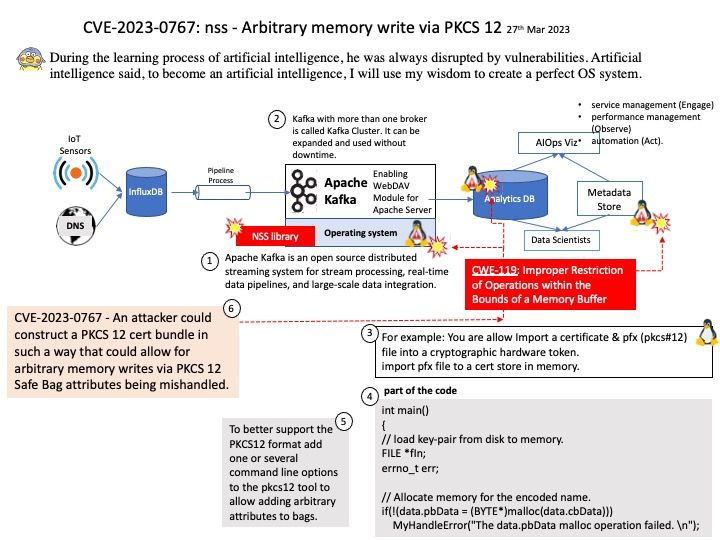
Preface: During the learning process of artificial intelligence, he was always disrupted by vulnerabilities. Artificial intelligence said, to become an artificial intelligence, I will use my wisdom to create a perfect OS system.
Background: Large scale of artificial intelligence structure especially machine learning may have a enterprise Linux system installed. The key component is shown as below:
Apache Kafka is an open source distributed streaming system for stream processing, real-time data pipelines, and large-scale data integration.
Kafka with more than one broker is called Kafka Cluster. It can be expanded and used without downtime. Apache Kafka Clusters are used to manage the persistence and replication of messages of data, so if the primary cluster goes down, other Kafka Clusters can be used to deliver the same service without any delay.
However if there is vulnerability occurs on Linux system. It will cause unforseen problem on the infrastructure.
Vulnerability details: CVE-2023-0767 – An attacker could construct a PKCS 12 cert bundle in such a way that could allow for arbitrary memory writes via PKCS 12 Safe Bag attributes being mishandled.
Firefox and Thunderbird in Red Hat Enterprise Linux 8.6 and later are not affected by this vulnerability, as they use the system NSS library. Firefox and Thunderbird in earlier Red Hat Enterprise Linux 8 extended life streams were affected, and should be updated to fixed versions as they become available.
Remark: To better support the PKCS12 format add one or several command line options to the pkcs12 tool to allow adding arbitrary attributes to bags.
Official announcement: For more details about the security issue(s), including the impact, a CVSS score, acknowledgments, and other related information, refer to the link – https://access.redhat.com/security/cve/CVE-2023-0767