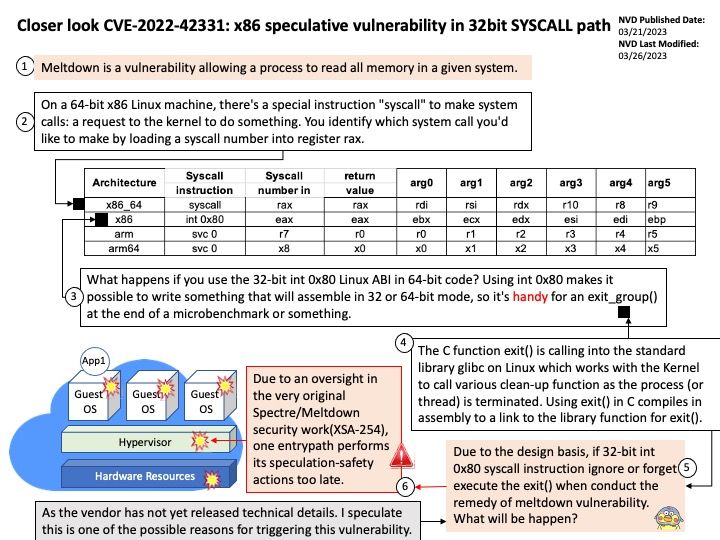
Preface: Meltdown is a vulnerability allowing a process to read all memory in a given system.
Background: The Xen Project is a free and open source type-1 or bare-metal hypervisor that enables a computer to run multiple operating systems simultaneously on the same hardware. A Type 1 hypervisor runs directly on the underlying computer’s physical hardware, interacting directly with its CPU, memory, and physical storage. For this reason, Type 1 hypervisors are also referred to as bare-metal hypervisors. A Type 1 hypervisor takes the place of the host operating system.
The pros of type-1 hypervisors lie in performance and security. It offerrs high performance because the hypervisor has direct access to the hardware. Security is also more reliable on type-1 than type-2, because there is no interface between the hypervisor and CPU.
Vulnerability details: Due to an oversight in the very original Spectre/Meltdown security work (XSA-254), one entrypath performs its speculation-safety actions too late.
In some configurations, there is an unprotected RET instruction which can be attacked with a variety of speculative attacks.
Impact: An attacker might be able to infer the contents of arbitrary host memory, including memory assigned to other guests.
Affected system: Xen versions 4.5 through 4.17 are vulnerable. Older versions are not vulnerable.
Official announcement: For details, please refer to the link – https://nvd.nist.gov/vuln/detail/CVE-2022-42331