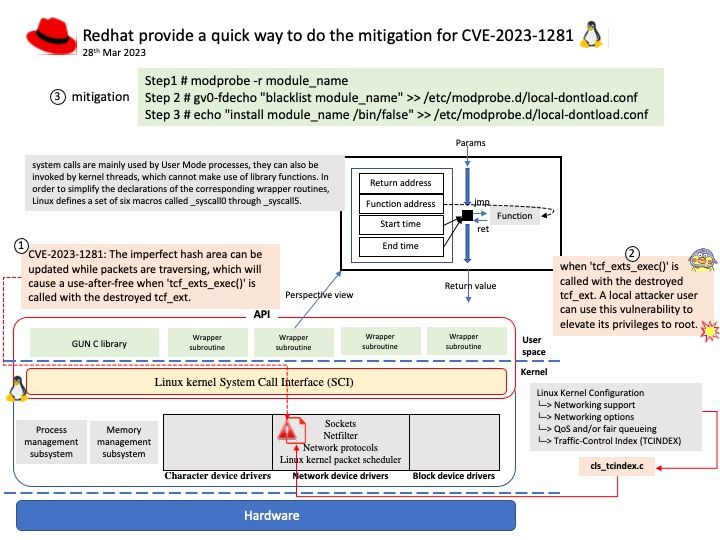
Preface: Use-After-Free (UAF) is a vulnerability related to incorrect use of dynamic memory during program operation. If after freeing a memory location, a program does not clear the pointer to that memory, an attacker can use the error to hack the program.
Background: Background: tcindex, traffic control index filter. This filter allows to match packets based on their tcindex field value, i.e. the combination of the DSCP and ECN fields as present in IPv4 and IPv6 headers.
SYNOPSIS:
tc filter … tcindex [ hash SIZE ] [ mask MASK ] [ shift SHIFT ] [ pas_on | fall_through ] [ classid CLASSID] [ action ACTION_SPEC ]
Vulnerability details: A use-after-free vulnerability was found in the traffic control index filter (tcindex) in the Linux kernel. The imperfect hash area can be updated while packets are traversing. This issue could allow a local attacker to cause a use-after-free problem, leading to privilege escalation.
Solution: How do I blacklist a kernel module to prevent it from loading automatically?
https://access.redhat.com/solutions/41278