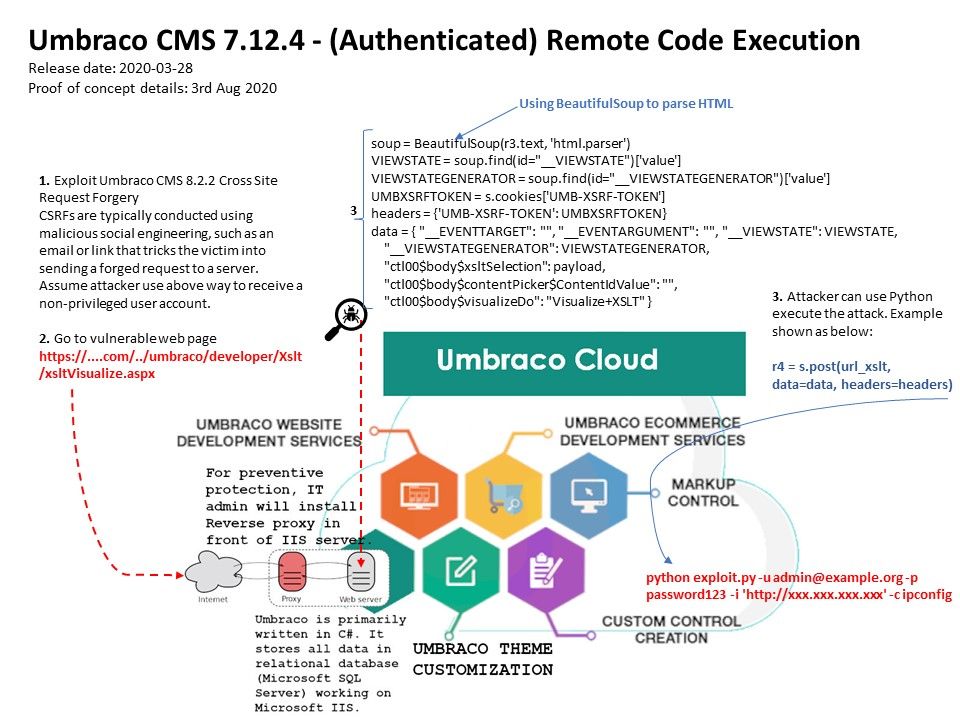
Preface: Serialization in Java is a mechanism of writing the state of an object into a byte-stream. It is mainly used in Hibernate, RMI, JPA, EJB and JMS technologies. The reverse operation of serialization is called deserialization where byte-stream is converted into an object.
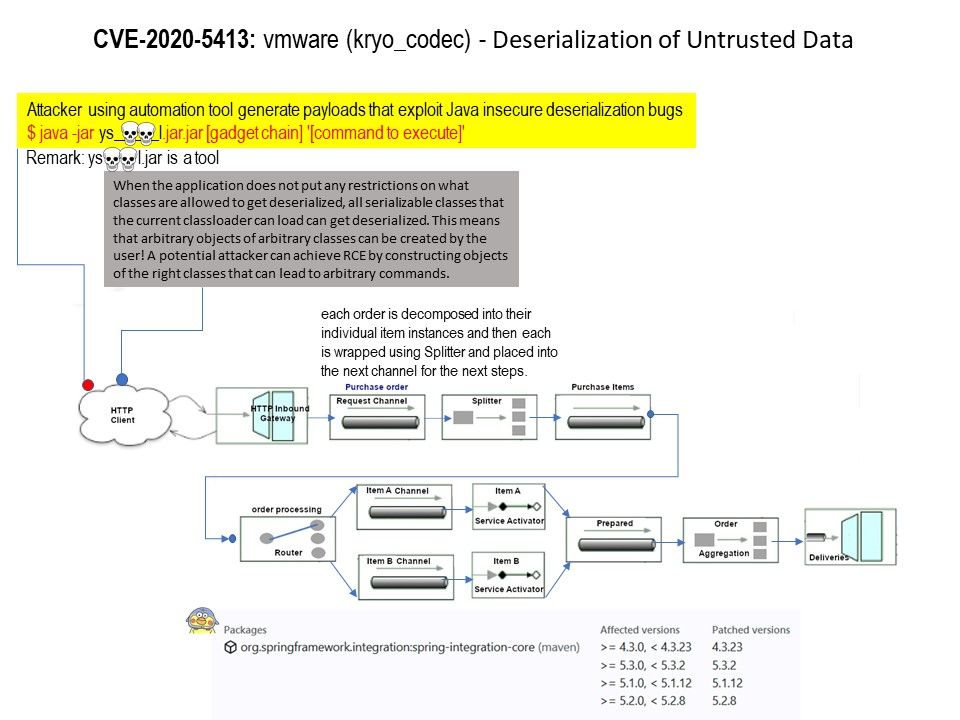
Product background: Spring Integration framework provides Kryo Codec implementations as an alternative for Java (de)serialization. About 11 years ago. VMWare has announced the acquisition of SpringSource, a provider of Web application development and management services.
Vulnerability details: When Kryo is configured with default options, all unregistered classes are resolved on demand. This leads to the “deserialization gadgets” exploit when provided data contains malicious code for execution during deserialization.
Remedy: Kryo can be configured to require a set of trusted classes for (de)serialization. Spring Integration should be proactive against blocking unknown “deserialization gadgets” when configuring Kryo in code. For more details, please refer to the link – https://spring.io/blog/2020/07/22/spring-integration-4-3-23-5-1-12-5-2-8-5-3-2-available-cve-2020-5413

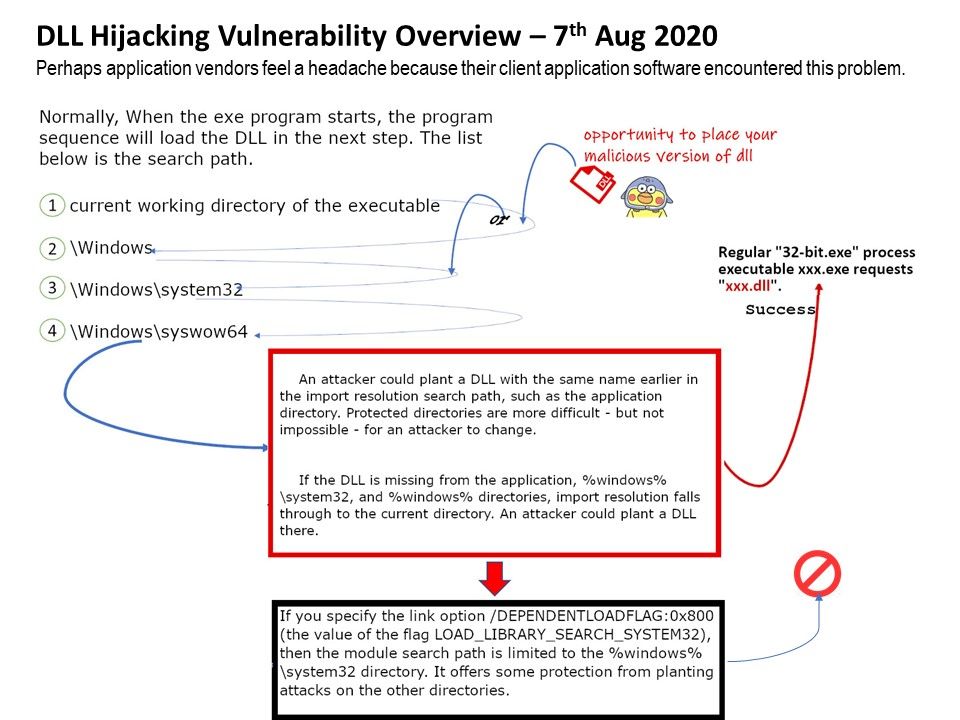
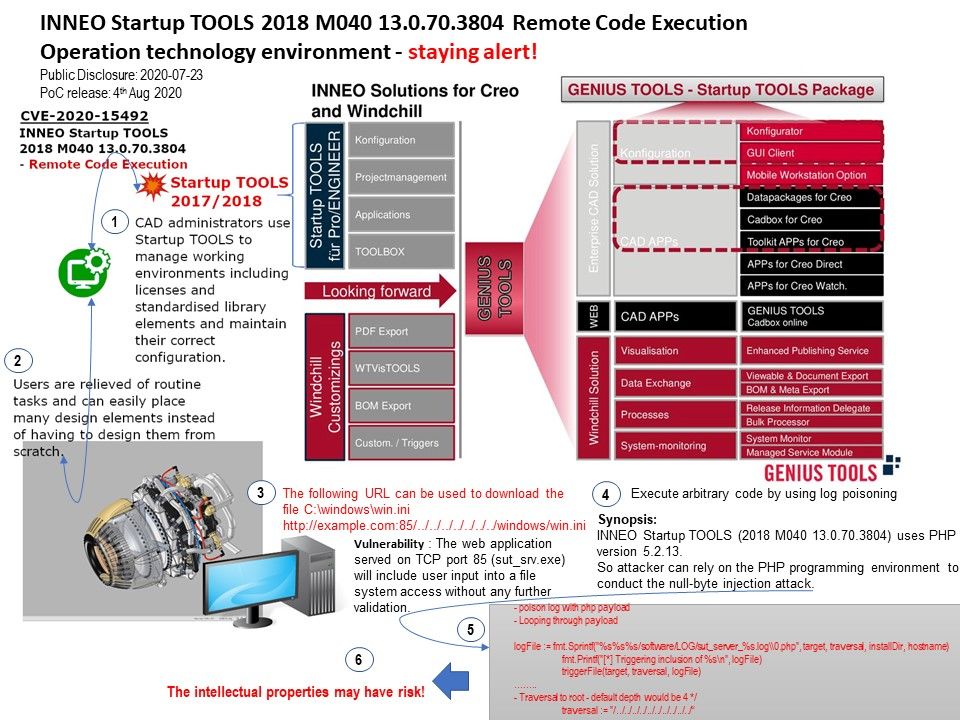
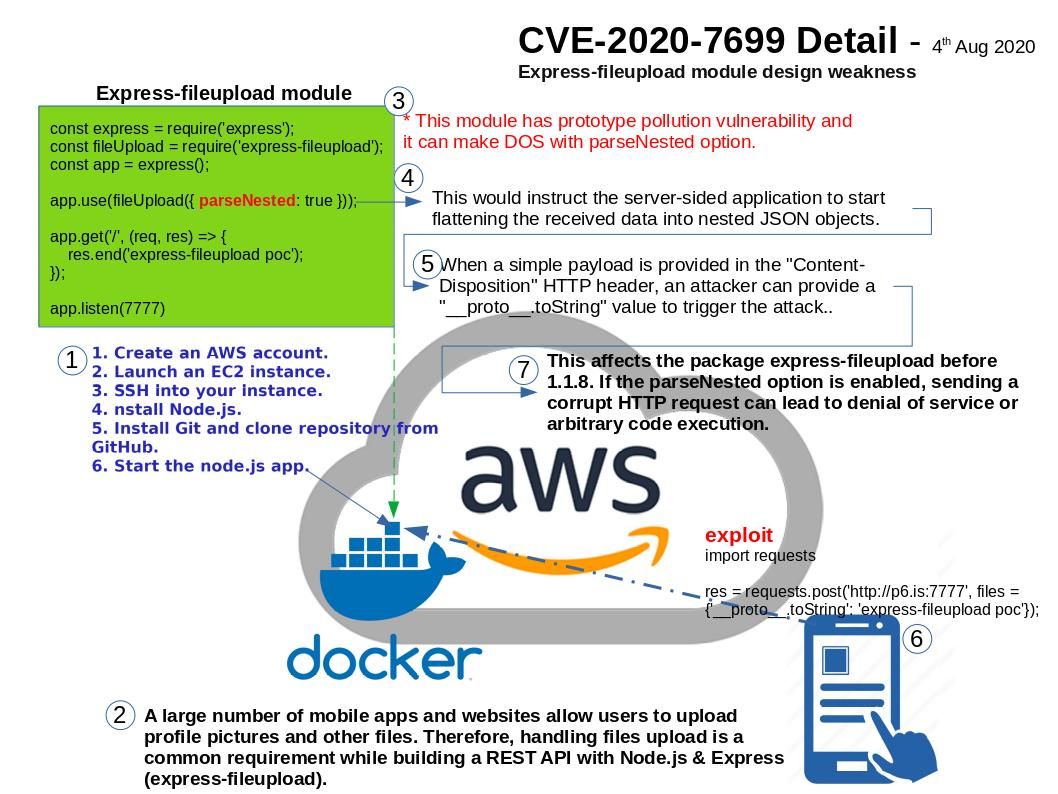
.jpg?width=1920&height=1080&fit=bounds)
.jpg?width=1920&height=1080&fit=bounds)