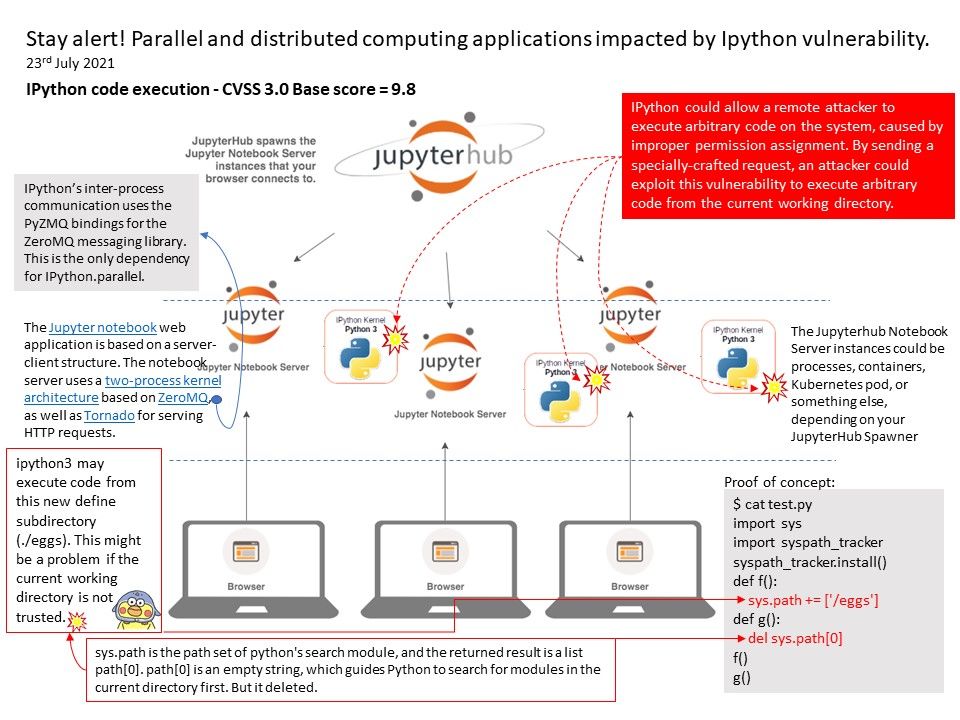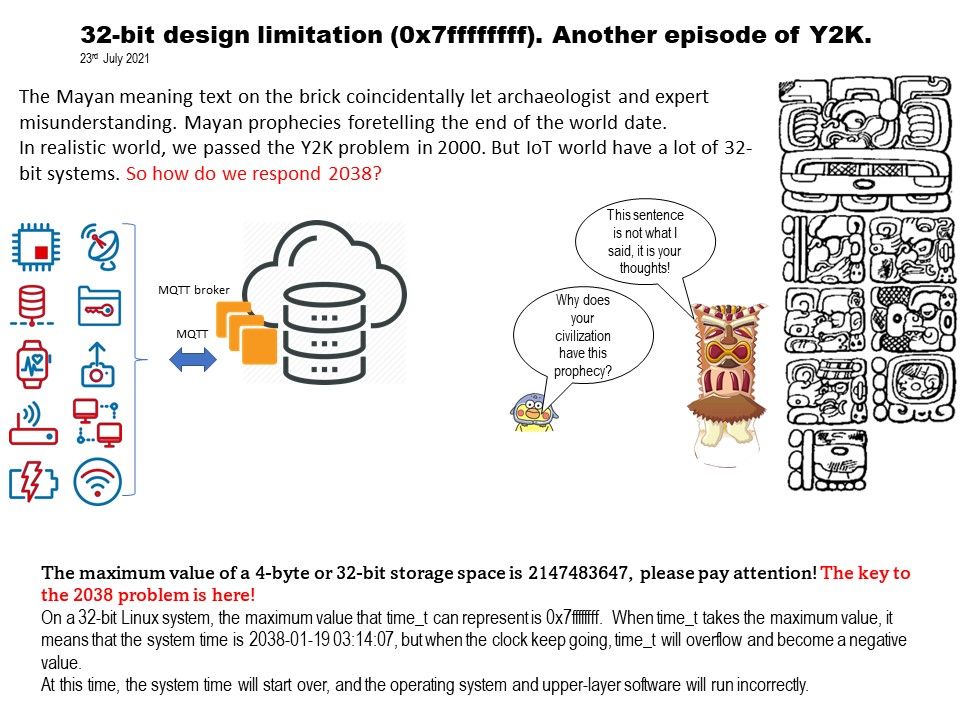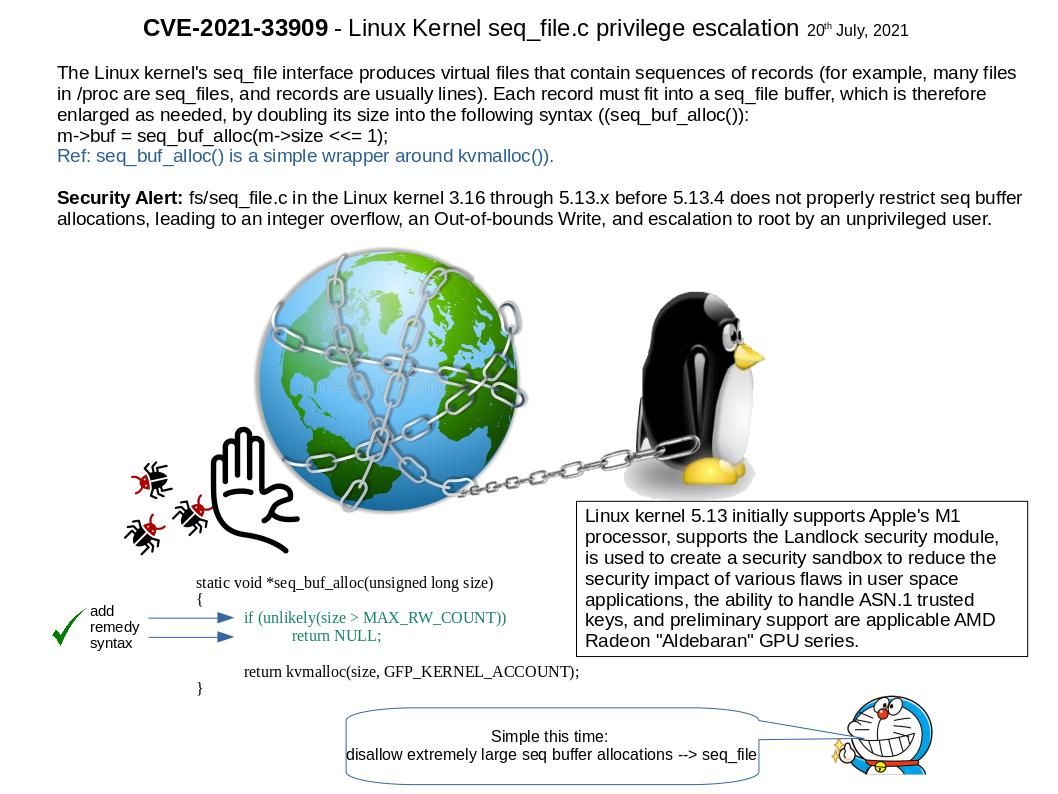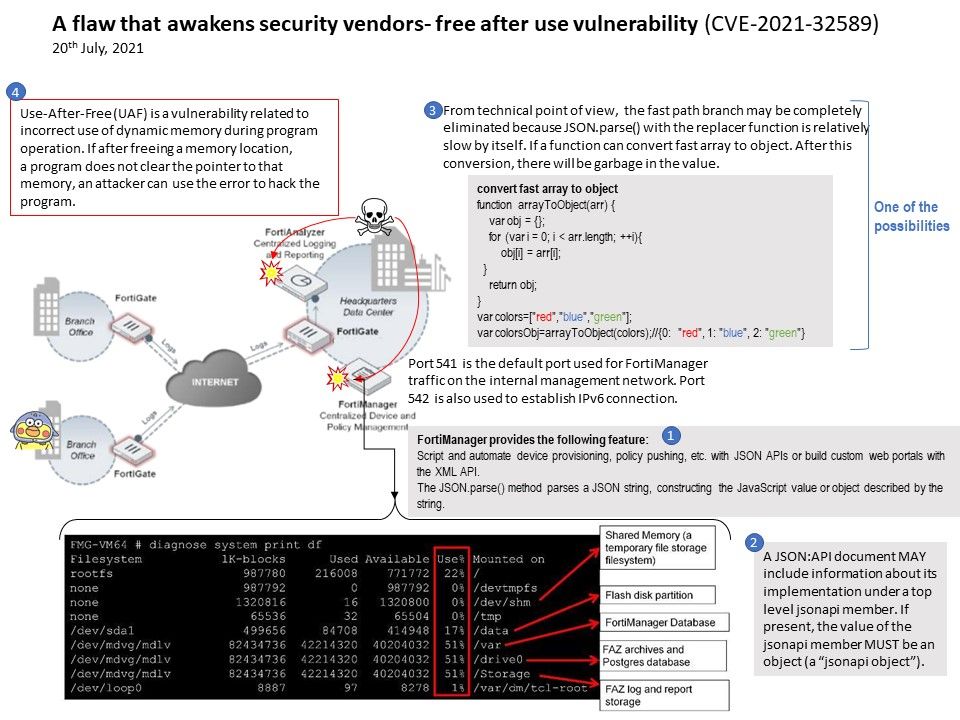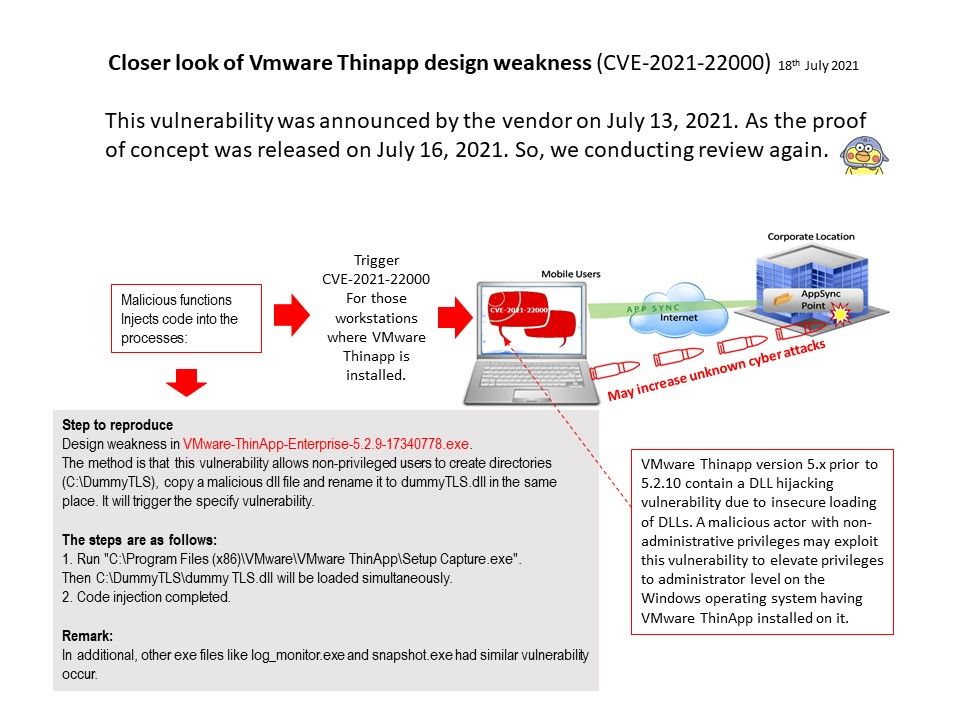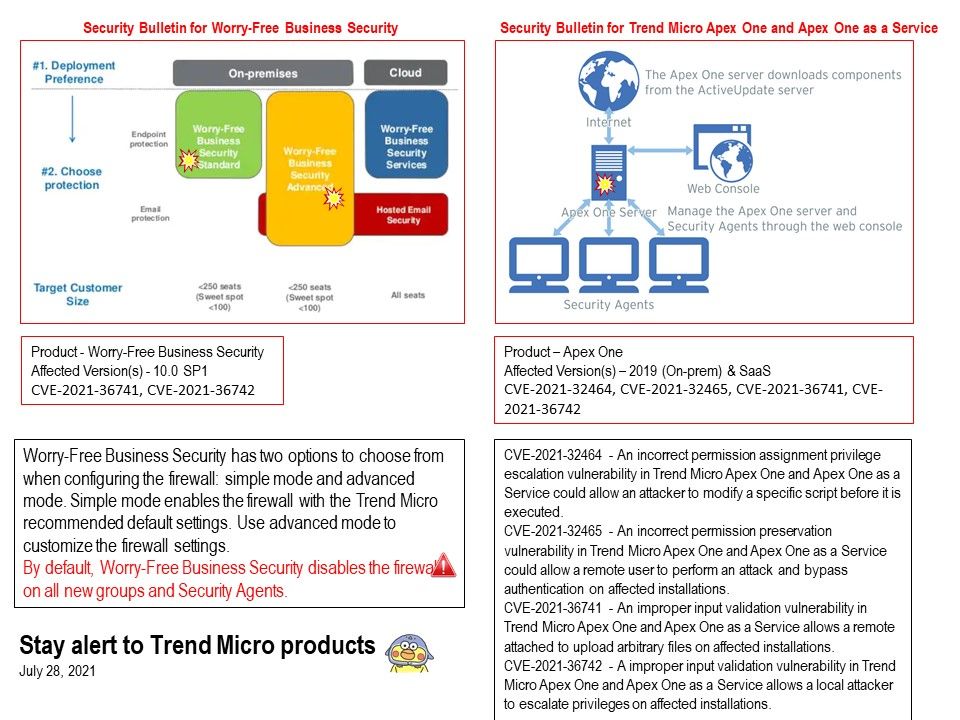
Preface: In order to expand business development, software products sometimes use similar engineering designs. When vulnerabilities occur, their effects seem to be interrelated.
Privilege Escalation Attack Techniques: A low-privileged process from being escalated via a token stolen from a process with greater privileges. This technique is often used in tandem with another vulnerability to successfully deliver and run an attacker’s malicious code with system permissions.
Perhaps attacker not use this way now. But in past, Scheduled tasks can also be used to bypass User Account Control (UAC) and escalate privileges, when misusing system actions such as antivirus update for example. As this command is marked with auto-elevating, it will run with elevated privileges without prompting the user through UAC. The key is that it uses a user controlled environment variable as part of the path, which can be manipulated.
Vulnerability details:
CVE-2021-32464 – An incorrect permission assignment privilege escalation vulnerability in Trend Micro Apex One and Apex One as a Service could allow an attacker to modify a specific script before it is executed.
CVE-2021-32465 – An incorrect permission preservation vulnerability in Trend Micro Apex One and Apex One as a Service could allow a remote user to perform an attack and bypass authentication on affected installations.
CVE-2021-36741 – An improper input validation vulnerability in Trend Micro Apex One and Apex One as a Service allows a remote attached to upload arbitrary files on affected installations.
CVE-2021-36742 – A improper input validation vulnerability in Trend Micro Apex One and Apex One as a Service allows a local attacker to escalate privileges on affected installations.
Remedy by vendor:
Security Bulletin for Worry-Free Business Security – https://success.trendmicro.com/solution/000287820
Security Bulletin for Trend Micro Apex One and Apex One as a Service – https://success.trendmicro.com/solution/000287819
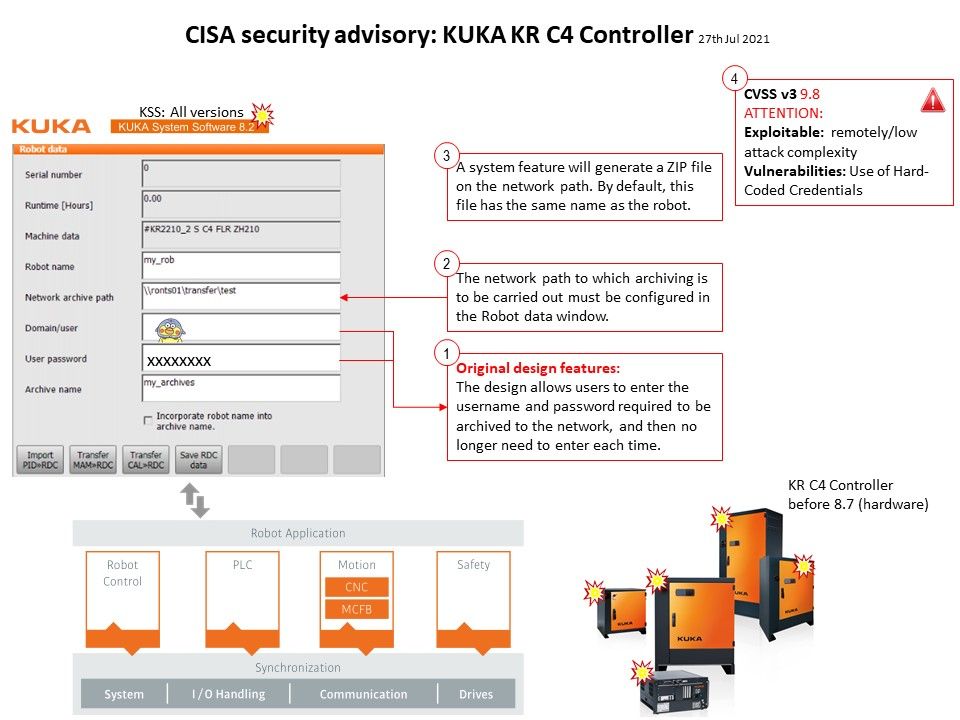
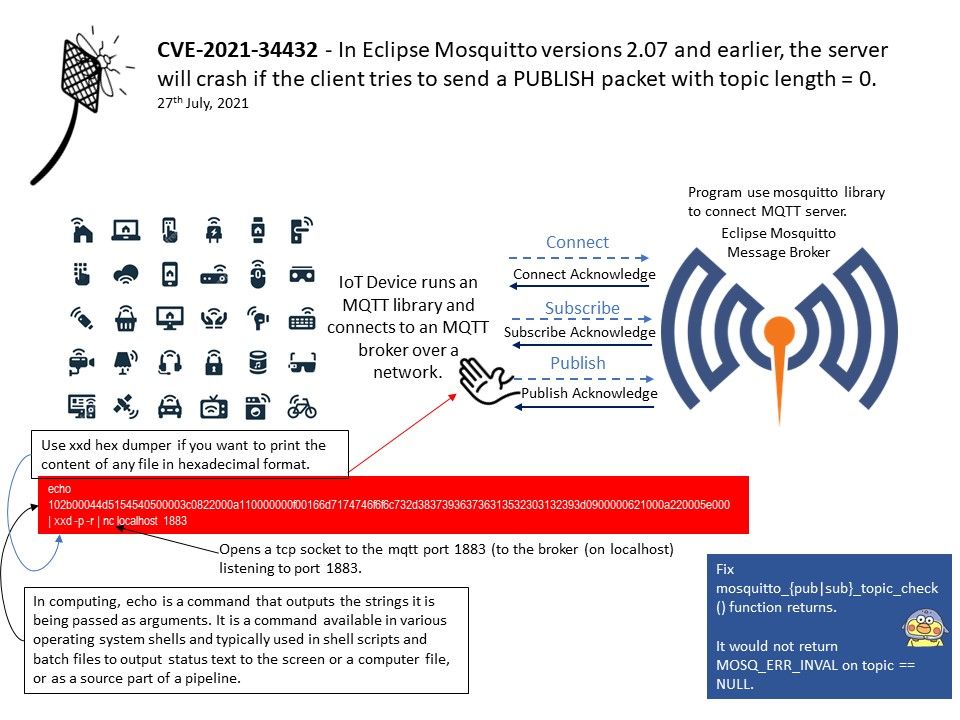
.jpg?width=1920&height=1080&fit=bounds)