Preface: What is difference between underflow and overflow?
Buffer Overflow – When accessed memory is beyond the end of the buffer.
Buffer Underflow – When the accessed memory is before the beginning of a buffer.
Background: Zephyr is embedded RTOS, it compatible to support more than 350 CPU boards includes x86, ARM, ARC, MIPS, etc. The Zephyr Project has been one of the fastest growing RTOSes, with ambitious goals established in their charter for connected and constrained devices; but it is more than just an RTOS. It is an open-source and open-governance project with a full and growing ecosystem of drivers, communication stacks, hardware abstractions, low-power OS services, build system and application components that allow for the rapid creation of innovative applications.
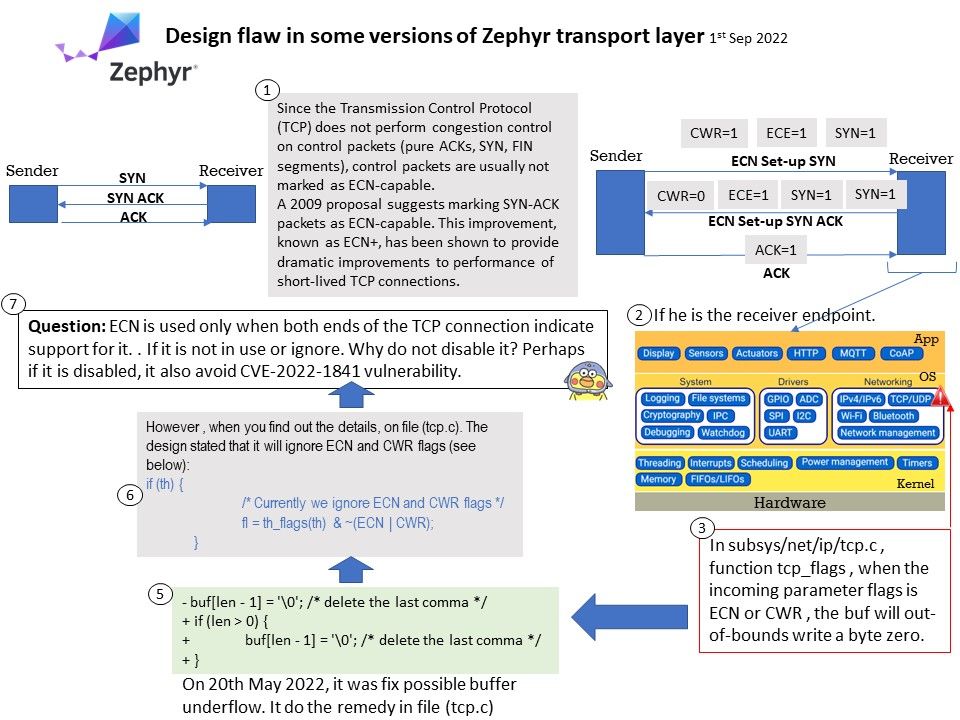
About Control use of Explicit Congestion Notification (ECN) by TCP: ECN is used only when both ends of the TCP connection indicate support for it. This feature is useful in avoiding losses due to congestion by allowing supporting routers to signal congestion before having to drop packets.
Vulnerability details: In subsys/net/ip/tcp[.]c , function tcp_flags , when the incoming parameter flags is ECN or CWR , the buf will out-of-bounds write a byte zero.
When a malformed tcp packet is received, the tcp_flags function does not check the validity of the parameters, but directly parses the th_flags field in TCP header. When th_flags is ECN or CWR , in the tcp_flags function, len is always 0, and buf[0-1] will be
written ‘\0’ . This will modify other data on the stack.
On 20th May 2022, it was fix possible buffer underflow. It do the remedy in file (tcp[.]c). Details can be found at this link – https://github.com/zephyrproject-rtos/zephyr/security/advisories/GHSA-5c3j-p8cr-2pgh
Question: ECN is used only when both ends of the TCP connection indicate support for it. If it is not in use or ignore. Why do not disable it? Perhaps if it is disabled, it also avoid CVE-2022-1841 vulnerability.