Preface: NET 5 and [.] NET 6 are supported on multiple operating systems, including Windows, Linux, Android, iOS /tvOS, and macOS. The only difference is that[ .] NET 6 is further supported on Windows Arms64 and macOS Apple Silicon while .
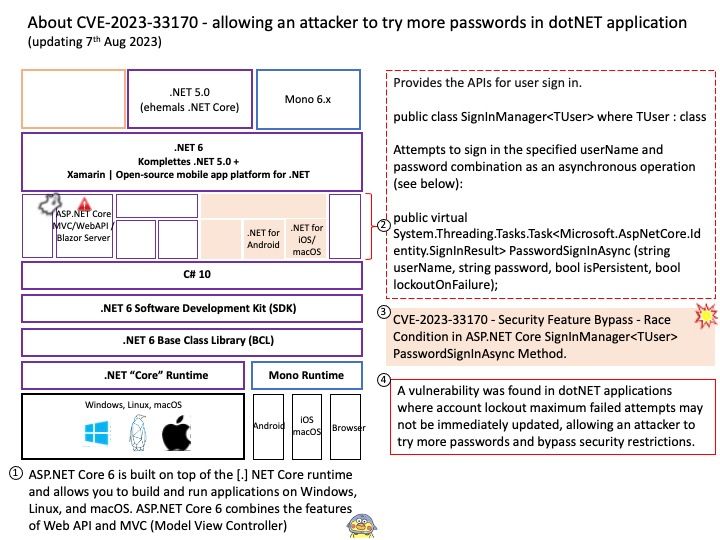
Background: ASP[.]NET Core 6 is built on top of the [.] NET Core runtime and allows you to build and run applications on Windows, Linux, and macOS. ASP[.]NET Core 6 combines the features of Web API and MVC.
Red Hat Enterprise Linux (RHEL) 8 and later .NET 6 is capable for the IBM Z and LinuxONE (s390x) architectures, along with AMD and Intel (x64_64) and ARM (aarch64). IBM Z and LinuxONE is fully enabled throughout all .NET core components with the Mono runtime available (currently no CoreCLR support).
Vulnerability details: A vulnerability was found in dotNET applications where account lockout maximum failed attempts may not be immediately updated, allowing an attacker to try more passwords and bypass security restrictions. This flaw allows a remote attacker to bypass security features, causing an impact on confidentiality, integrity, and availability.
CVE-2023-33170 – Security Feature Bypass – Race Condition in ASP.NET Core SignInManager PasswordSignInAsync Method.
Official announcement: For details, please refer to the link – https://nvd.nist.gov/vuln/detail/CVE-2023-33170