Preface: In fact, by the time the vulnerability was released to the public, the design limitations and/or flaws had already been fixed. You may ask, what is the discussion space for the discovered vulnerabilities? As you know, an increasing number of vendors remain compliant with CVE policies, but the technical details will not be disclosed. If your focus is understanding, even if the vendor doesn’t release any details. You can learn about specific techniques as you learn. The techniques you learn can expand your horizons.
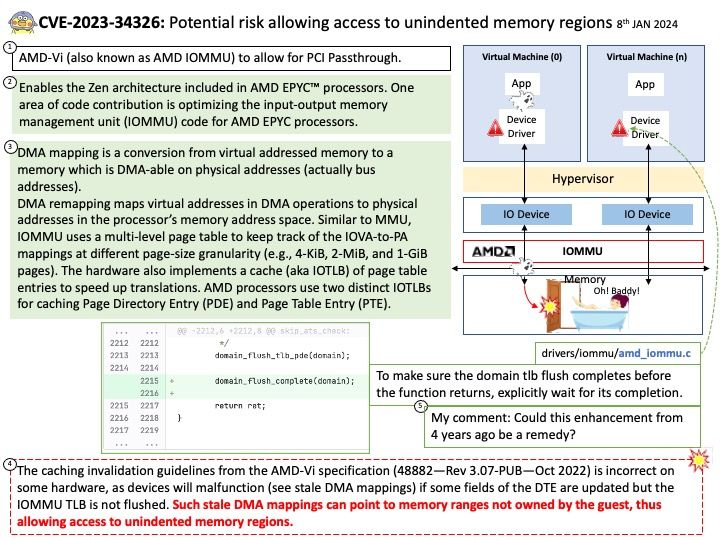
Background: AMD-Vi represents an I/O memory management unit (IOMMU) that is embedded in the chipset of the AMD Opteron 6000 Series platform. IOMMU is a key technology in extending the CPU’s virtual memory to GPUs to enable heterogeneous computing. AMD-Vi (also known as AMD IOMMU) to allow for PCI Passthrough.
DMA mapping is a conversion from virtual addressed memory to a memory which is DMA-able on physical addresses (actually bus addresses).
DMA remapping maps virtual addresses in DMA operations to physical addresses in the processor’s memory address space. Similar to MMU, IOMMU uses a multi-level page table to keep track of the IOVA-to-PA mappings at different page-size granularity (e.g., 4-KiB, 2-MiB, and 1-GiB pages). The hardware also implements a cache (aka IOTLB) of page table entries to speed up translations.
AMD processors use two distinct IOTLBs for caching Page Directory Entry (PDE) and Page Table Entry (PTE) (AMD, 2021; Kegel et al., 2016).
Ref: If your application scenario does not require virtualization, then disable AMD Virtualization Technology. With virtualization disabled, also, disable AMD IOMMU. It can cause differences in latency for memory access. Finally, also disable SR-IOV.
Vulnerability details: The caching invalidation guidelines from the AMD-Vi specification (48882—Rev 3.07-PUB—Oct 2022) is incorrect on some hardware, as devices will malfunction (see stale DMA mappings) if some fields of the DTE are updated but the IOMMU TLB is not flushed. Such stale DMA mappings can point to memory ranges not owned by the guest, thus allowing access to unindented memory regions.
Official announcement: Please refer to the link for details – https://nvd.nist.gov/vuln/detail/CVE-2023-34326