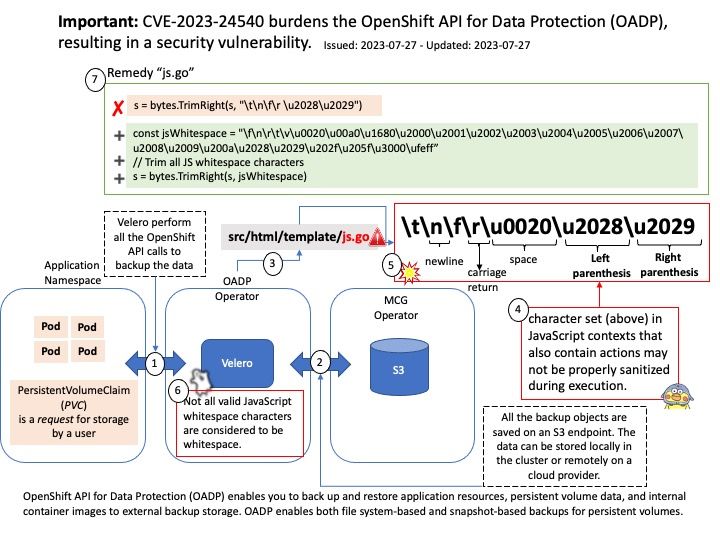
Preface: Not all valid JavaScript whitespace characters are considered to be whitespace. Templates containing whitespace characters outside of the character set “\t\n\f\r\u0020\u2028\u2029” in JavaScript contexts that also contain actions may not be properly sanitized during execution (CVE-2023-24540)
Background: OpenShift API for Data Protection (OADP) enables you to back up and restore application resources, persistent volume data, and internal container images to external backup storage. OADP enables both file system-based and snapshot-based backups for persistent volumes.
OADP backs up Kubernetes/OpenShift objects and internal images by saving them as an archive file on object storage. OADP backs up persistent volumes (PVs) by creating snapshots. You can restore all objects in a backup or filter the restored objects by namespace, PV, or label. You can schedule backups at specified intervals.
The default OADP plugins enable Velero, a tool that’s used to integrate with certain cloud providers and to back up and restore OpenShift Container Platform resources.
Security Fix(es) from Bugzilla:
- golang: html/template: improper handling of JavaScript whitespace (CVE-2023-24540)
Affected Products
- OpenShift API for Data Protection 1 x86_64
Fixes
- BZ – 2196027 – CVE-2023-24540 golang: html/template: improper handling of JavaScript whitespace
- OADP-1504 – oadp-1.0: Restoring pod using image from openshift build randomly ImagePullBackoff