Preface: As usual when you read a vulnerability bulletin. The vendor sometimes do not disclose technical details to the public. If you will read daily renewal CVE records. Maybe you feel the same way I do. CPU is one of the key topics of the vulnerability database. Since the supplier has the right to secrecy. As a computer user, all you have to do is patch.
Background: AMD engineers that made the “Zen” architecture powering every AMD processor available today, from AMD Ryzen™ desktop and mobile processors, to AMD EPYC™ CPUs, and AMD Threadripper™ CPUs. It all started with “Zen”. AMD Epyc CPU codenames follow the naming scheme of Italian cities, including Milan (3rd Gen 2021), Rome (2nd Gen 2019) and Naples (1st Gen 2017).
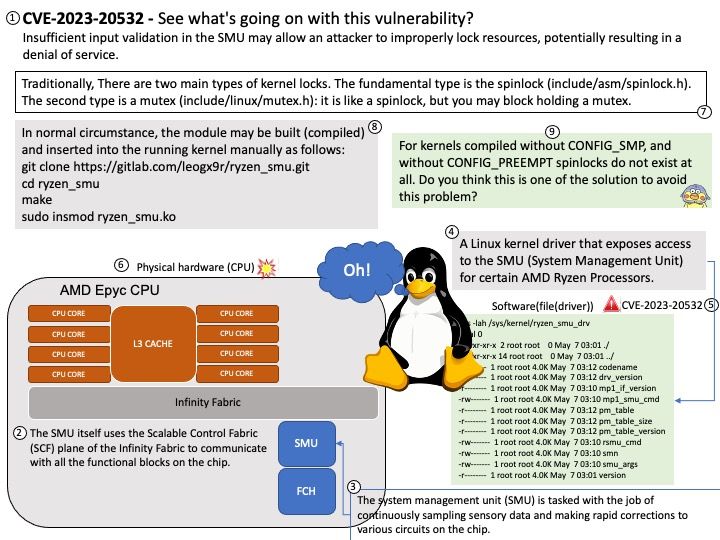
The system management unit (SMU) is tasked with the job of continuously sampling sensory data and making rapid corrections to various circuits on the chip.
Ryzen SMU is a Linux kernel driver that exposes access to the SMU (System Management Unit) for certain AMD Ryzen Processors.
Vulnerability details: Insufficient input validation in the SMU may allow an attacker to improperly lock resources, potentially resulting in a denial of service.
Reference: Traditionally, There are two main types of kernel locks. The fundamental type is the spinlock (include/asm/spinlock[.]h). The second type is a mutex (include/linux/mutex[.]h): it is like a spinlock, but you may block holding a mutex.
For official announcement on AMD Server Vulnerabilities – January 2023. Please refer to url – https://www.amd.com/en/corporate/product-security/bulletin/amd-sb-1032
Remark: If you’re interested in the matter, see the diagram for details.