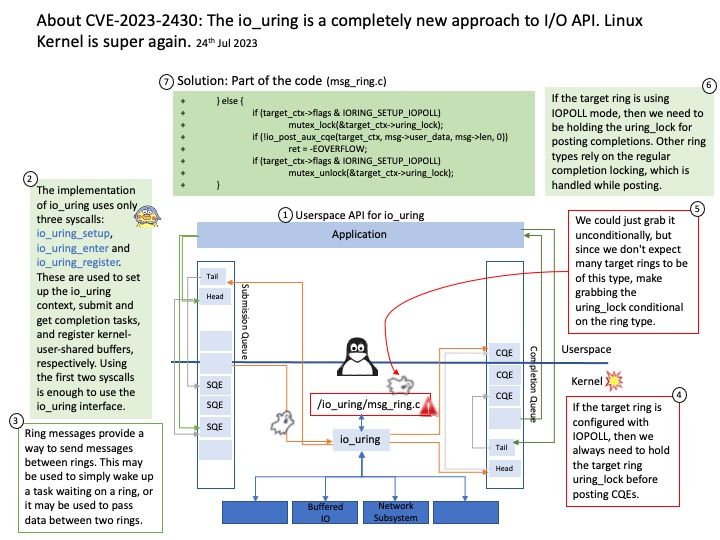
Preface: How does IO uring work? It works by creating two circular buffers, called “queue rings”, for storage of submission and completion of I/O requests, respectively. For storage devices, these are called the submission queue (SQ) and completion queue (CQ).
Background: io_uring can handle various I/O related requests. for example:
- File related: read, write, open, fsync, fallocate, fadvise, close
- Network related: connect, accept, send, recv, epoll_ctl
- Etc…
How io_uring is implemented in the kernel? io_uring has two options when it is created, corresponding to the different ways io_uring handles tasks:
- After turning on IORING_SETUP_IOPOLL, io_uring will use polling to perform all operations.
- After enabling IORING_SETUP_SQPOLL, io_uring will create a kernel thread dedicated to harvesting tasks submitted by users.
Vulnerability details: A vulnerability was found due to missing lock for IOPOLL flaw in io_cqring_event_overflow() in io_uring[.]c in Linux Kernel. This flaw allows a local attacker with user privilege to trigger a Denial of Service threat.
Official announcement: For details, please refer to link – https://nvd.nist.gov/vuln/detail/CVE-2023-2430