Preface: CISA Releases Security Advisory on WebHMI Vulnerabilities – https://us-cert.cisa.gov/ics/advisories/icsa-21-336-03
Background: The company Distributed Data Systems LLC is well-known in Ukraine and abroad for products with WebHMI and 7bit brands for remote monitoring and control of industrial equipment in Industry 4.0 format.
Remark: 7Bit ModBus Proxy is a caching gateway from ModBus TCP protocol to Modbus RTU.
SCADA is a powerful control system that is designed to collect, analyze, and visualize data from industrial equipment. Web-based HMIs allow users to monitor and control devices and processes at a distance. WebHMI is a SCADA-system with built-in web server that allows you to monitor and control any automation system on the local network and via the Internet from your computer and mobile devices.
Vulnerability details: The WebHMI itself encountered two different vulnerabilities includes Authentication Bypass by Primary Weakness and Unrestricted Upload of File with Dangerous Type.
CVE-2021-43931 The authentication algorithm of the WebHMI portal is sound, but the implemented mechanism can be bypassed as the result of a separate weakness that is primary to the authentication error.
CVE-2021-43936 The software allows the attacker to upload or transfer files of dangerous types to the WebHMI portal, that may be automatically processed within the product’s environment or lead to arbitrary code execution.
The following information is our speculation on the cause of the vulnerabilities.
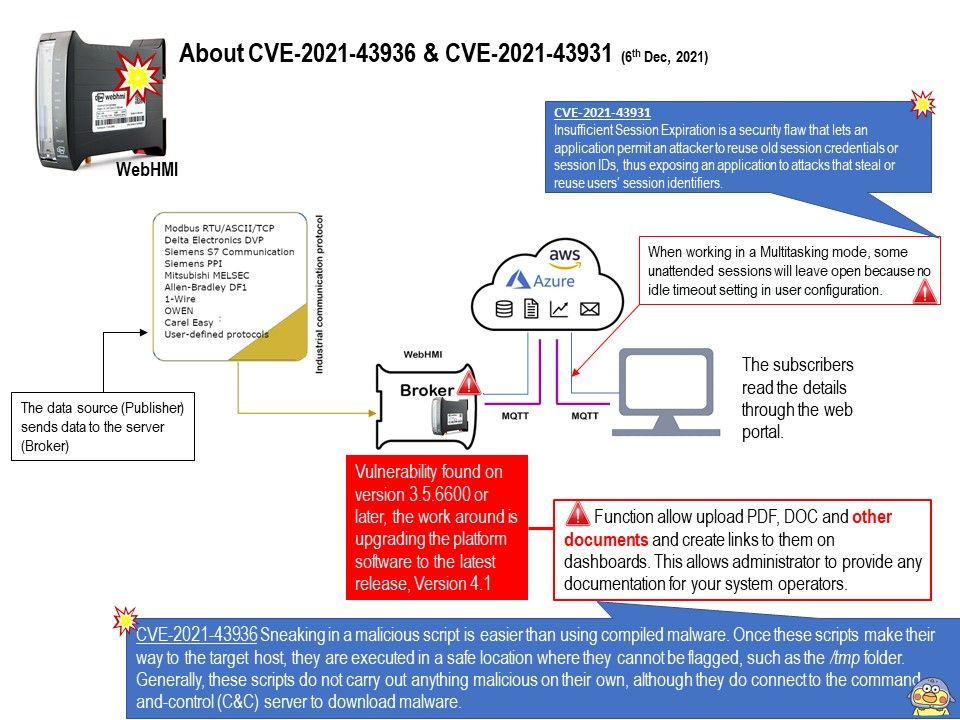
CVE-2021-43931 – Insufficient Session Expiration is a security flaw that lets an application permit an attacker to reuse old session credentials or session IDs, thus exposing an application to attacks that steal or reuse users’ session identifiers.
CVE-2021-43936 – Sneaking in a malicious script is easier than using compiled malware. Once these scripts make their way to the target host, they are executed in a safe location where they cannot be flagged, such as the /tmp folder. Generally, these scripts do not carry out anything malicious on their own, although they do connect to the command-and-control (C&C) server to download malware.