Preface: Before the earthquake, many special phenomena will awaken people. Does a similar situation apply to cybersecurity attacks, especially APT?
Security focus: NSA has announcement a day ago. They urge the company must be extra care of vulnerabilities in Multiple VPN Applications. Are you interested of this article? Following URL can provide the details. https://media.defense.gov/2019/Oct/07/2002191601/-1/-1/0/CSA-MITIGATING-RECENT-VPN-VULNERABILITIES.PDF
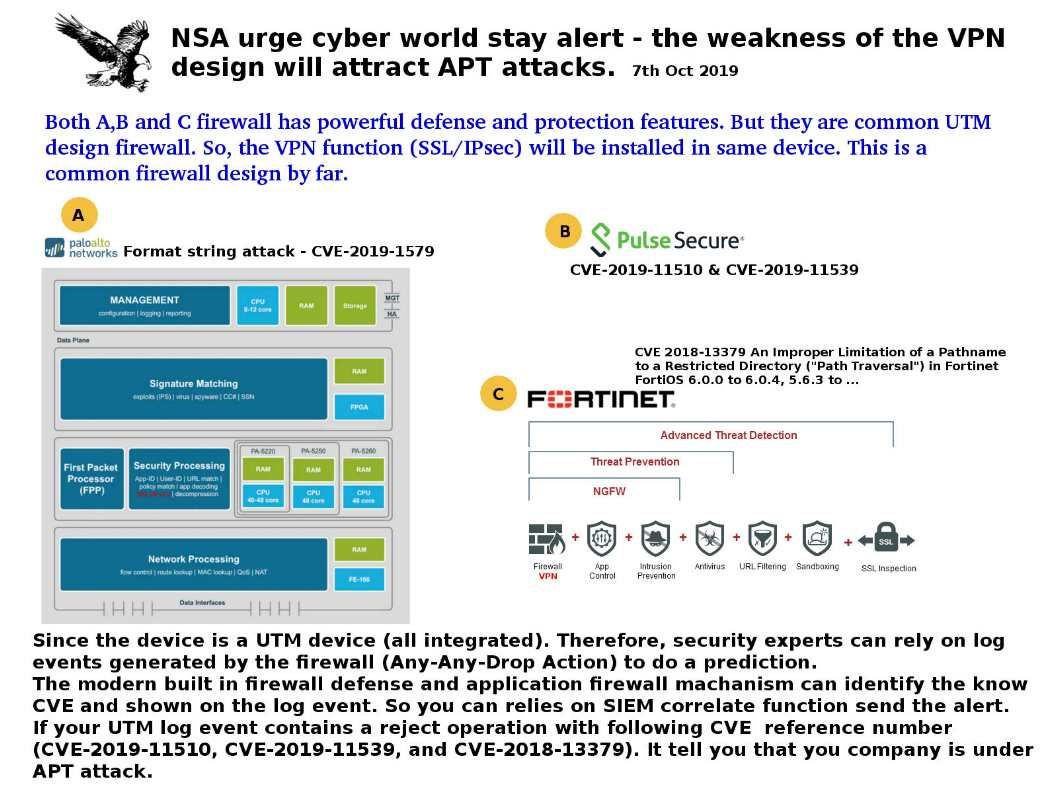
Additional information: UTM is a common firewall design by far. Different kind of services are all in one box. Since the device is a UTM device (all integrated). Therefore, security experts can rely on log events generated by the firewall (Any-Any-Drop Action) to do a prediction.
The modern built in firewall defense and application firewall mechanism can identify the know CVE and shown on the log event. So you can relies on SIEM correlate function send the alert.
If your UTM log event contains a reject operation with following CVE reference number (CVE-2019-11510, CVE-2019-11539, and CVE-2018-13379). It tell you that your company is under APT attack.
What is the next action when above scenario occurs? You should activate the escalation procedure immediately.