Preface: Why some people want everything fast. But when a man is having dinner with his girlfriend, he hopes that time will be slower.
5G communication background: In April 2008, NASA partnered with Geoff Brown and Machine-to-Machine Intelligence (M2Mi) Corp to develop 5G communications technology.
As times go by, On 3 April 2019, South Korea became the first country to adopt 5G.
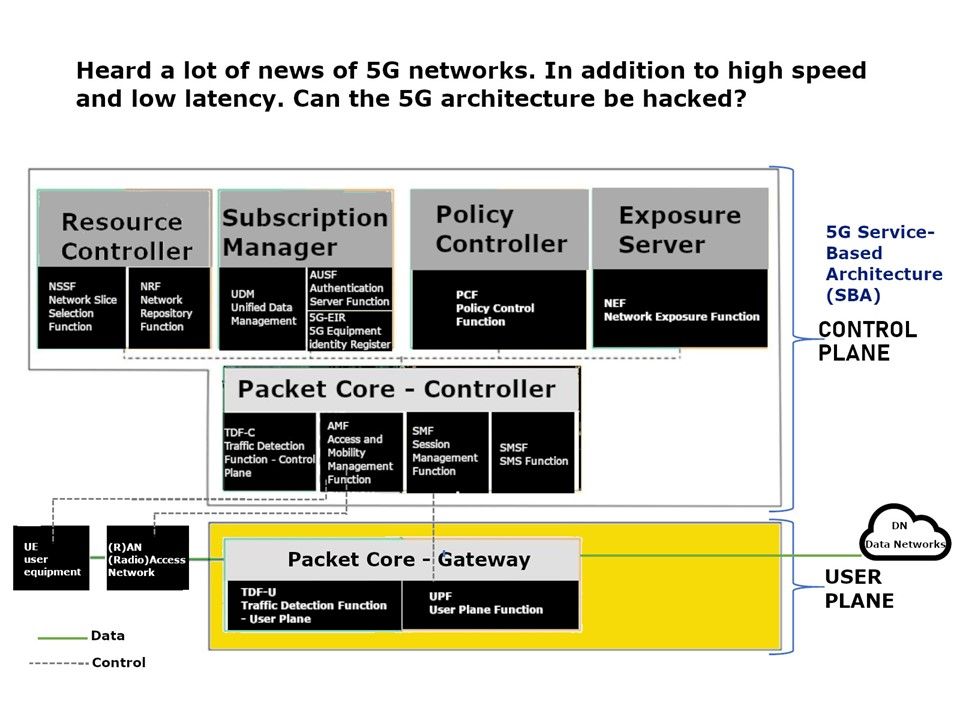
Heard a lot of news of 5G technology. In additional to high speed and low latency. Can the 5G architecture be hacked?
5G is the first generation that was designed with virtualization and cloud-based technology. Nokia said building separate systems to meet future requirements and use cases of 5G was not an option, so the future network needed to be integrated and aligned with software-defined functions, cognitive technology to orchestrate it and distributed content and processing. 5G’s future rests on software-defined networking (SDN), whose main concept is to decouple the infrastructure of wireless networks from expensive, closed hardware and shift it to an intelligent software layer running on commodity hardware. However, software-defined functions are vulnerable to security threats as well. One of the most significant security risk factors is the possibility of a compromised SDN controller attack at the control plane layer. Due to the centralization design of the SDN, the SDN controller becomes the brain of the SDN architecture. Attackers can focus on compromising the SDN controller in an attempt to manipulate the entire network.
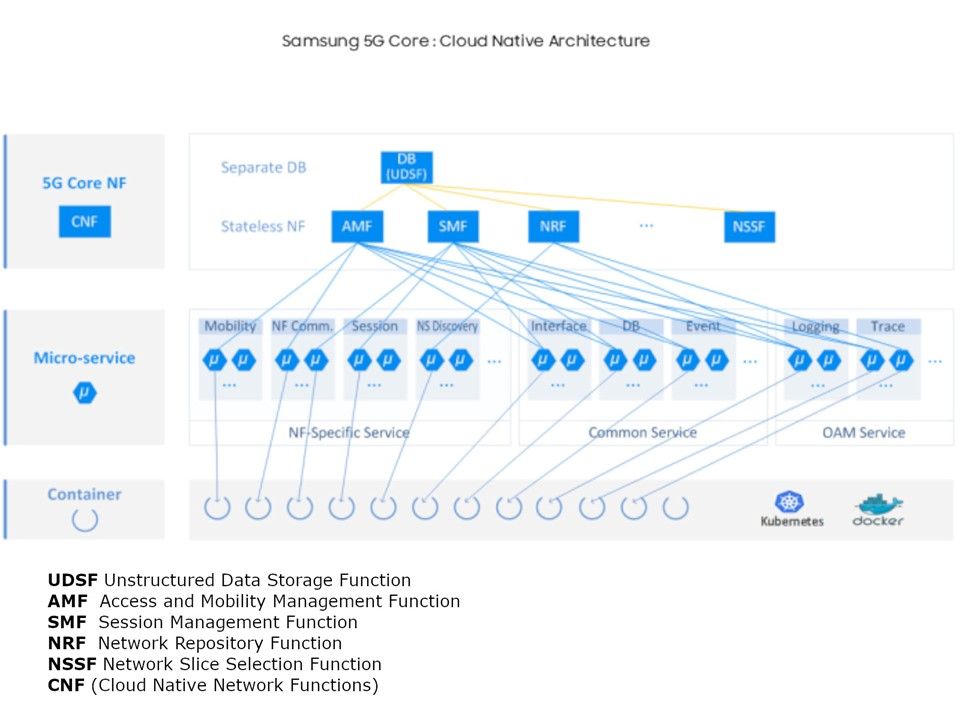
Perhaps above prediction was true. Samsung 5G Core NFs are cloud native NFs, which consist of container-based micro-services to enable flexible scaling and upgrade to meet telecom operators’ requirements. For more details, please refer below diagram.
Besides, 5G Service-Based Architecture (SBA) components consists of serveral components (Resource Controller, Subscription Manager, Policy Controller and Exposure Server). The interconnect in between packet core controller to above four different components could make use of HTTP/JSON. From security point of view , it is hard to forseen that this type of interconnection whether will encounter vulnerability in future.
On demand patch management in existing information technology world will be extend to 5G network in future.
Docker and Kubernetes become a main trend in technology world. Both products features can improve the redundancy and fault tolerance level of the system. And therefore it is hard to avoid the 5G services provider install similar architecture. APT attack and ransomware will wreak havoc with cyber world. In order to reduce the the zero-day of attack to Docker and Kubernetes environment. System hardening process and access control policy must be take in this place. So the 5G service based architecture system will be the new hacker target soon.
Summary: The above description is only cover a small part of the 5G network. Let us observe what will happen to the mobile communication world?