Preface: Qualcomm has been a major player in the technology space, especially since the company saw the potential of IoT and mobile processing early on, so it’s been growing.
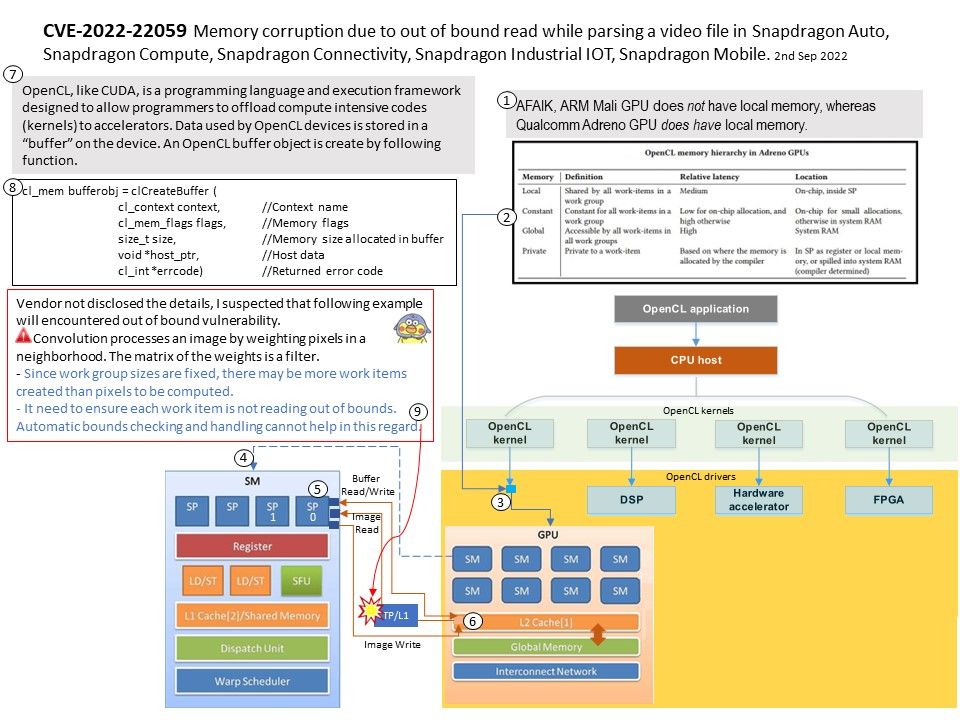
Background: Qualcomm enables programming of the Adreno GPU in its Snapdragon application processors via the open standard OpenCL language and API. OpenCL support enables programmers to offload computer vision algorithm kernels to the GPU, which in turn provides speed and power-consumption advantages over a CPU implementation.
The major functionality includes execution of the graphics shaders (e.g., vertex shader, fragment shader and compute shader), as well as the OpenCL kernels.
Texture processor (TP) and level-1 (L1) cache. Texture processor is an important engine in Adreno that handles many texture related operations for graphics and compute. Its primary function for OpenCL is to serve the request of SP to do texture operations such as sampling on image objects. The sampling could be point sampling or bi-linear filtering, which can be useful for down- or up-sampling. The image object could be of 1D, 2D, or 3D, and in different channel order, such as RGBA, RG, R, etc. TP in Adreno has a dedicated L1 cache, which is read-only cache and stores data fetched from level-2 (L2) cache for texture operations.
Vulnerability details: Memory corruption due to out of bound read while parsing a video file in Snapdragon Auto, Snapdragon Compute, Snapdragon Connectivity, Snapdragon Industrial IOT, Snapdragon Mobile. The weakness was published 09/02/2022. The advisory is shared at qualcomm.com.
Vendor not disclosed the details, I suspected that an example will encountered out of bound vulnerability. (see attached diagram).
Convolution processes an image by weighting pixels in a neighborhood. The matrix of the weights is a filter.
- Since work group sizes are fixed, there may be more work items created than pixels to be computed.
- It need to ensure each work item is not reading out of bounds. Automatic bounds checking and handling cannot help in this regard.
The weakness was published 09/02/2022. The advisory is shared at https://www.qualcomm.com/company/product-security/bulletins/august-2022-bulletin