Preface: The word Database, inspire you thinking a large volume of database. For example, a structured set of data held in a computer, especially one that is accessible in various ways. Do a transformation of design, bring the data which going to use to a specify memory. Compare to disk access storage, direct access to memory will be more faster. This is one of the modern strategy in big data analytic design solution.
Background: Running in-memory means requests for data do not require a trip to disk.
- What memory does Redis use? An empty instance uses ~ 3MB of memory. 1 Million small Keys -> String Value pairs use ~ 85MB of memory. 1 Million Keys -> Hash value, representing an object with 5 fields, use ~ 160 MB of memory.
In Ubuntu and other Linux distributions, the Redis database directory is /var/lib/redis .
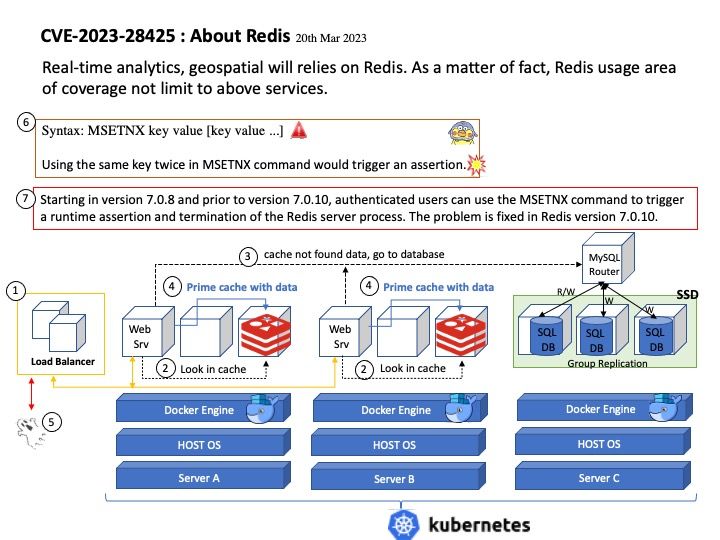
Vulnerability details: The vulnerability exists due to a reachable assertion when handling the MSETNX command. A remote attacker can send a specially crafted MSETNX command and perform a denial of service (DoS) attack.
Starting in version 7.0.8 and prior to version 7.0.10, authenticated users can use the MSETNX command to trigger a runtime assertion and termination of the Redis server process.
Solution: The problem is fixed in Redis version 7.0.10.
Official details: Please refer to NATIONAL VULNERABILITY DATABASE – https://nvd.nist.gov/vuln/detail/CVE-2023-28425