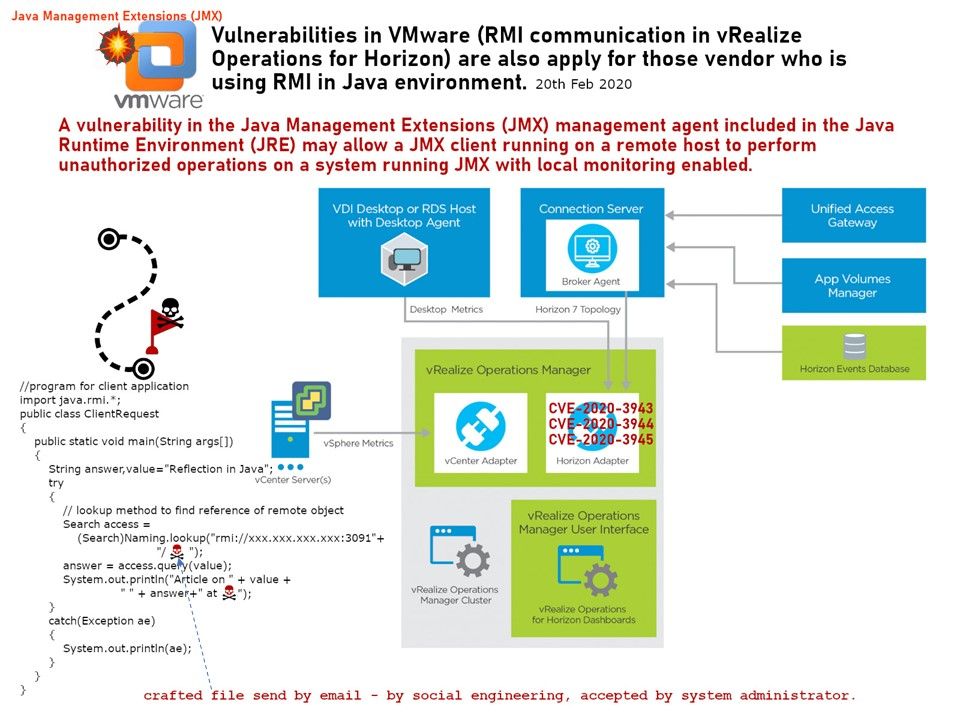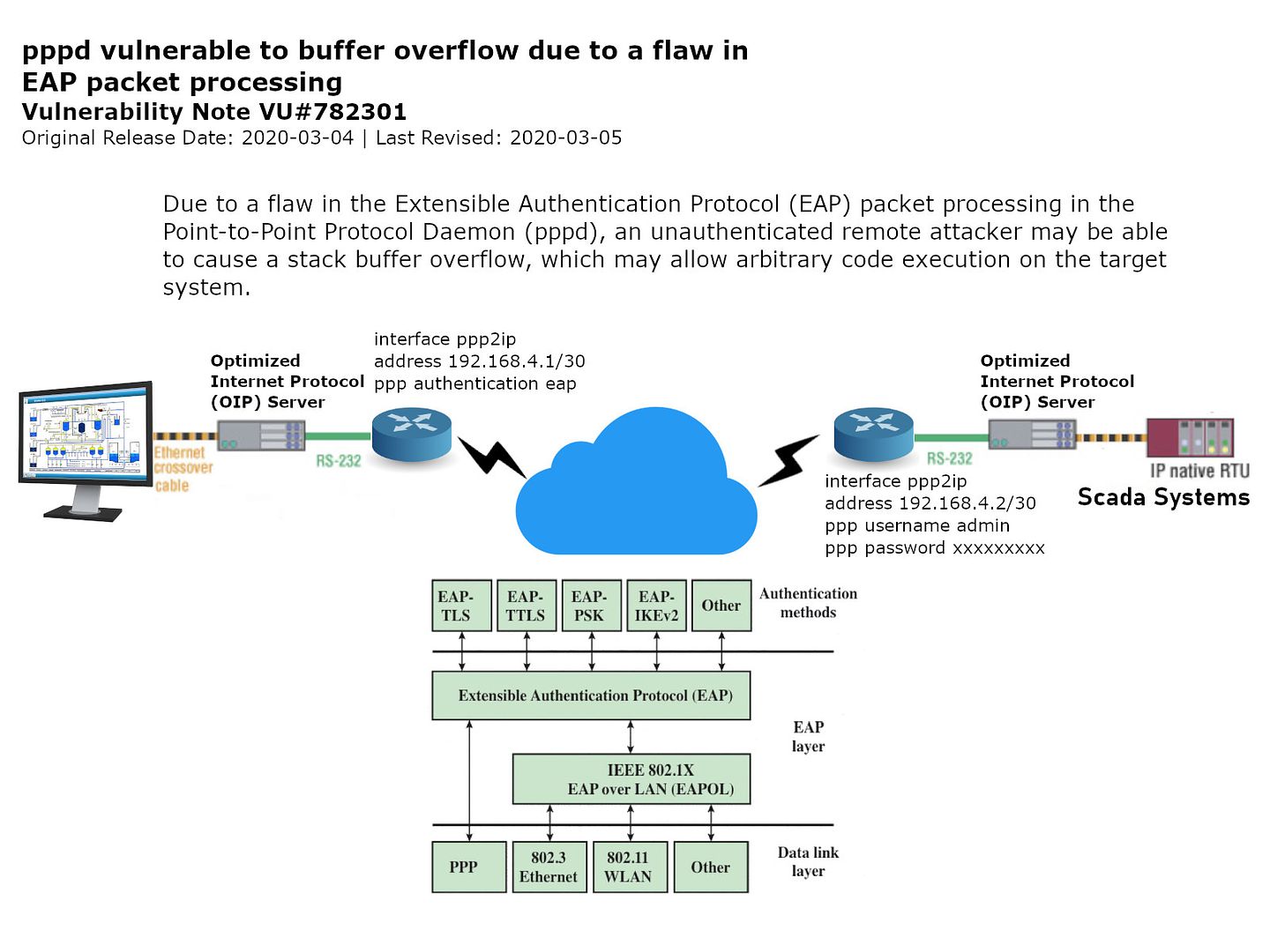
Preface: PPP daemon (pppd) which is used to manage network connections between two nodes on Unix-like operating systems. The EAP extension to PPP was first defined in RFC 2284, now obsoleted by RFC 3748.
Synopsis: A 17-year-old defect in Linux system found! The impact will be included dial-up modems, DSL broadband connections, and Virtual Private Networks. The Linux system including Debian, Ubuntu, SUSE Linux, Fedora, NetBSD and Red Hat Enterprise Linux has been impacted. In the old technology world, PPP over Ethernet, defined in RFC 2516, is a method of transmitting PPP over Ethernet. It provides the ability to connect a network of PPPoE client hosts to a service provider access concentrator over a single bridging access device. Above communication protocol do the interconnect function on automation system and SCADA architecture. The impact of this issue was included different industry especially Manufacturing, Food Production, Electric and Gas Utilities & Waste Water Treatment. Even though the business equipment do not have exception. The business products including Cisco CallManager, TP-LINK products and Synology products. The OpenWrt Project is a Linux operating system targeting embedded devices. Embedded computing platforms are responsible for many of the of the lower-level mechanics that drive the IoT. It seems that the area of impact will be included of this area.
Official announcement – https://www.kb.cert.org/vuls/id/782301/
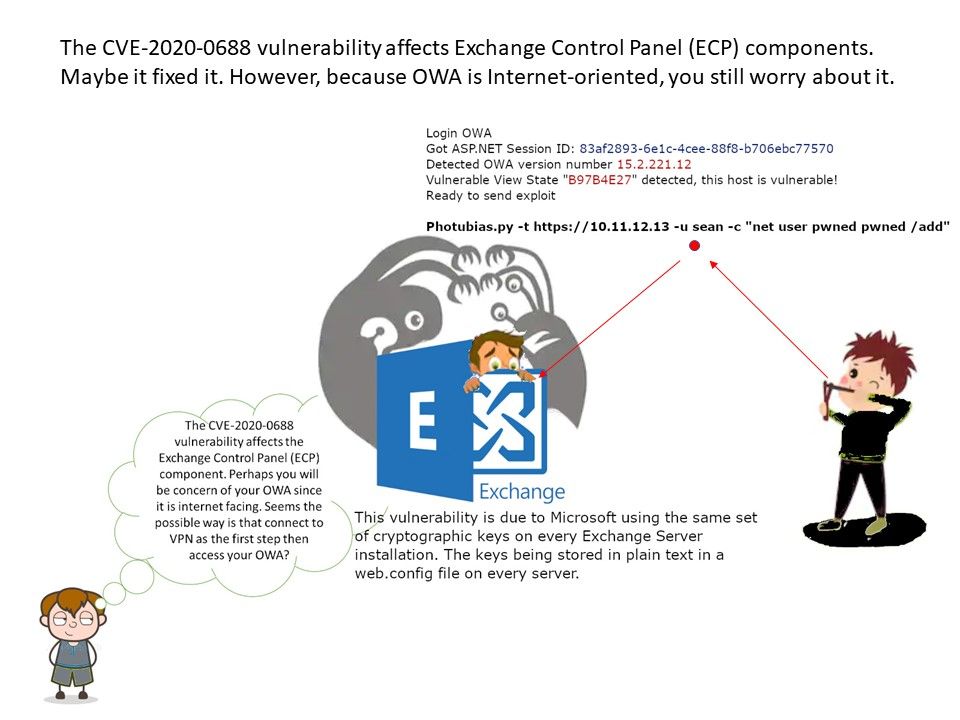



.jpg)
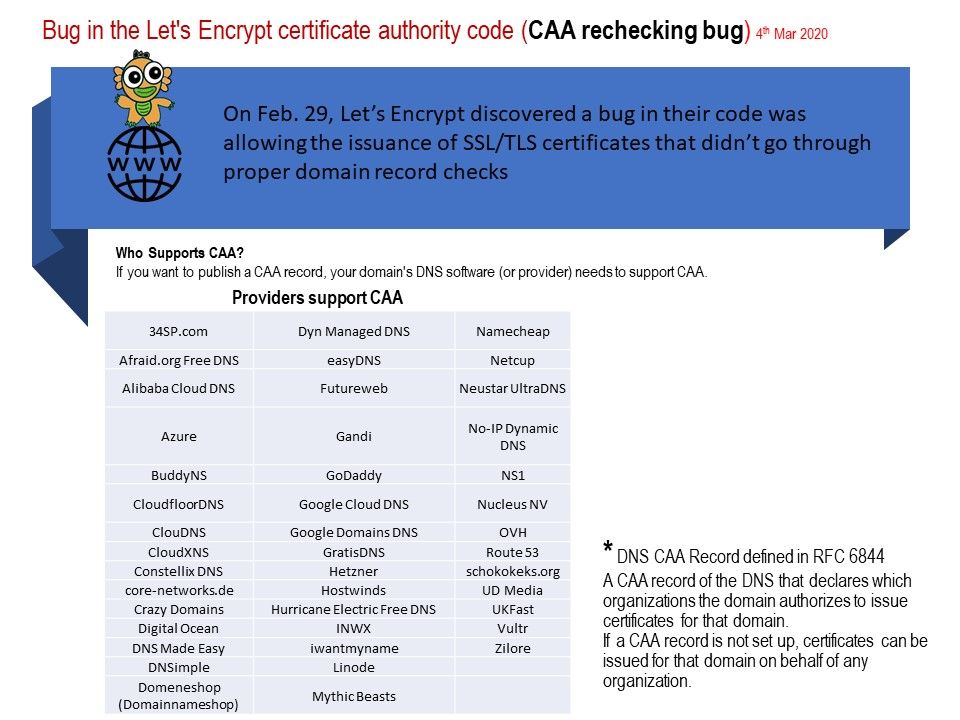
.jpg)