Preface: Vendor vulnerability management program sometimes have doubt to public. They frequent ask, how to do the protection before patch release? Perhaps not require worry too much because zero-day vulnerabilities are go with us all the time.
Synopsis: On October 2019, Oracle has released its Critical Patch Update for October 2019 to address 219 vulnerabilities across multiple products. Perhaps FasterXML jackson-databind vulnerability bring my focus. Because this vulnerability was announced to public on August this year.
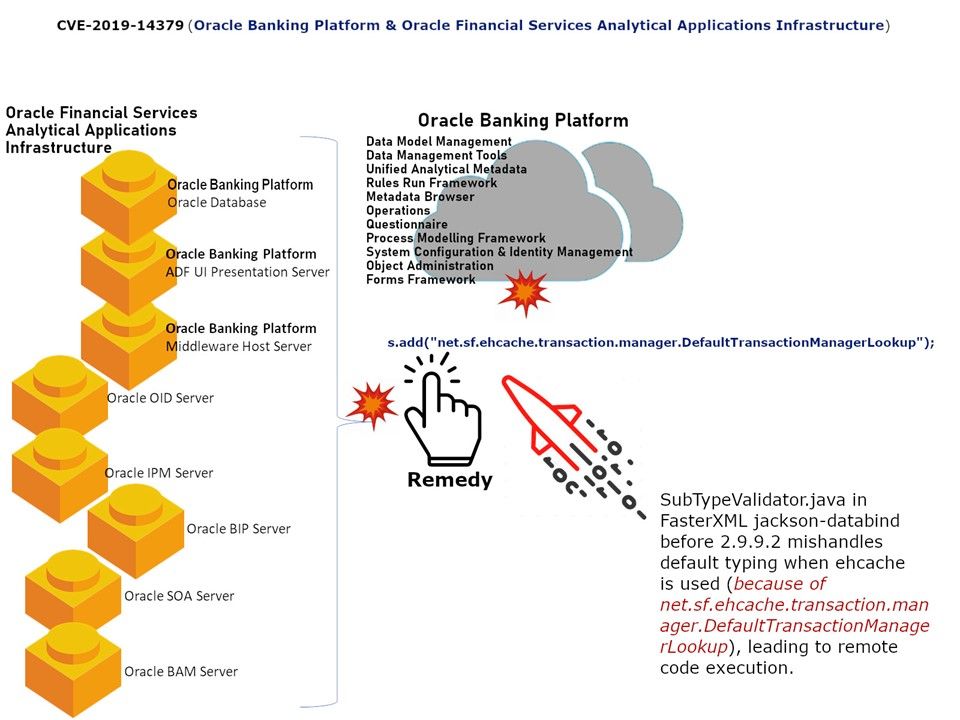
Vulnerability details: Banking finance business analyser will be familiar with OFSAA. OFSAA out of the box data models continue to be released as Erwin. But it supports Oracle SQL modeler for data model extensions.However the CVE-2019-14379 design weakness has been found on Oracle Banking Platform and Oracle Financial Services Analytical Applications Infrastructure. Data binding is useful for allowing user input to be dynamically bound to the domain model of an application (or whatever objects you use to process user input). SubTypeValidator.java in FasterXML jackson-databind before 2.9.9.2 mishandles default typing when ehcache is used (because of net.sf.ehcache.transaction.manager.DefaultTransactionManagerLookup), leading to remote code execution.
What is Fasterxml Jackson Databind?
Contains basic mapper (conversion) functionality that allows for converting between regular streaming json content and Java objects (beans or Tree Model: support for both is via ObjectMapper class, as well as convenience methods included in JsonParser. For more details of oracle security advisory details, please refer to url: https://www.oracle.com/technetwork/security-advisory/cpuoct2019-5072832.html