Preface: Not sure if this vulnerability affects all linux brands. However, Debian has solved this problem. Maybe when you turned on your linux yesterday. A critical update will cover this issue.
Remark: Debian Linux’s mainline kernel has been ported bare-metal to the Apple M1 SoC, opening up the way for a Linux ecosystem replacing MacOS.
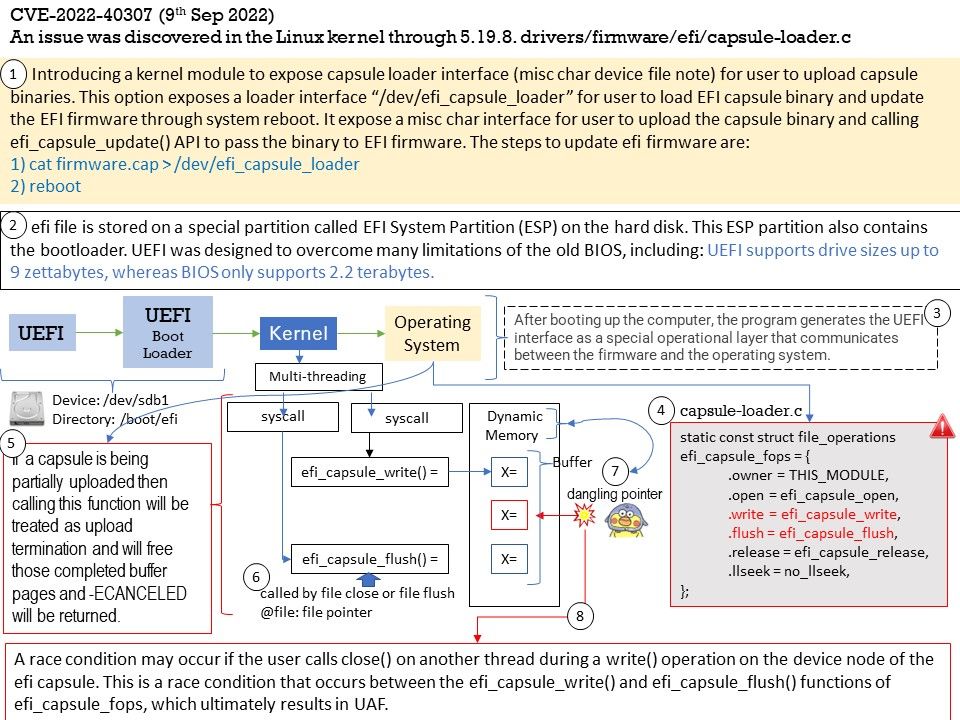
Background: BIOS uses the Master Boot Record (MBR) to save information about the hard drive data while UEFI uses the GUID partition table (GPT). Compared with BIOS, UEFI is more powerful and has more advanced features. It is the latest method of booting a computer, which is designed to replace BIOS.UEFI is the replacement for BIOS. EFI is the storage partition used with UEFI.
Unified Extensible Firmware Interface is a personal computer system specification that defines the software interface between the operating system and system firmware as an alternative to BIOS. The extensible firmware interface is responsible for POST, contacting the operating system, and providing the interface between the operating system and the hardware. The predecessor of UEFI was the Intel Boot Initiative, which was developed by Intel in 1998, and was later renamed the Extensible Firmware Interface.
Introducing a kernel module to expose capsule loader interface (misc char device file note) for user to upload capsule binaries. This option exposes a loader interface “/dev/efi_capsule_loader” for user to load EFI capsule binary and update the EFI firmware through system reboot. It expose a misc char interface for user to upload the capsule binary and calling efi_capsule_update() API to pass the binary to EFI firmware. The steps to update efi firmware are:
1) cat firmware[.]cap > /dev/efi_capsule_loader
2) reboot
Vulnerability details: An issue was discovered in the Linux kernel through 5.19.8. drivers/firmware/efi/capsule-loader[.]c has a race condition with a resultant use-after-free.
NVD Published Date:09/09/2022
NVD Last Modified:09/09/2022
Official announcement – https://nvd.nist.gov/vuln/detail/CVE-2022-40307