Preface: Some said, found malware lets cybercriminal remotely manipulate your Android.
Background: The full name of TEE is trusted execution environment, which is an area on the CPU of mobile devices (smart phones, tablets, smart TVs). The role of this area is to provide a more secure space for data and code execution, and to ensure their confidentiality and integrity.
Other TEE operating systems are traditionally supplied as binary blobs by third-party vendors or developed internally. Developing internal TEE systems or licensing a TEE from a third-party can be costly to System-on-Chip (SoC) vendors and OEMs.
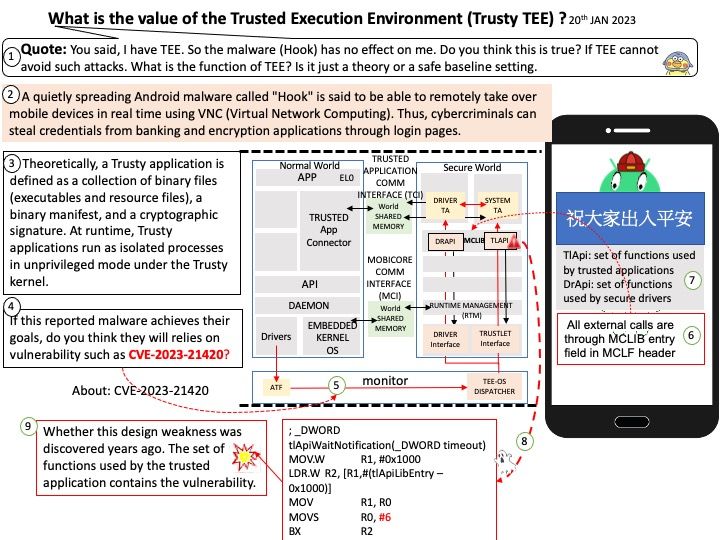
Trusty is a secure Operating System (OS) that provides a Trusted Execution Environment (TEE) for Android. A Trusty application is defined as a collection of binary files (executables and resource files), a binary manifest, and a cryptographic signature. At runtime, Trusty applications run as isolated processes in unprivileged mode under the Trusty kernel.
Technical details: According to headline news, a new Android malware named ‘Hook’ is being sold by cybercriminals, boasting it can remotely take over mobile devices in real-time using VNC (virtual network computing). said bleepingcomputer news.
For details, please refer to URL – https://www.bleepingcomputer.com/news/security/new-hook-android-malware-lets-hackers-remotely-control-your-phone/
Speculation: If this reported malware achieves their goals, do you think they will relies on vulnerability such as CVE-2023-21420?
Solution: To avoid Android malware, you should only install apps from the Google Play Store.
Here’s wishing you a Happy Chinese New Year 2023.