software that helps standardize model deployment and delivers fast and scalable AI in production.
Vulnerability details:
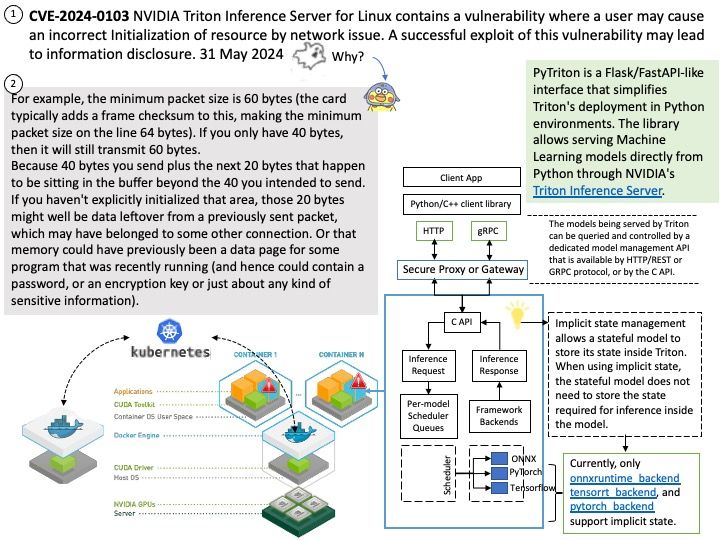
CVE-2024-0103 Information disclosure
NVIDIA Triton Inference Server for Linux contains a vulnerability where a user may cause an incorrect Initialization of resource by network issue. A successful exploit of this vulnerability may lead to information disclosure.
Ref: For example, the minimum packet size is 60 bytes (the card typically adds a frame checksum to this, making the minimum packet size on the line 64 bytes). If you only have 40 bytes, then it will still transmit 60 bytes.
Because 40 bytes you send plus the next 20 bytes that happen to be sitting in the buffer beyond the 40 you intended to send.
If you haven’t explicitly initialized that area, those 20 bytes might well be data leftover from a previously sent packet, which may have belonged to some other connection. Or that memory could have previously been a data page for some program that was recently running (and hence could contain a password, or an encryption key or just about any kind of sensitive information).
Official details: For detail, please refer to link – https://nvidia.custhelp.com/app/answers/detail/a_id/5546