Preface: The heap is the portion of memory where dynamically allocated memory resides (i.e. memory allocated via malloc ).
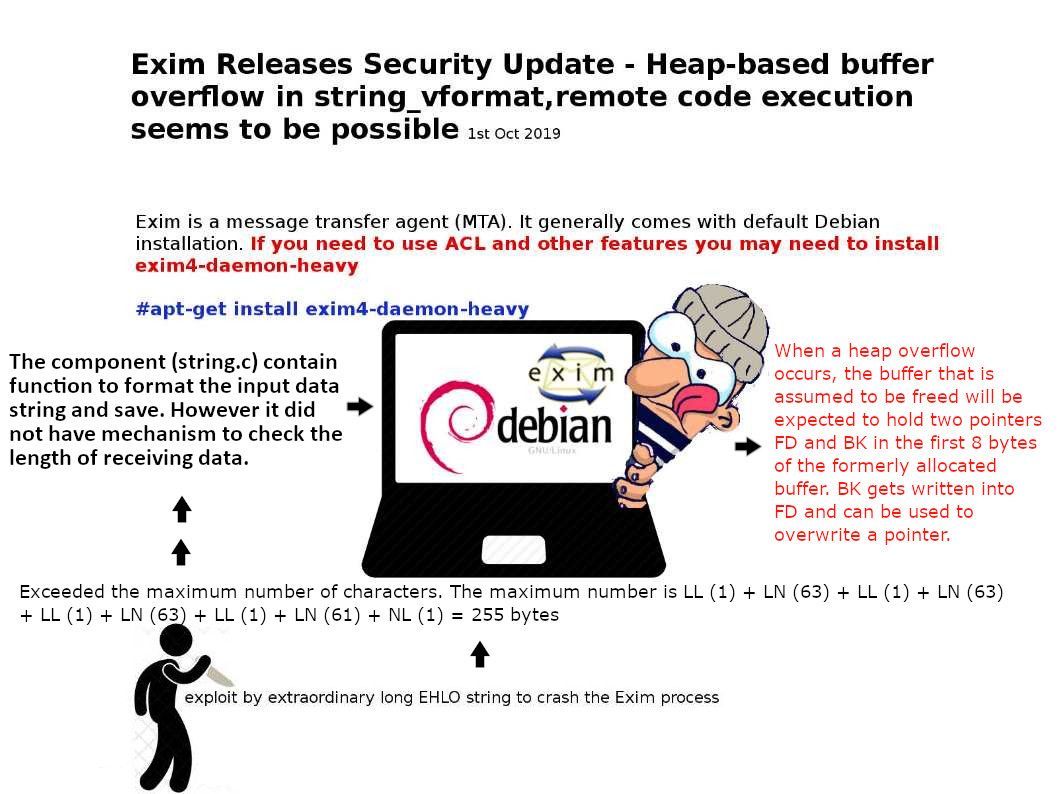
Background: Exim is a message transfer agent (MTA). It generally comes with default Debian installation. If you need to use ACL and other features you may need to install exim4-daemon-heavy (see below):
– apt-get install exim4-daemon-heavy
Vulnerability details: The heap is the portion of memory where dynamically allocated memory resides (i.e. memory allocated via malloc ). The component (string.c) contain function to format the input data string and save. However it did not have mechanism to check the length of receiving data. As a result, it trigger a heap base buffer overflow by a extraordinary long EHLO string. The attacker have to find out which unlink() he can “reuse” in glibc. From technical point of view, Unlink() is the classic and probably the simplest one. In short attacker can overwrite arbitrary 4 bytes at two specified places (FD & BK)! This is more than enough to redirect the control flow.
Reference: Maximum length of a DNS name – Exceeded the maximum number of characters. The maximum number is LL (1) + LN (63) + LL (1) + LN (63) + LL (1) + LN (63) + LL (1) + LN (61) + NL (1) = 255 bytes
Remedy: No known mitigation. End user must download and build the fixed version 4.92.3