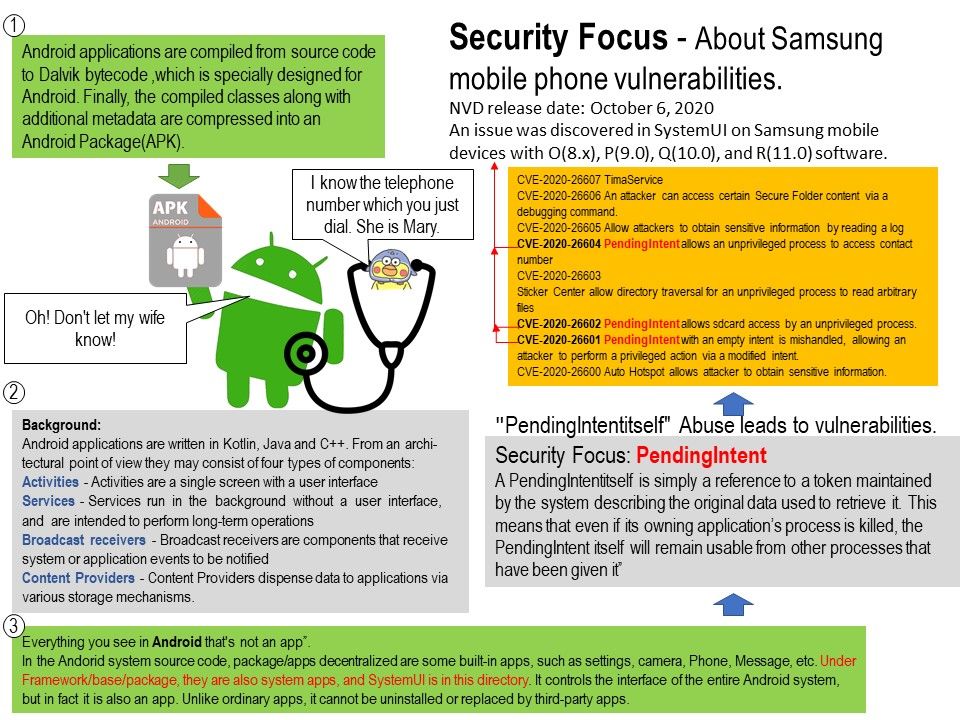
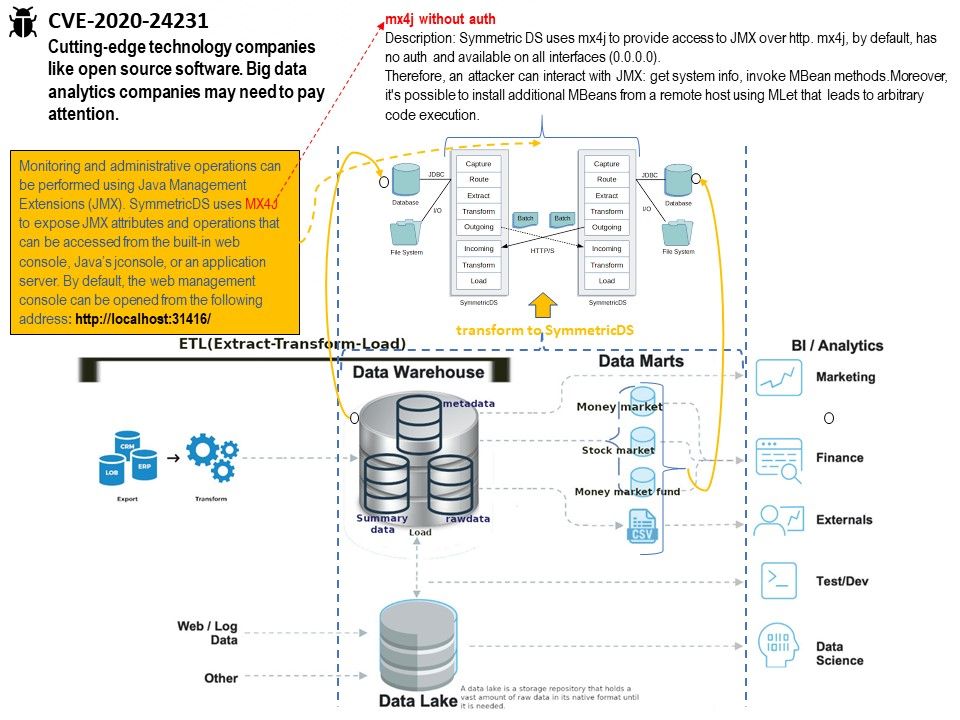
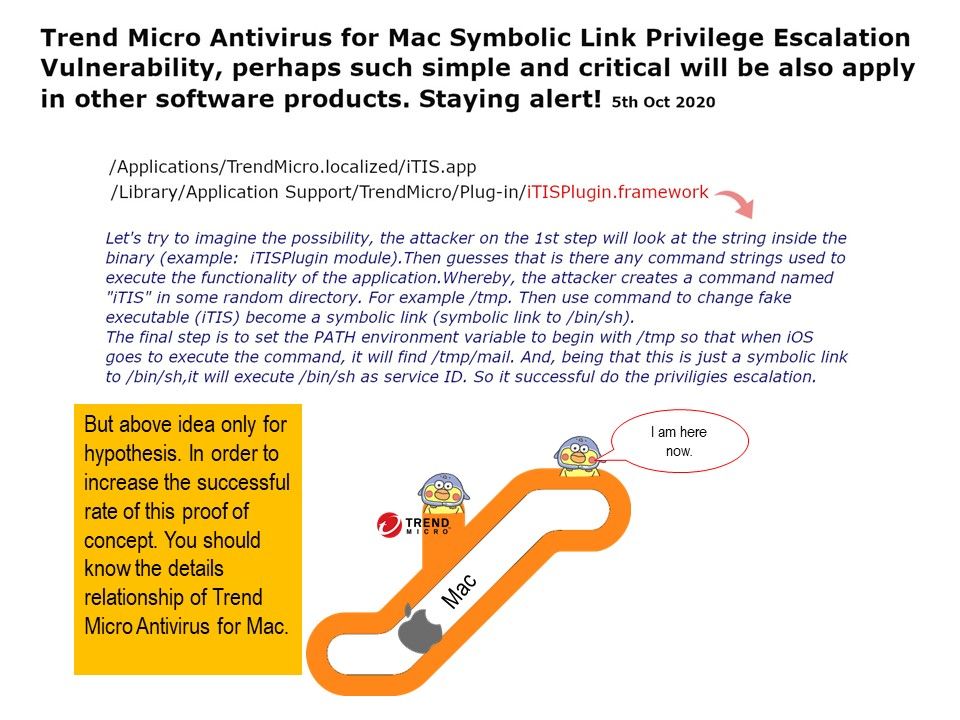
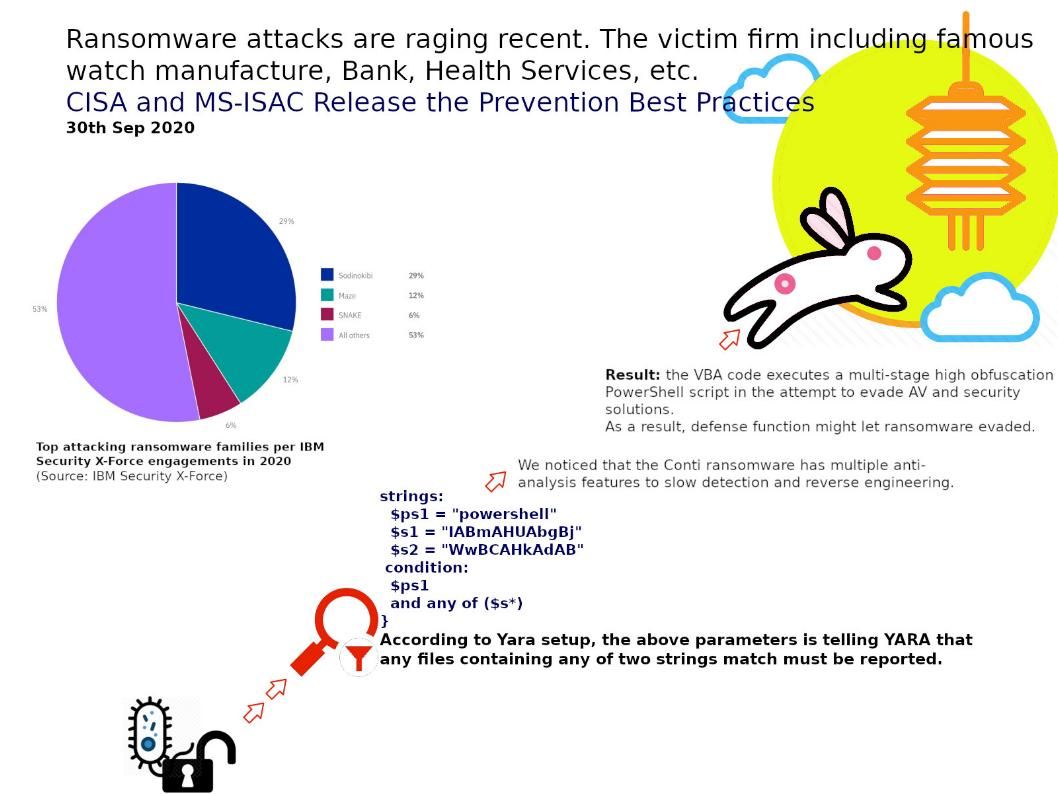
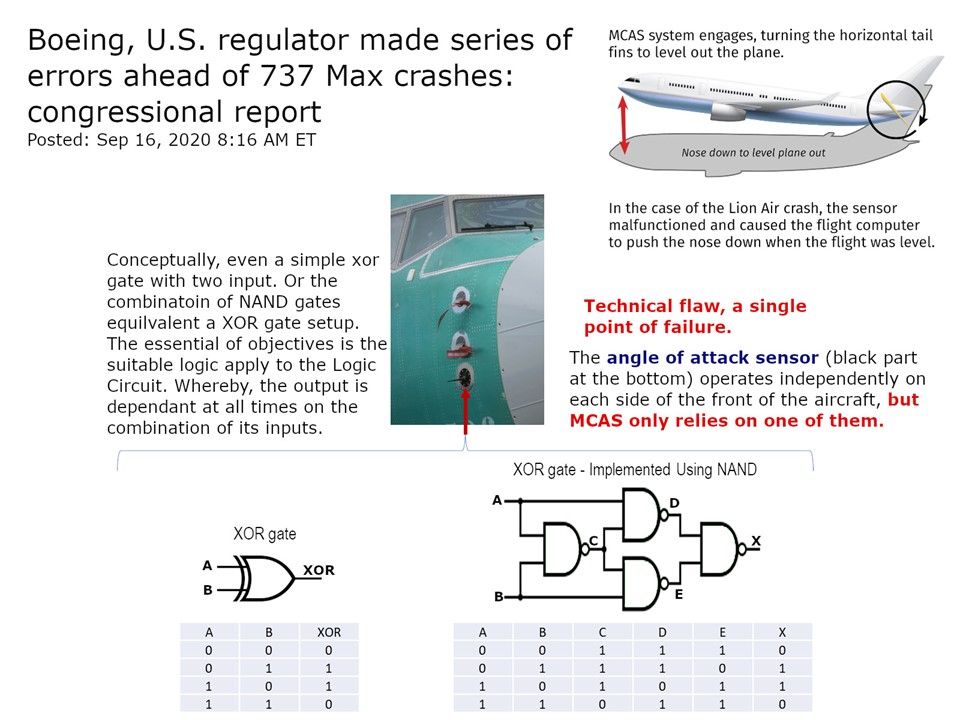
Preface: In order to avoid malware attack, DNS is the 1st door for quarantine. This step not difficult, see whether the domain name which calling will be included in the black list.
What is Punycode?
Unicode that converts words that cannot be written in ASCII.
Background: There are two different scenarios for the cyber threat actor to exploit.
- Attacker build a deceptive IDNs (Internet Domain Name) that are likely to be misled internet user.
- Phishing Attack is Almost Impossible to Detect when encounter Puny-code vulnerability.
Synopsis: If the DNS filter mechanism is not convert the IDN domains in its Punycode form to do the verification, it make a possibility, let the blacklist domain ignore by filter.
Example: The domain “xn--eqru1b157l[.]co” is equivalent to “黑名單[.]co”. Whereby “xn--eqru1b157l” is the Puny-code.
Vulnerability details: Trend Micro Antivirus for Mac 2020 (Consumer) Bypass Web Threat Protection via Internationalized Domain Name Homograph Attack (Puny-code) Vulnerability.
Remedy: Trend Micro has released a new build of Trend Micro Antivirus for Mac Security (Consumer). Please refer to link – https://helpcenter.trendmicro.com/en-us/article/TMKA-09949
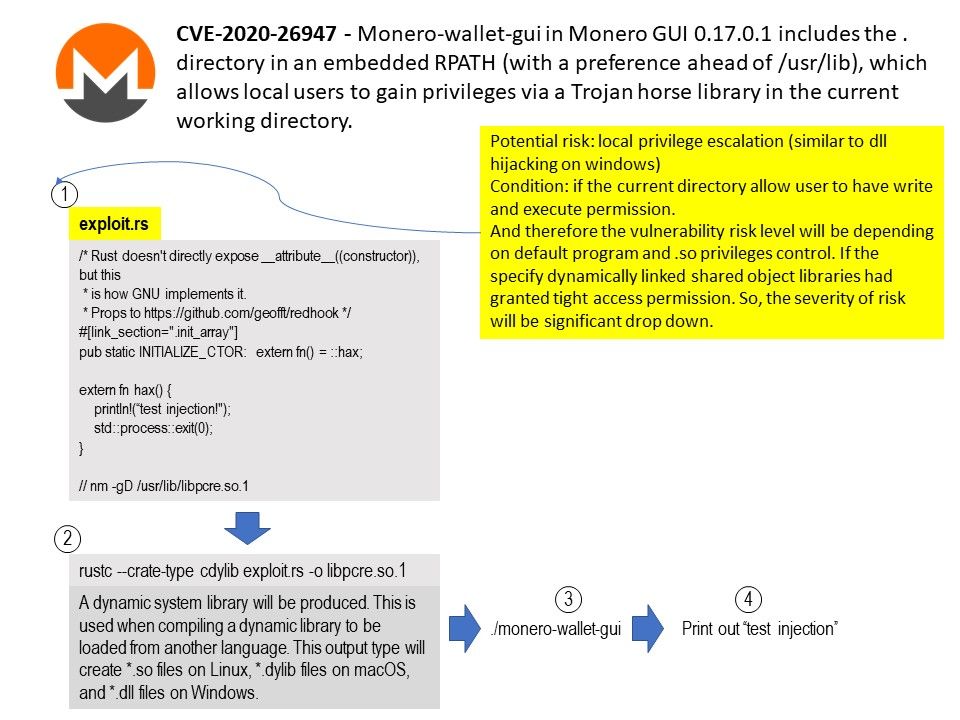
_1.jpg?width=1920&height=1080&fit=bounds)