Preface: On 2014, Amazon Web Services (AWS) is asking those that write code and use GitHub to go back and check their work to make sure they didn’t forget to remove login credentials. The warning comes as news is circulating about the availability of nearly 10,000 AWS keys in plain sight on GitHub just by running a simple query.
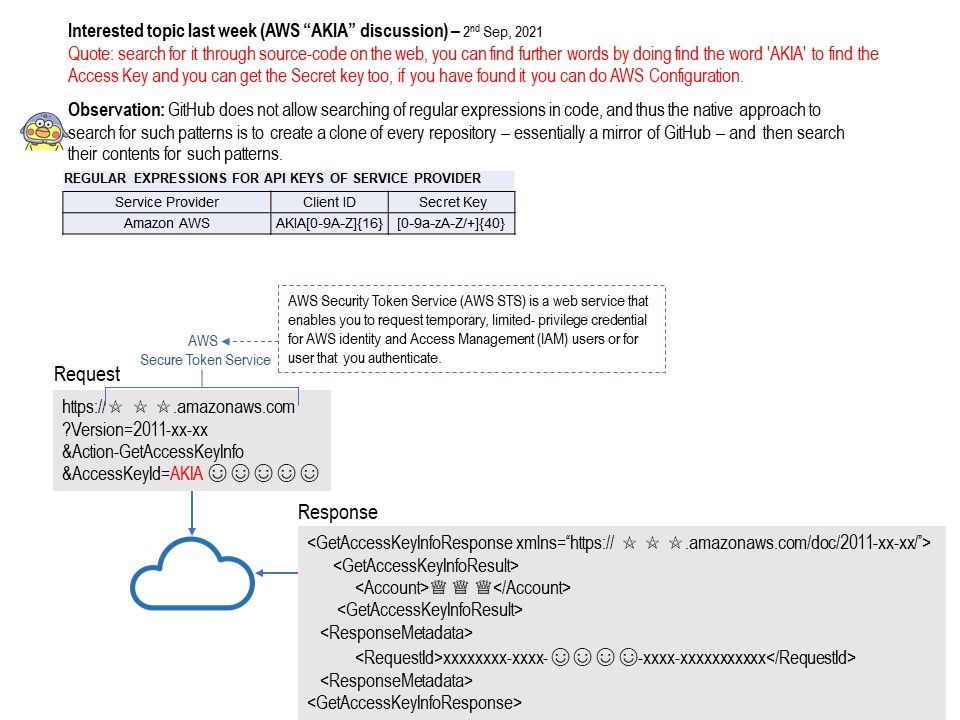
Background: Security expert found that search for it through source-code on the web, you can find further words by doing find the word ‘AKIA’ to find the Access Key and you can get the Secret key too, if you have found it you can do AWS Configuration.
GitHub does not allow searching of regular expressions in code, and thus the naive approach to search for such patterns is to create a clone of every repository – essentially a mirror of GitHub – and then search their contents for such patterns.
Ref:IAM access key IDs beginning with AKIA are long-term credentials, and access key IDs beginning with ASIA are temporary credentials. ASIA credentials are used with AWS Security Token Service (AWS STS) operations for temporary access to AWS services.
Best practice recommended by vendor:
-Note that we recommended against using the root user for everyday work in AWS.
-As a security best practice, we recommended that you regularly rotate (change) IAM user access keys.
-You can review the AWS access keys in your code to determine whether the keys are from an account that you own.