Preface: Don’t contempt this design weakness. Why? Red Hat Virtualization (RHV, previously known as Red Hat Enterprise Virtualization) is an enterprise virtualization product based on the KVM hypervisor.
Background: Avi Kivity began the development of KVM in mid-2006 at Qumranet, a technology startup company that was acquired by Red Hat in 2008. KVM surfaced in October, 2006 and was merged into the Linux kernel mainline in kernel version 2.6. 20, which was released on 5 February 2007. KVM is maintained by Paolo Bonzini.
- OpenShift Virtualization uses the Red Hat Enterprise Linux KVM hypervisor technology deployed using containers, allowing Kubernetes to deploy and manage VMs locally.
- KVM is a hypervisor, which is used to achieve full virtualization. Many of the cluster environments make use of KVM in order to achieve a cluster of virtual machines. In order to manage this type of cluster and the virtual machines therein, managing systems have been developed.
Vulnerability details: An issue was discovered the x86 KVM subsystem in the Linux kernel before 5.18.17. Unprivileged guest users can compromise the guest kernel because TLB flush operations are mishandled in certain KVM_VCPU_PREEMPTED situations.
As a consequence, KVM instruction emulation can access memory through stale translations when the guest kernel thinks it has flushed all
cached translations. This could potentially be used by unprivileged userspace inside a guest to compromise the guest kernel.
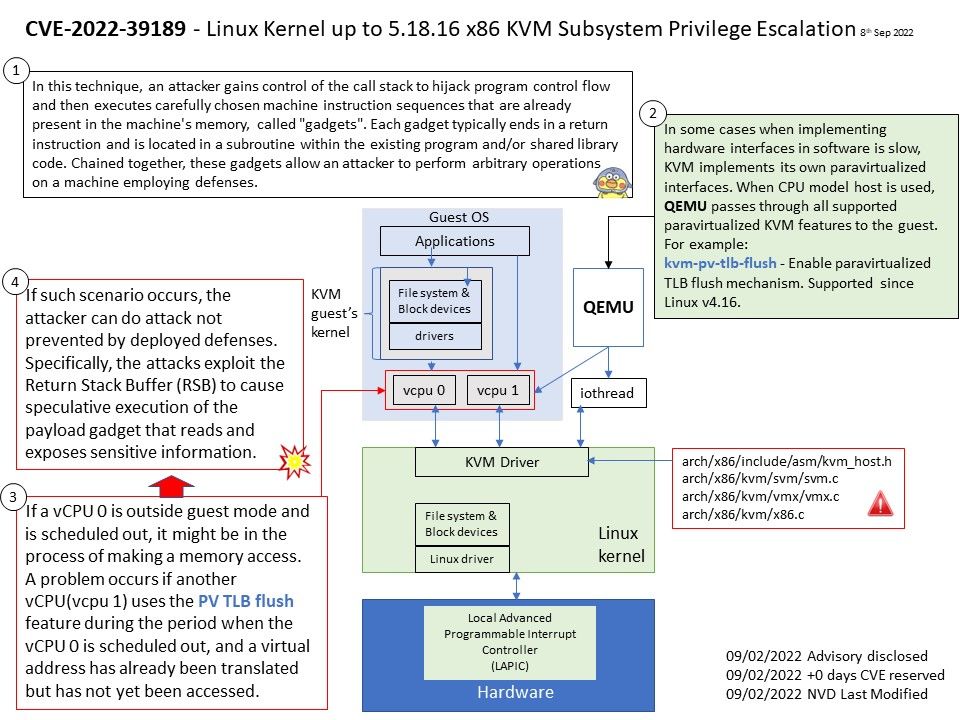
Refer to attached diagram. If a vCPU 0 is outside guest mode and is scheduled out, it might be in the process of making a memory access. A problem occurs if another vCPU (vcpu 1) uses the PV TLB flush feature during the period when the vCPU 0 is scheduled out. The problem is that a virtual address has already been translated but has not yet been accessed.
If such scenario occurs, the attacker can do attack not prevented by deployed defenses. Specifically, the attacks exploit the Return Stack Buffer (RSB) to cause speculative execution of the payload gadget that reads and exposes sensitive information.
Official announcement – Please refer to the link for details – https://nvd.nist.gov/vuln/detail/CVE-2022-39189