Preface: The company was founded in 2007. MobileIron, he is early pioneer in mobile security and management for smartphones and tablet computers, such as iPhone, iPad, Android…etc.
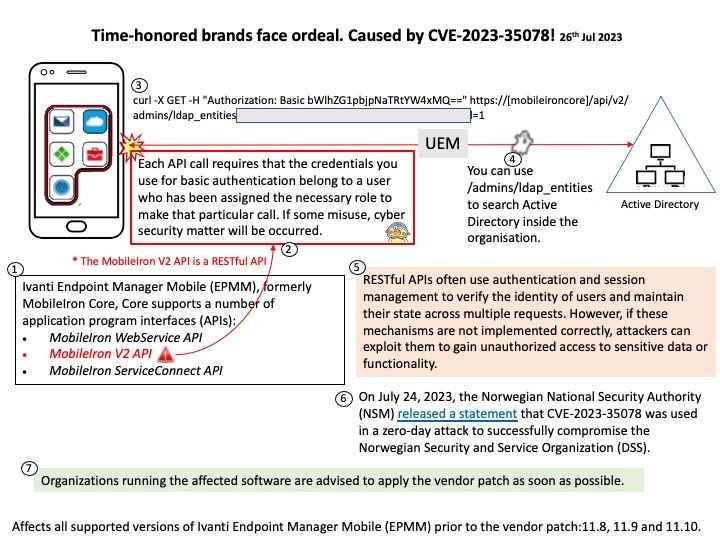
Background: Core supports a number of application program interfaces (APIs):
- MobileIron WebService API
- MobileIron V2 API
- MobileIron ServiceConnect API
The MobileIron V2 API is a RESTful API you use to send HTTPS requests to get data from and provide data to MobileIron. The MobileIron V2 API requires basic authentication to authorize API calls. Each API call requires that the credentials you use for basic authentication belong to a user who has been assigned the necessary role to make that particular call. If some misuse, cyber security matter will be occurred.
Vulnerability details: Ivanti Endpoint Manager Mobile (EPMM), formerly MobileIron Core, through 11.10 allows remote attackers to obtain PII, add an administrative account, and change the configuration because of an authentication bypass, as exploited in the wild in July 2023.
Ref: RESTful APIs often use authentication and session management to verify the identity of users and maintain their state across multiple requests. However, if these mechanisms are not implemented correctly, attackers can exploit them to gain unauthorized access to sensitive data or functionality.
Official details: For details, please refer to the link – https://nvd.nist.gov/vuln/detail/CVE-2023-35078