Preface: Big data analysis can understand data by discovering trends and patterns. Machine learning can accelerate this process with the help of decision-making algorithms. It can classify incoming data, recognize patterns, and transform the data to do the technology development. In addition, it is a way to develop artificial intelligence.
Background: What is Apache Zeppelin used for?
Apache Zeppelin is a new and upcoming web-based notebook which brings data exploration, visualization, sharing and collaboration features to Spark. It support Python, but also a growing list of programming languages such as Scala, Hive, SparkSQL, shell and markdown.
Web-based notebooks are files that contain the input code and output such as results and graphs from an interactive session. They also contain additional information, such as documentation, mathematical expressions, and media related to an interactive session. Therefore it is the key element of big data analytics.
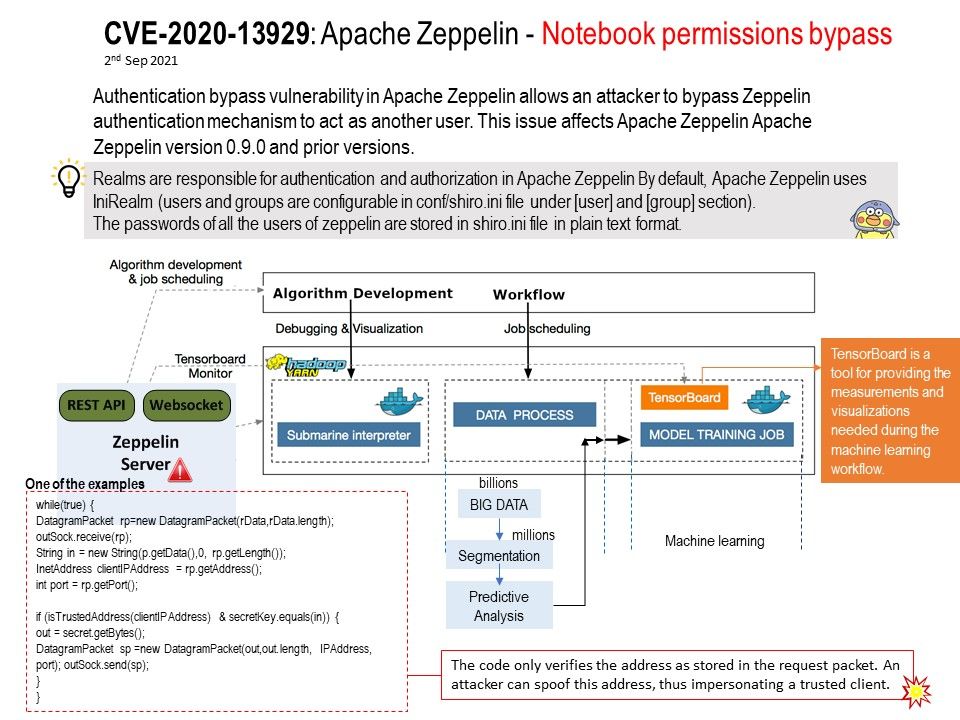
Vulnerability details: Authentication bypass vulnerability in Apache Zeppelin allows an attacker to bypass Zeppelin authentication mechanism to act as another user. This issue affects Apache Zeppelin Apache Zeppelin version 0.9.0 and prior versions. The attack can only be initiated within the local network. No form of authentication is needed for a successful exploitation. Please refer to the link for details – https://seclists.org/oss-sec/2021/q3/150