Preface: The vendor who transforming Linux kernel not limit to Apple computer. Oracle, they are also has it own Linux Kernel so called UEK (Unbreakable Enterprise Kernel).
So, who maintains software updates for Oracle Linux? It will depend on Oracle Linux yum server.
Background: Oracle Linux commes with a choice of two kernels, the UEK, which is installed and enabled by default, and the Red Hat Compatible Kernel. The Unbreakable Enterprise Kernel (UEK) is a Linux kernel built by Oracle and supported through Oracle Linux support. Its focus is performance, stability, and minimal backports by tracking the mainline source code as closely as is practical. The UEK 4 Cryptographic Module is a software only cryptographic module that provides general-purpose cyrptographic services to the remainder of the Linux kernel.
Vulnerability details: On 15th Nov, 2021, CVE reserved not disclose to public. Till 30th Aug 2022, the details of vulnerability exposed. A flaw in net_rds_alloc_sgs() in Oracle Linux kernels allows unprivileged local users to crash the machine.
Reliable Datagram Sockets (RDS) is a high-performance, low-latency, reliable connectionless protocol for delivery datagrams. It is development by Oracle Coporation. This new function come with Linux kernel 2.6.30. And released on 9th June 2009. The code was contributed by the openFabrics Alliance (OFA).
Official details: https://git.kernel.org/pub/scm/linux/kernel/git/torvalds/linux.git/commit/?id=ea010070d0a7497253d5a6f919f6dd107450b31a
Reference: So far by Oracle Linux design, RDS provides reliable, ordered datagram delivery by using a single reliable connection between two nodes in the cluster.
RDS supports a number of sysctls in/proc/sys/net/rds
Applications can ask the RDS kernel module to receive notifications via control message (for instance, there is a notification when a congestion update arrived, oe when a RDMA operation completes). These notifications are received through the msg[.]msg_control buffer of struct msghdr.
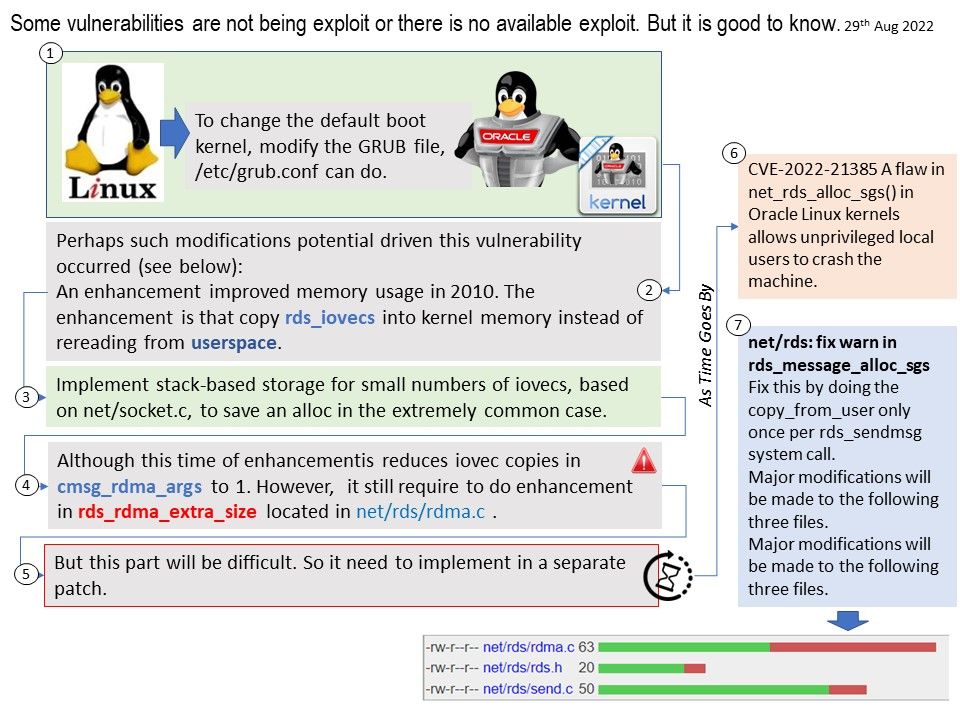
Suspect this is the start of the vulnerability story:
Perhaps such modifications potential driven this vulnerability occured (see below):
An enhancement improved memory usage in 2010. The enhancement is that copy rds_iovecs into kernel memory instead of rereading from userspace.
Implement stack-based storage for small numbers of iovecs, based on net/socket[.]c, to save an alloc in the extremely common case.
Although this time of enhancementis reduces iovec copies in cmsg_rdma_args to 1. However, it still require to do enhancement in rds_rdma_extra_size located in net/rds/rdma[.]c .
But this part will be difficult. So it need to implement in a separate patch.