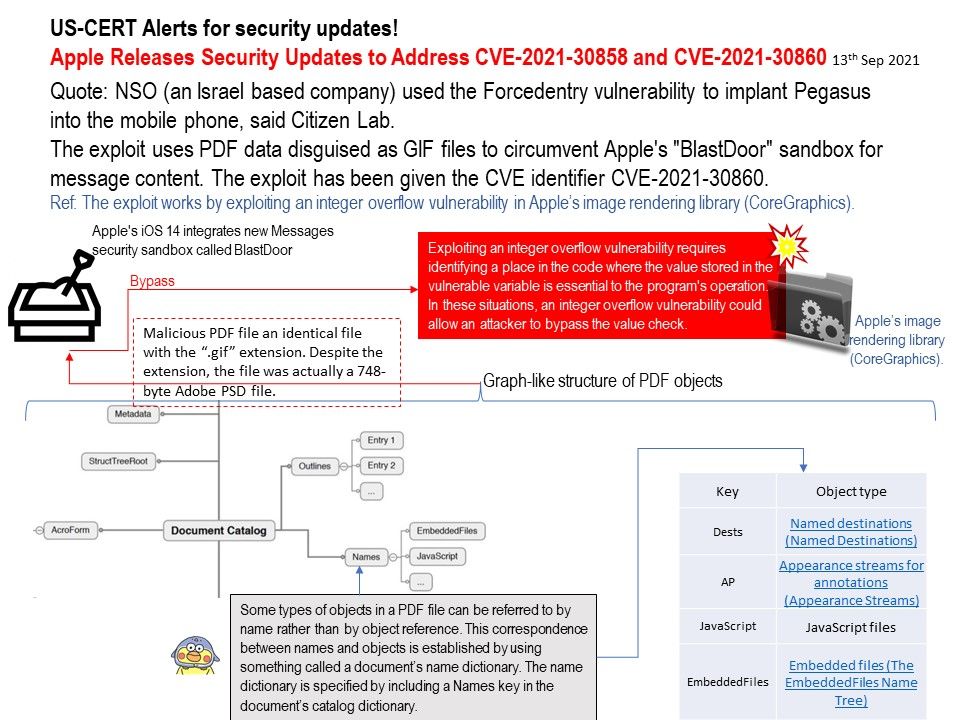
Preface: These aren’t objects in the “ object-oriented programming” sense of the word; instead, they are the building blocks on which PDF stands. There are nine types of objects: null, Boolean, integer, real, name, string, array, dictionary, and stream.
Background: The Pegasus spy program created by NSO uses a zero-day vulnerability in Apple’s operating system to fear entering the iPhone. Apple’s mobile phone nation has urgently updated all operating system platforms affected by the vulnerability.
Vulnerability details: The exploit uses PDF data disguised as GIF files to circumvent Apple’s “BlastDoor” sandbox for message content. The exploit has been given the CVE identifier CVE-2021-30860.
Ref: The exploit works by exploiting an integer overflow vulnerability in Apple’s image rendering library (CoreGraphics).
Available for: iPhone 6s and later, iPad Pro (all models), iPad Air 2 and later, iPad 5th generation and later, iPad mini 4 and later, and iPod touch (7th generation)
Additional: CVE-2021-30858 (WebKit) – Processing maliciously crafted web content may lead to arbitrary code execution. Apple is aware of a report that this issue may have been actively exploited.
For the above details, please refer to the official announcement. – https://support.apple.com/en-us/HT212807
Other reference: https://citizenlab.ca/2021/09/forcedentry-nso-group-imessage-zero-click-exploit-captured-in-the-wild/
.jpg?width=1920&height=1080&fit=bounds)