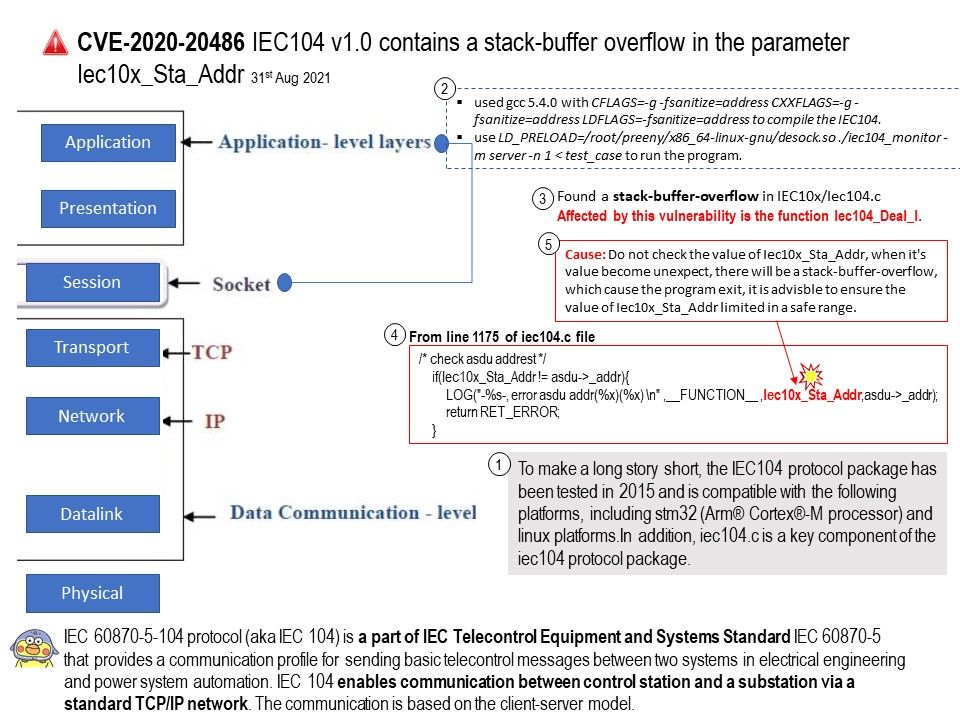
Preface: IEC 60870-5-104 protocol (aka IEC 104) is a part of IEC Telecontrol Equipment and Systems Standard IEC 60870-5 that provides a communication profile for sending basic telecontrol messages between two systems in electrical engineering and power system automation.
Background: IEC 104 enables communication between control station and a substation via a standard TCP/IP network. The communication is based on the client-server model. The IEC104 protocol package has been tested in 2015 and is compatible with the following platforms, including stm32 (Arm® Cortex®-M processor) and linux platforms.In addition, iec104.c is a key component of the iec104 protocol package.
Vulnerability details: IEC104 v1.0 contains a stack-buffer overflow in the parameter Iec10x_Sta_Addr. This vulnerability is known as CVE-2020-18730 since 13th Aug, 2020. However, the vulnerability was released by NIST on August 23, 2021. The technical article state that a segmentation violation in the Iec104_Deal_I function of IEC104 v1.0 allows attackers to cause a denial of service (DOS). In addition, start from line 1175 of the iec104[.]c file. Experts discovered where the vulnerability occurred.
CVE-2020-18730 details can be found on this link – https://nvd.nist.gov/vuln/detail/CVE-2020-18730
Mitigation: Run or compile the software using features or extensions that automatically provide a protection mechanism that mitigates or eliminates buffer overflows. For example, certain compilers and extensions provide automatic buffer overflow detection mechanisms that are built into the compiled code. Examples include the Microsoft Visual Studio /GS flag, Fedora/Red Hat FORTIFY_SOURCE GCC flag, StackGuard, and ProPolice.