Preface: Windows RCE vulnerabilities have targeted Office users, and Microsoft urgently provides mitigation instructions.
Background: The MS web browser COM control adds browsing, document, viewing, and downloading capabilities to your applications. Parsing and rendering of HTML documents in the WebBrowser control is handled by the MSHTML component which is an Active Document Dynamic HTML (DHTML) object Model hosting ActiveX Controls and script languages.
Unicode is a standard encoding system that is used to represent characters from almost all languages. Every Unicode character is encoded using a unique integer code point between 0 and 0x10FFFF .
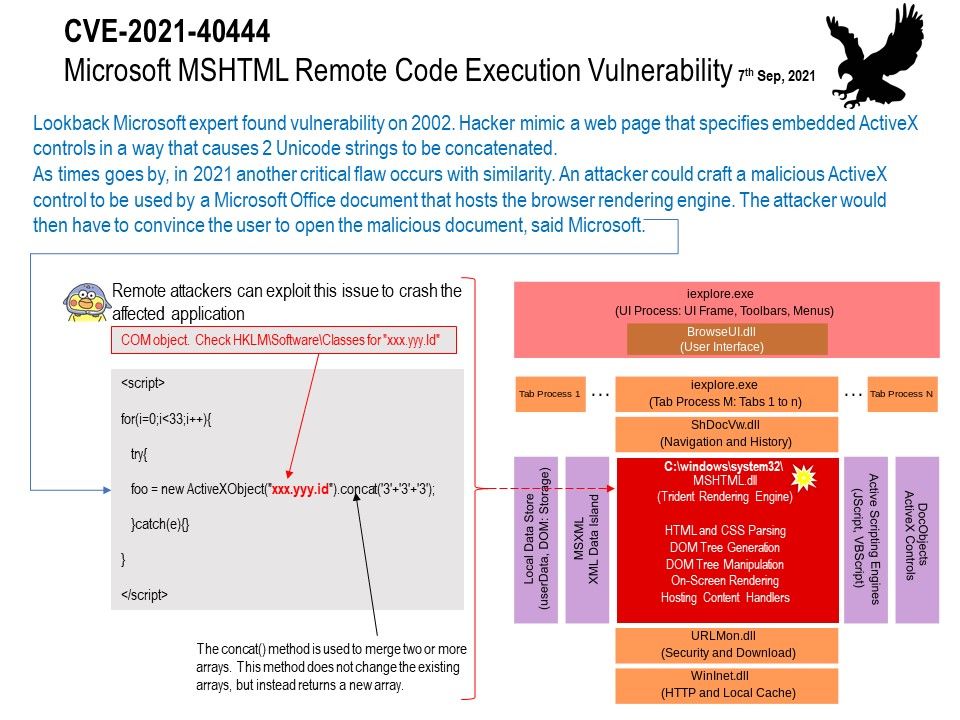
Vulnerability details: Lookback Microsoft expert found vulnerability on 2002. Hacker mimic a web page that specifies embedded ActiveX controls in a way that causes 2 Unicode strings to be concatenated.
As times goes by, in 2021 another critical flaw occurs with similarity. An attacker could craft a malicious ActiveX control to be used by a Microsoft Office document that hosts the browser rendering engine. The attacker would then have to convince the user to open the malicious document, said Microsoft. For mitigation and solutions, please refer to the link – https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-40444