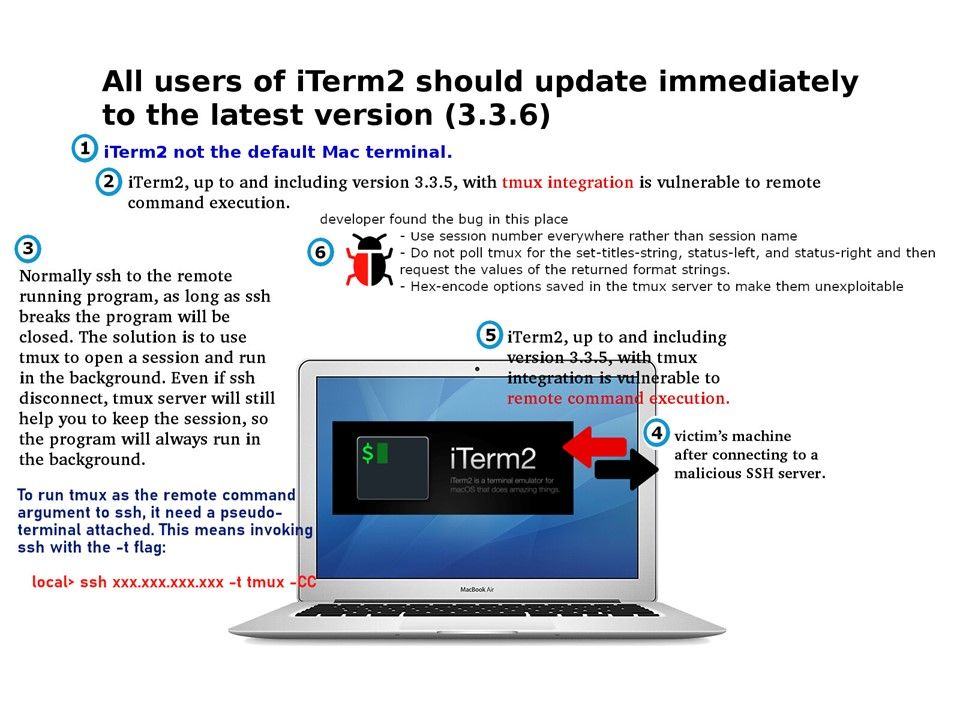
Preface: iTerm2 not the default Mac terminal
Vulnerability details: A vulnerability, identified as CVE-2019-9535, exists in the way that iTerm2 integrates with tmux’s control mode, which may allow an attacker to execute arbitrary commands by providing malicious output to the terminal. This affects versions of iTerm2 up to and including 3.3.5.
Technical background: iTerm2 with tmux integration since version 3.3.5. The powerful feature of Tmux is able to run tmux as the remote command argument to ssh. Meanwhile Tmux is a terminal multiplexer. Simply put, this allows you to split one terminal session into many.
Remedy: Developer take the following actions:
- Use session number everywhere rather than session name
- Do not poll tmux for the set-titles-string, status-left, and status-right and then request the values of the returned format strings.
- Hex-encode options saved in the tmux server to make them unexploitable
Update iTerm2 to version 3.3.6, which includes mitigations against exploitation of this vulnerability.