Preface: Who uses RSA’s BSAFE library? BSAFE uses Dual_EC_DRBG as its default pseudorandom number generator. Dual_EC_DRBG let people hesitation because the algorithm that is suspected to contain a NSA backdoor.
Product background: The Crypto-C ME software development toolkit is designed to enable developers to incorporate cryptographic technologies into applications. Crypto-C ME security software helps to protect sensitive data as it is stored, using strong encryption techniques to ease integration with existing data models.
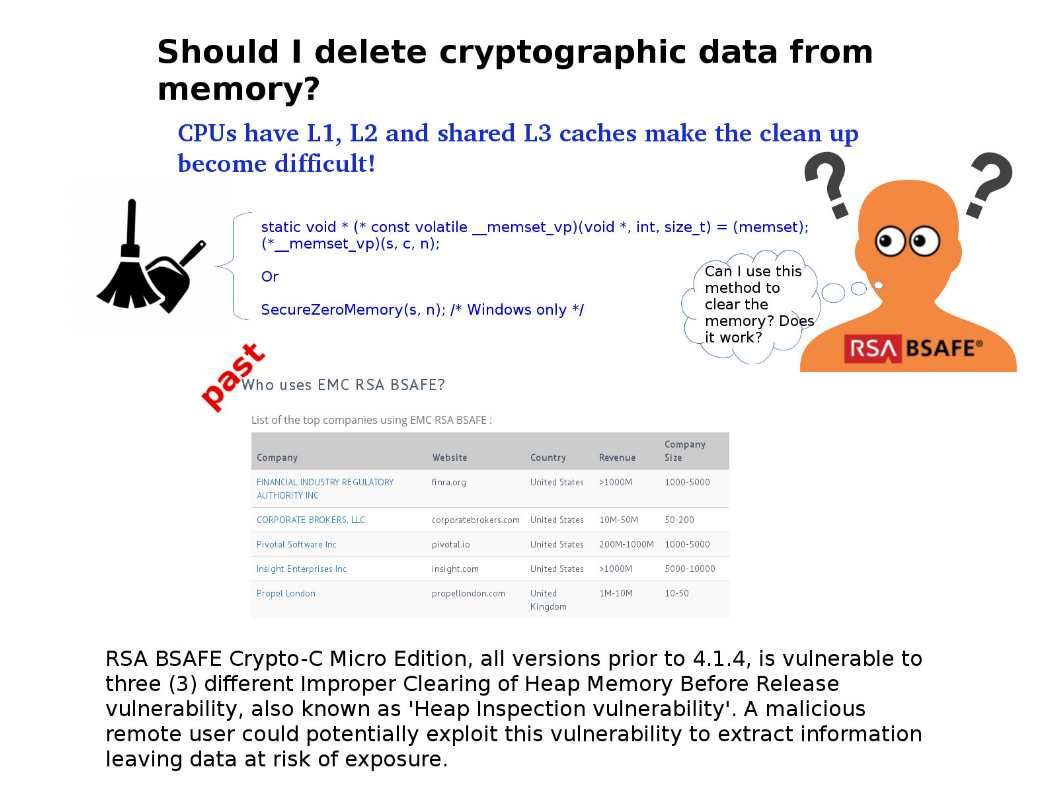
Vulnerability details: RSA BSAFE Crypto-C Micro Edition, all versions prior to 4.1.4, is vulnerable to three (3) different Improper Clearing of Heap Memory Before Release vulnerability, also known as ‘Heap Inspection vulnerability’. A malicious remote user could potentially exploit this vulnerability to extract information leaving data at risk of exposure.
Additional information: For insatnce, if you software application written in CPython. So you have to implement your own data type in C and wipe memory in its deallocation function. Since BSAFE is one of the oldest cryptography libraries and therefore the original design not contain this clean up function in memory.
Vendor announcement (Reference URL): https://www.dell.com/support/security/zh-hk/details/DOC-107000/DSA-2019-079-RSA-BSAFE®-Crypto-C-Micro-Edition-and-Micro-Edition-Suite-Multiple-Security-Vulnerab