Preface: Geometric progression up growth in net meeting software product recently because of COVID-19 effect.
Background: We are all concerning of privileges escalation vulnerability. Recap OS vulnerability in past impact Zoom product. The GHOST vulnerability trigger “buffer overflow” bug that affects the gethostbyname () and gethostbyname2 () function calls in the glibc library. The vulnerability could allow remote attackers who could execute arbitrary code with the privileges of the user running the application to invoke any of these functions.
Which components of Zoom may be affected?
You have installed a meeting connector, virtual room connector, or phone connector / gateway that is running.
CentOS Linux versions 5.x, 6.x and 7.x
Remedy: yum update glibc
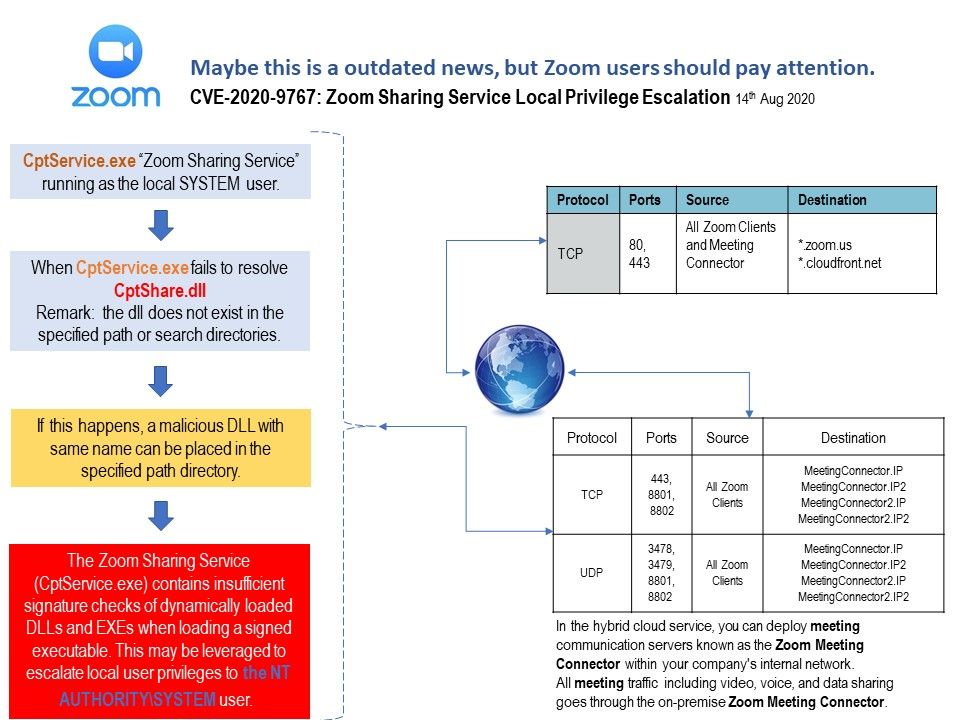
Recently News: In June 10, 2020 (about 4 months ago). Found that Zoom Sharing Service (Cptservice[.]exe) contains insufficient signature checks of dynamic loaded DLLs and EXEs when loading a signed executable. Such design weakness allow an attacker who had local access to a machine on which the service was running with elevated privileges to elevate their system privileges as well through use of a malicious DLL. NVD Published this vulnerability on 14th Aug 2020. Perhaps quite a lot of users already received alert. For those who do not know. You should upgrade the software immediately.
Remedy: https://support.zoom.us/hc/en-us/articles/360044350792-Security-CVE-2020-9767


.jpg?width=1920&height=1080&fit=bounds)