Preface: According to news in October 2023, experts speculated that commercial spyware exploited a security vulnerability in the Arm Mali GPU driver to compromise some people’s devices. The vulnerability was claimed to be a local attack. But how do attacker plant malware on a smartphone without remote access? Hard to say! Phishing and social engineering techniques may be involved.
Background: About four years ago, the mainstream GPUs are PowerVr, Mali, and Adreno (Qualcomm). Apple used a customized version of PowerVr in the early days. However, as Apple develops its own GPU, PowerVr software design now owned by Canyon Bridge Capital Partners. Mali is the graphics acceleration IP of ARM. Mali is actually ARM’s Mali series IP core.
The first version of the Mali microarchitecture is called Utgard. Later there were versions called Midgard (second generation), Bifrost (third generation), and Valhall (fourth generation). Valhall was launched in the second quarter of 2019. The main series are Mali-G57 and Mali-G77.
However, commercial spyware has exploited a security hole in Arm’s Mali GPU drivers to compromise some people’s devices, according to news from Oct 2023.
ARM decided last September (2023) not to disclose any details of CVE-2023-5091 to the public. The official announcement published on January 8, 2024 finally.
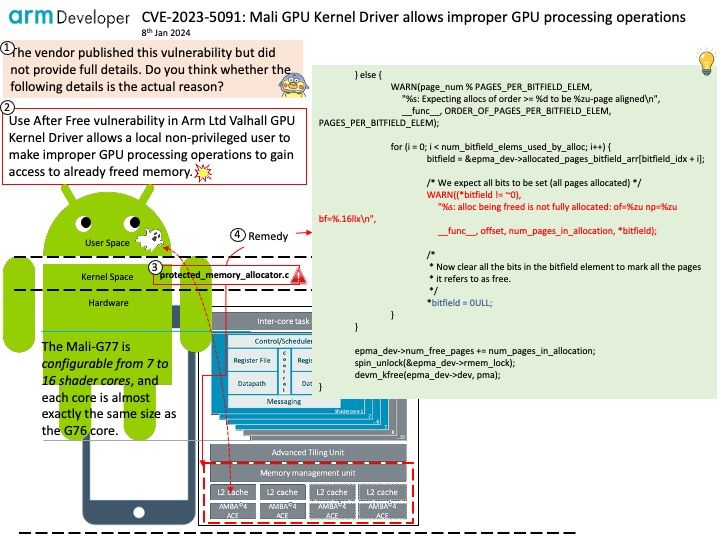
Vulnerability details: Use After Free vulnerability in Arm Ltd Valhall GPU Kernel Driver allows a local non-privileged user to make improper GPU processing operations to gain access to already freed memory. This issue affects Valhall GPU Kernel Driver: from r37p0 through r40p0.
Official announcement: Please refer to the link for details – https://nvd.nist.gov/vuln/detail/CVE-2023-5091