Preface: dlopen() The function dlopen() loads the dynamic shared object (shared library) file named by the null-terminated string filename and returns an opaque “handle” for the loaded object.
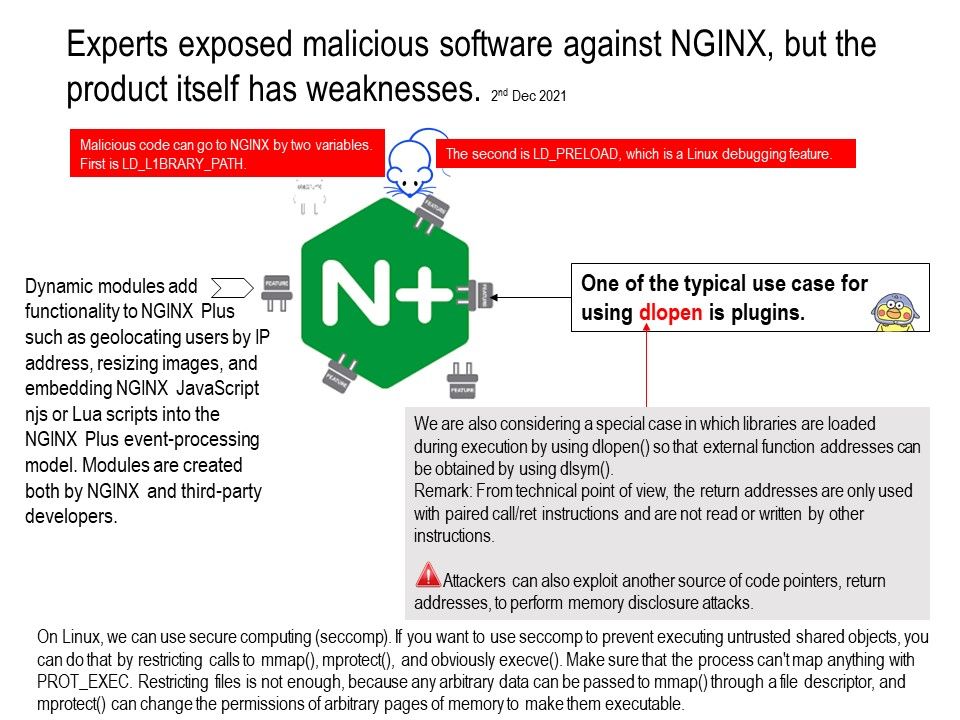
Background: NGINX Plus provides a supported and tested version.Starting at $2500 per year. NGINX is an open source software. Dynamic modules add functionality to NGINX Plus such as geolocating users by IP address, resizing images and embedding NGINX JavaScript njs or Lua scripts into the NGINX Plus event‑processing model.
Modules are created both by NGINX and third‑party developers.
NGINX, at its core, is a collection of modules. Whether you are using core modules, like the http and stream modules. Or 3rd party module, like geoip or RTMP, they are using the same module framework.
With the addition of dynamic module support, modules are an even better way to add functionality to NGINX.
Details of attack: A new parasitic malware targets the popular Nginx web server, Sansec discovered. This novel code injects itself into a host Nginx application and is nearly invisible. For more details, please refer to the link – https://sansec.io/research/nginrat
Observation: We are also considering a special case in which libraries are loaded during execution by using dlopen() so that external function addresses can be obtained by using dlsym().
Remark: From technical point of view, the return addresses are only used with paired call/ret instructions and are not read or written by other instructions.
However, attackers can also exploit another source of code pointers, return addresses, to perform memory disclosure attacks.