Preface: The biggest advantage for Android is actually in hardware, not software. The best part of Android platform is that it is flexible in accommodating third party applications which facilitates the Android user to add more functionality in his/her mobile device.
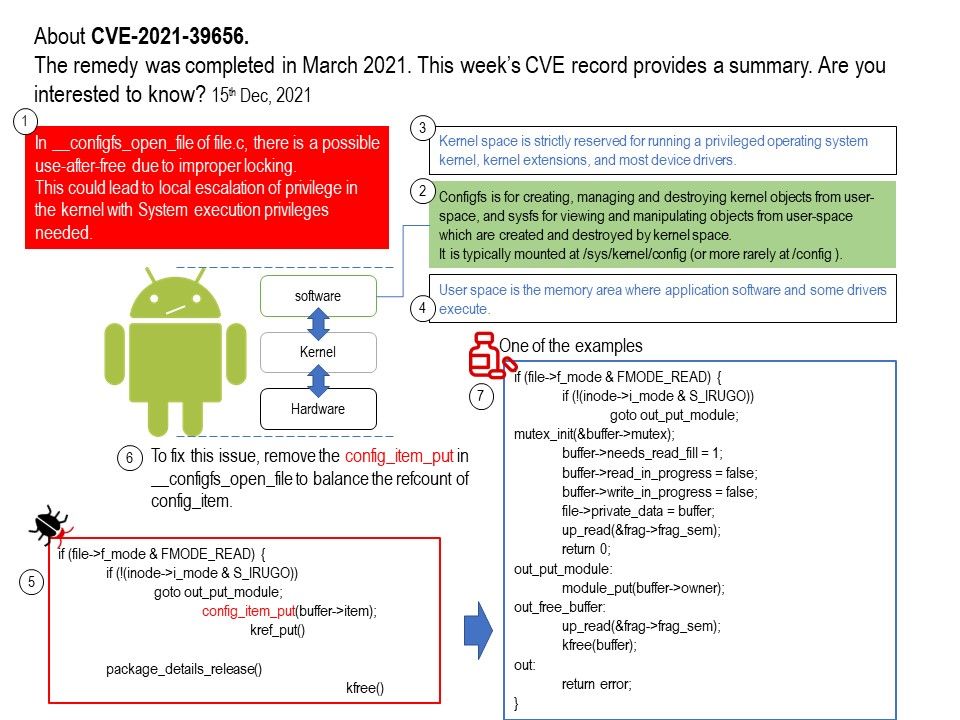
Background: Configfs is a ram-based filesystem that provides the converse of sysfs’s functionality. Where sysfs is a filesystem-based view of kernel objects, configfs is a filesystem-based manager of kernel objects, or config_items.
Both sysfs and configfs can and should exist together on the same system. One is not a replacement for the other.
Privileged or kernel mode is the processing mode that allows code to have direct access to all hardware and memory in the system. Kernel mode means when any process or program wants to use any functionality controlled by Operating System, so in that case,
we make a system call to execute any particular set of instructions stored in O.S. So these set of instructions are executed in Kernel mode.
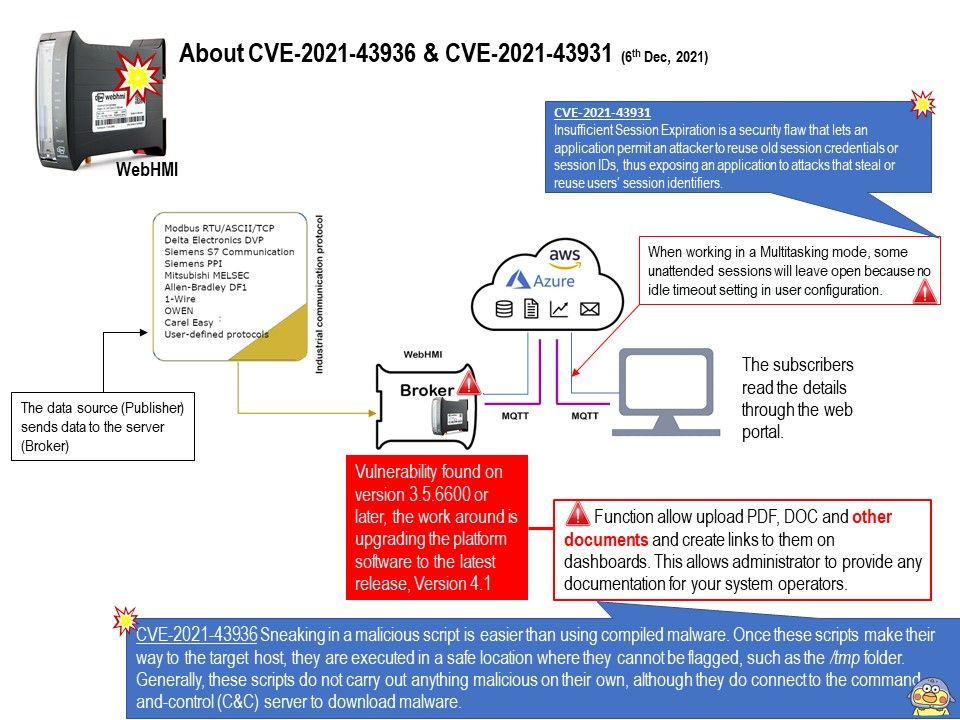
Vulnerability details: About CVE-2021-39656, .The remedy was completed in March 2021. This week’s CVE record provides a summary (see below):
In __configfs_open_file of file[.]c, there is a possible use-after-free due to improper locking. This could lead to local escalation of privilege in the kernel with System execution privileges needed.
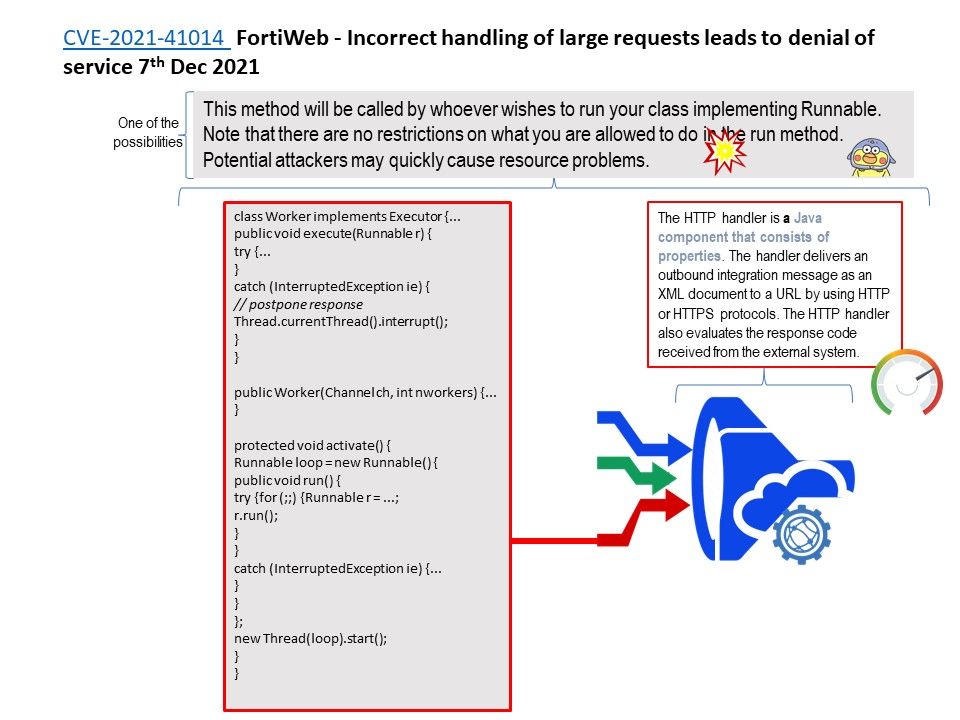
Remedy: To fix this issue, remove the config_item_put in __configfs_open_file to balance the refcount of config_item. Please refer to the attached picture for details.
Official announcement: https://android.googlesource.com/kernel/common/+/14fbbc8297728e880070f7b077b3301a8c698ef9
.jpg)