Preface: Cyberark provides the perfect authentication solution for enterprises. Because of their solutions, traditional authentication methods have evolved. However, there is no absolute anti-hacking solution in the world. The following explanation is to let you quickly understand this vulnerability. Even if this is not the right way, you will find out what they are doing.
Background: The CyberArk Vault uses a Shared Secret in order for the Server to identify a person. This Shared Secret can be a password or a combination of a password and another type of authentication. The Vault can enforce a password policy to avoid usage of passwords that can be easily guessed.
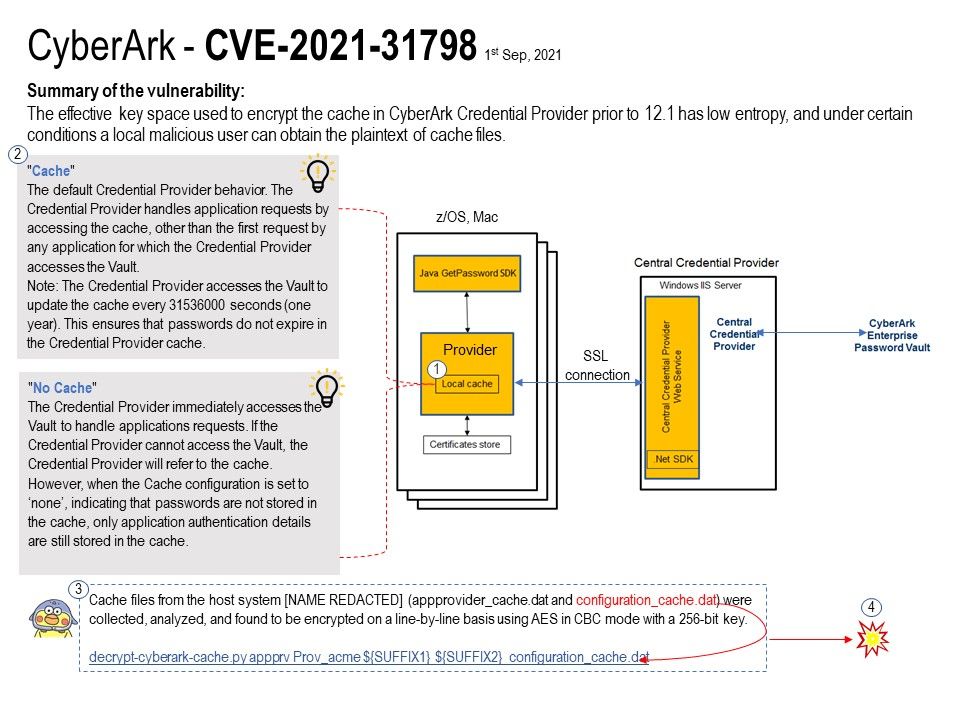
Vulnerability details: A vulnerability was found in CyberArk Credential Provider up to 12.0. An attack has to be approached locally.
Under certain conditions, the effective key space used to encrypt the cache is significantly reduced.
The effective key space used to encrypt the cache in CyberArk Credential Provider prior to 12.1 has low entropy, and under certain conditions a local malicious user can obtain the plaintext of cache files.
Remediation: Upgrading to version 12.1 eliminates this vulnerability.
Reference: The advisory is shared at korelogic.com – https://korelogic.com/Resources/Advisories/KL-001-2021-010.txt