Preface: Due to the threat posed by a successful attack, Oracle strongly recommends that customers apply Critical Patch Update security patches as soon possible.
Background: AVX-512 debuted in 2016 on Intel’s Xeon Phi x200 (codenamed Knights Landing). However, the instruction set has since found its way into other products from the chipmaker, such as Skylake-SP, Skylake-X, Cannon Lake, and Cascade Lake.
Furthermore, Intel’s support for AVX-512 instructions with its Alder Lake processors.
But an information disclosed by vendor to downstream manufacture that AVX-512 support on Alder Lake much like overclocking.
Remark: Overclocking is the action of increasing a component’s clock rate, running it at a higher speed than it was designed to run.
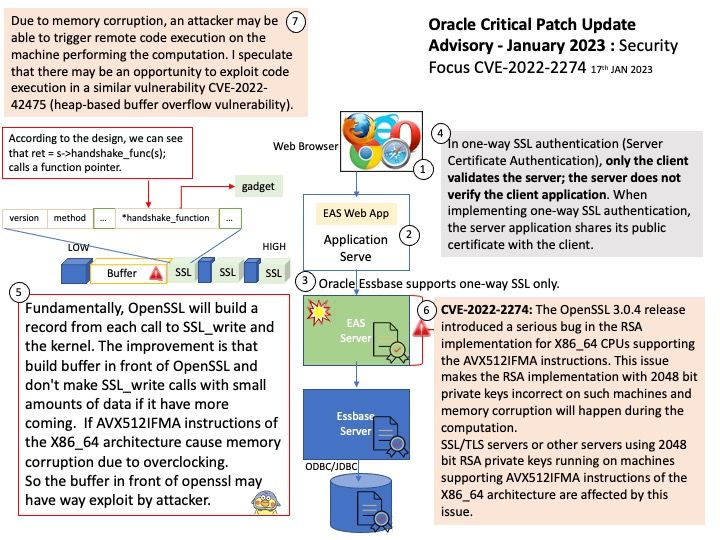
Oracle Essbase is a business analytics solution that uses a proven, flexible, best-in-class architecture for analysis, reporting, and collaboration. Oracle Essbase can be accessed on an intuitive web interface, or using Microsoft Office, for all of your analytic and business modeling needs, from multi-dimensional analysis to complex procedural business logic applied to your data.
Vulnerability details: The OpenSSL 3.0.4 release introduced a serious bug in the RSA implementation for X86_64 CPUs supporting the AVX512IFMA instructions. This issue makes the RSA implementation with 2048 bit private keys incorrect on such machines and memory corruption will happen during the computation. As a consequence of the memory corruption an attacker may be able to trigger a remote code execution on the machine performing the computation. SSL/TLS servers or other servers using 2048 bit RSA private keys running on machines supporting AVX512IFMA instructions of the X86_64 architecture are affected by this issue.
Observation: Fundamentally, OpenSSL will build a record from each call to SSL_write and the kernel. The improvement is that build buffer in front of OpenSSL and don’t make SSL_write calls with small amounts of data if it have more coming. If AVX512IFMA instructions of the X86_64 architecture cause memory corruption due to overclocking.
So the buffer in front of openssl may have way exploit by attacker.
Due to memory corruption, an attacker may be able to trigger remote code execution on the machine performing the computation. I speculate that there may be an opportunity to exploit code execution in a similar vulnerability CVE-2022-42475 (heap-based buffer overflow vulnerability).
Workaround (RedHat) – Disabling the AVX512IFMA instruction set extension can effectively mitigate this flaw:
export OPENSSL_ia32cap=:~0x200000
Official announcement (Oracle): For details please refer to link – https://www.oracle.com/security-alerts/cpujan2023.html