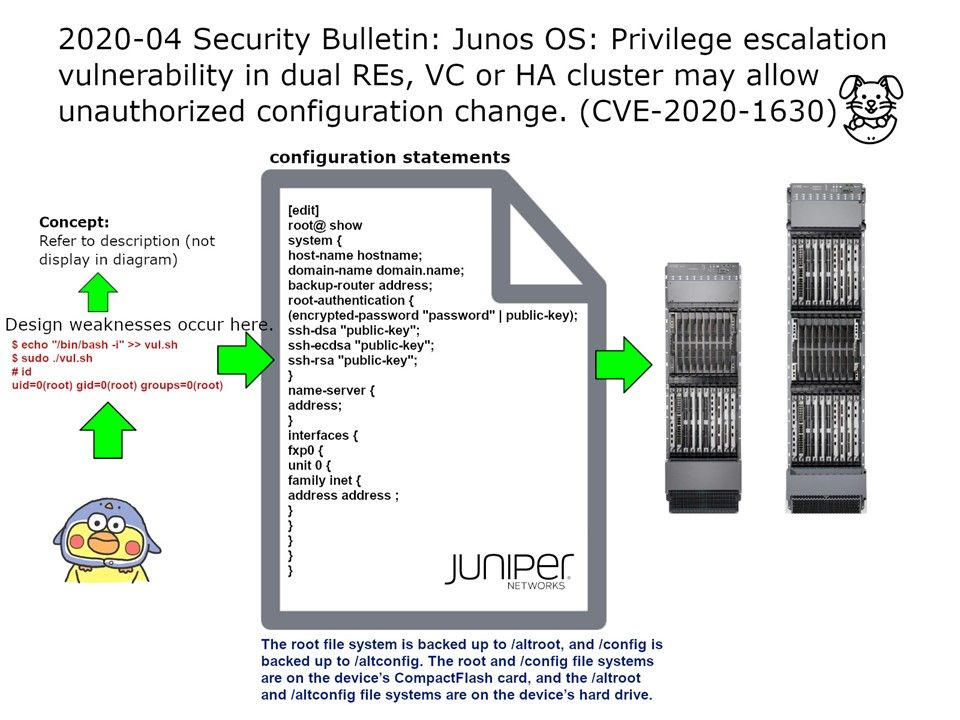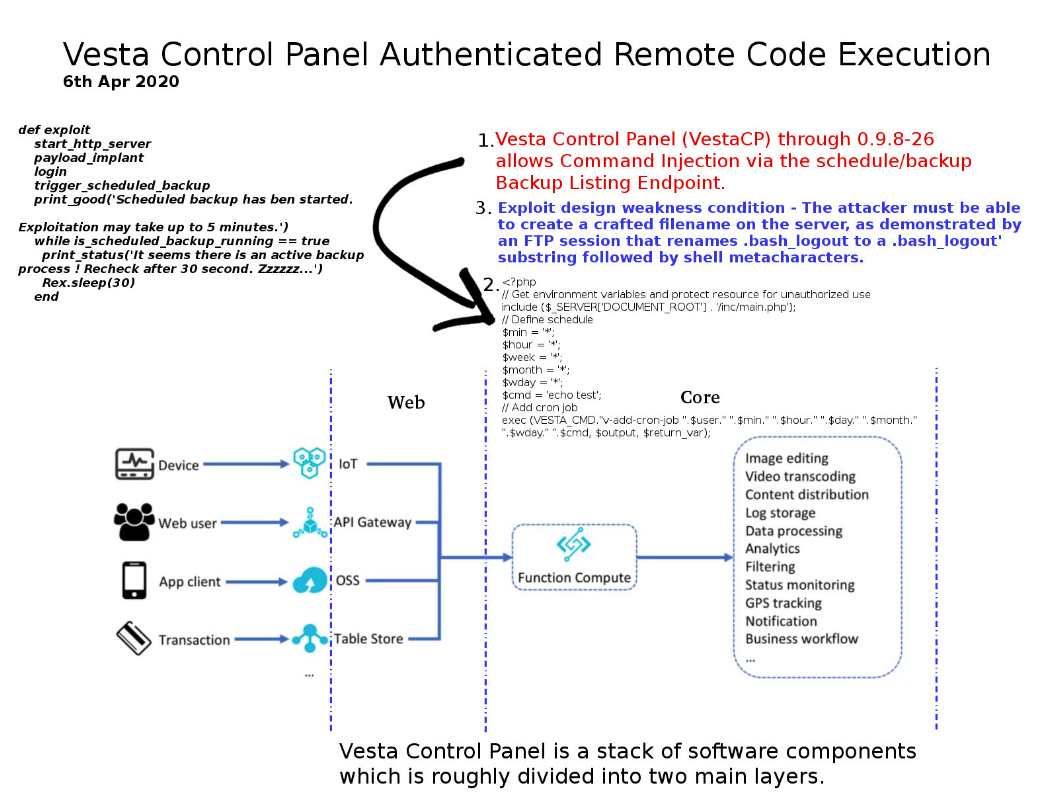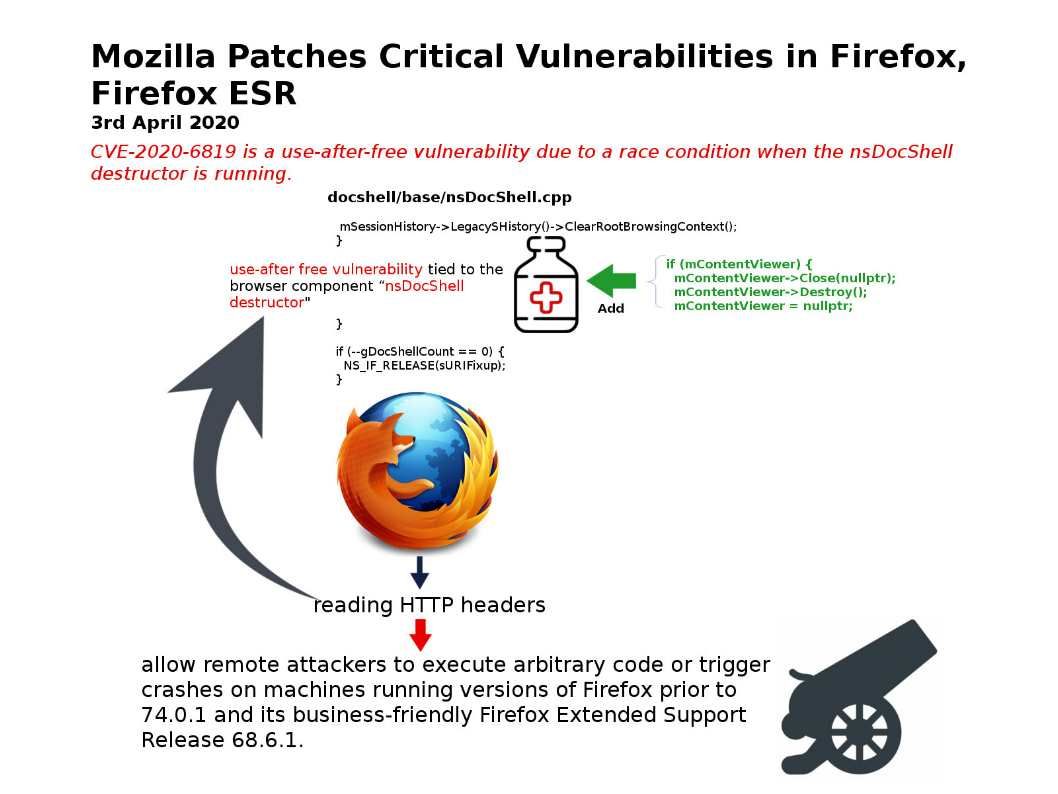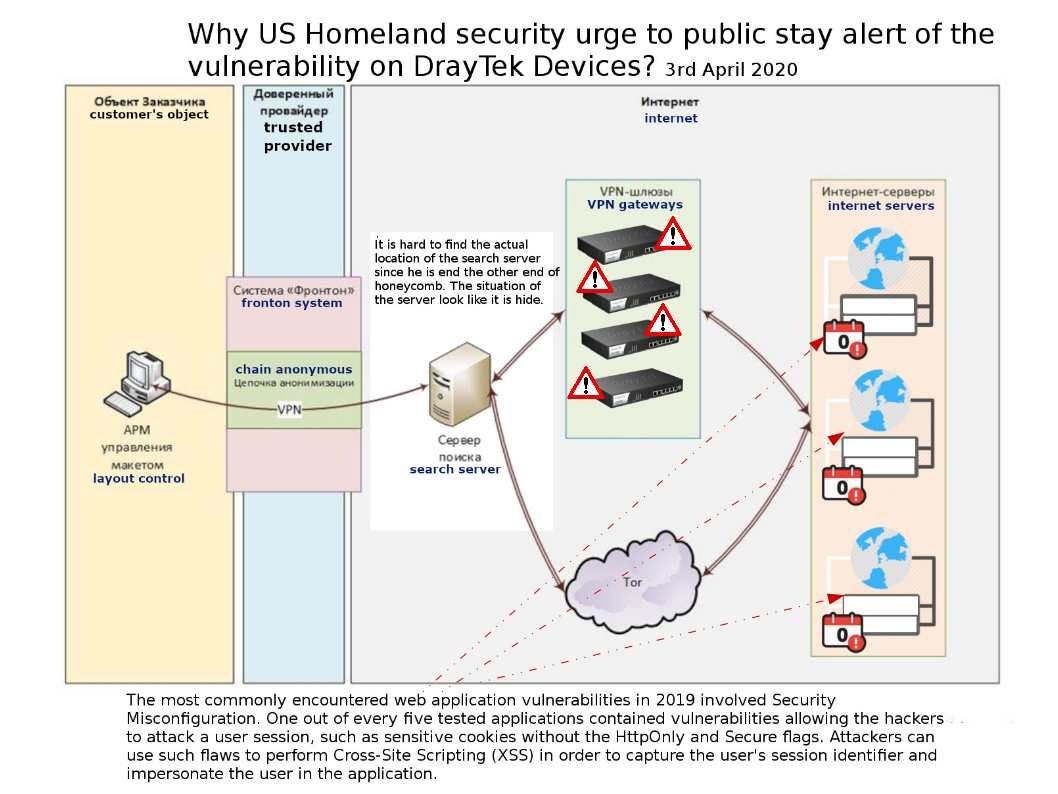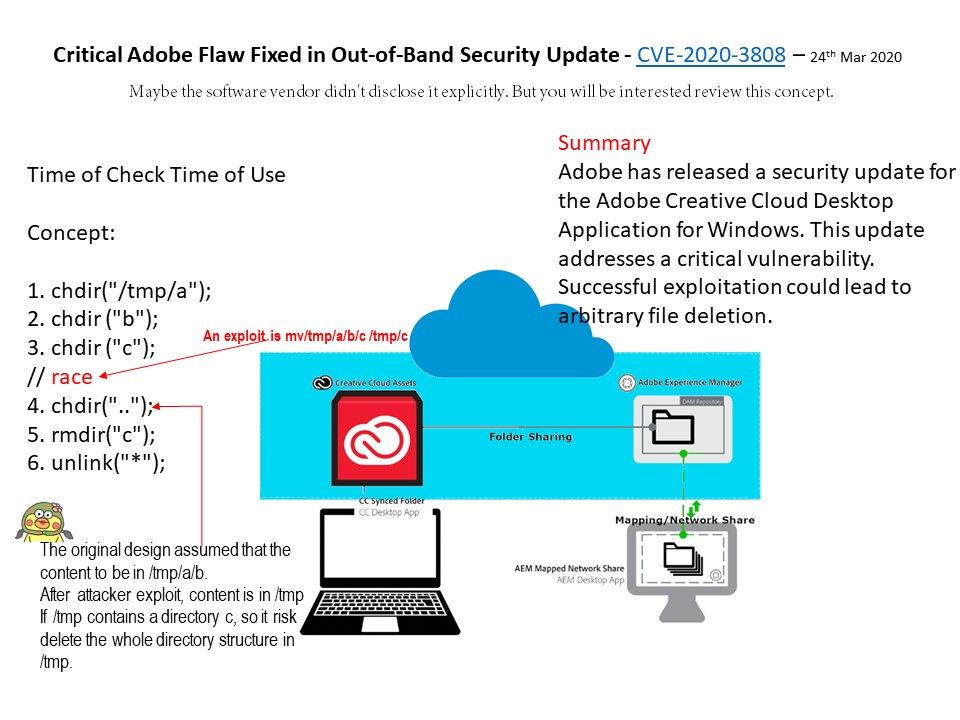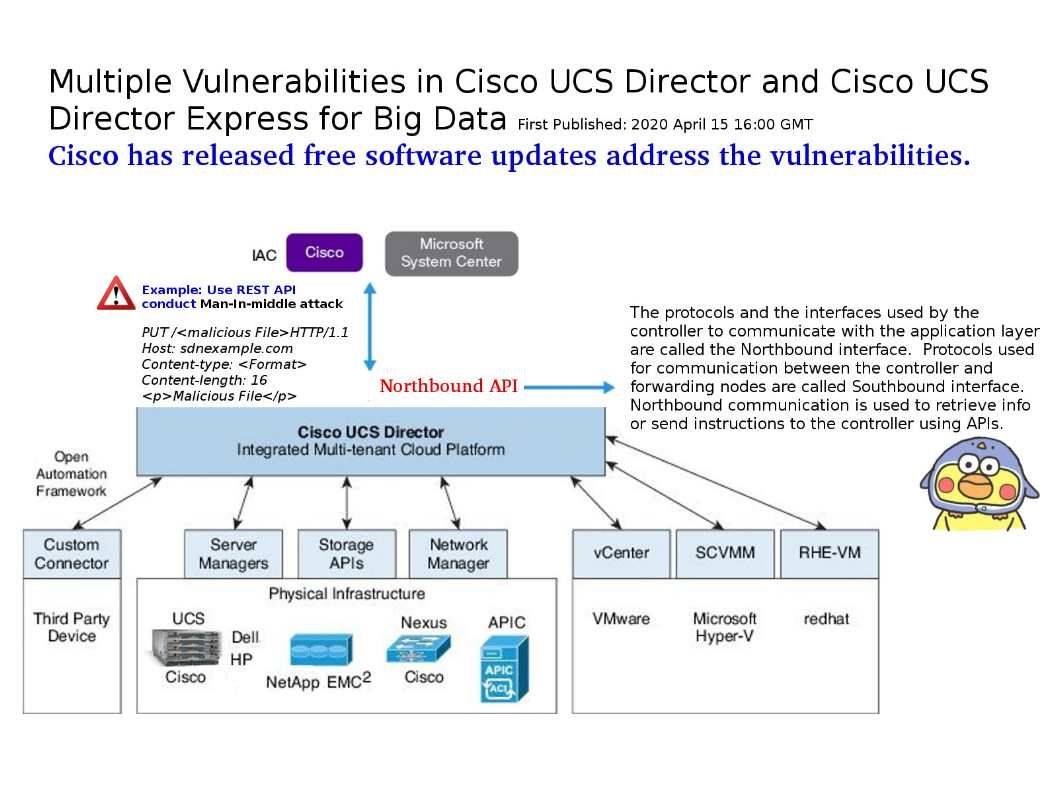
Preface: The protocols and the interfaces used by the controller to communicate with the application layer are called the Northbound interface. Protocols used for communication between the controller and forwarding nodes are called Southbound interface. Northbound communication is used to retrieve info or send instructions to the controller using APIs.
Vulnerability details: Multiple vulnerabilities in the REST API of Cisco UCS Director and Cisco UCS Director Express for Big Data may allow a remote attacker to bypass authentication or conduct directory traversal attacks on an affected device. For details, please refer official announcement – https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-ucsd-mult-vulns-UNfpdW4E
Other potential impact: The application entry point to the SDN deployment is through the controller via the Northbound Interface (NBI). If the communication is done using REST APIs with lacking proper protection, PUT method can be used to alter configurations or add malicious files that can alter other devices.These attacks are related to the communication over whether the Northbound Interface (NBI) or Southbound Interface (SBI). Some attacks are related to software. For details, please refer to the attached drawings.
.jpg?width=1920&height=1080&fit=bounds)
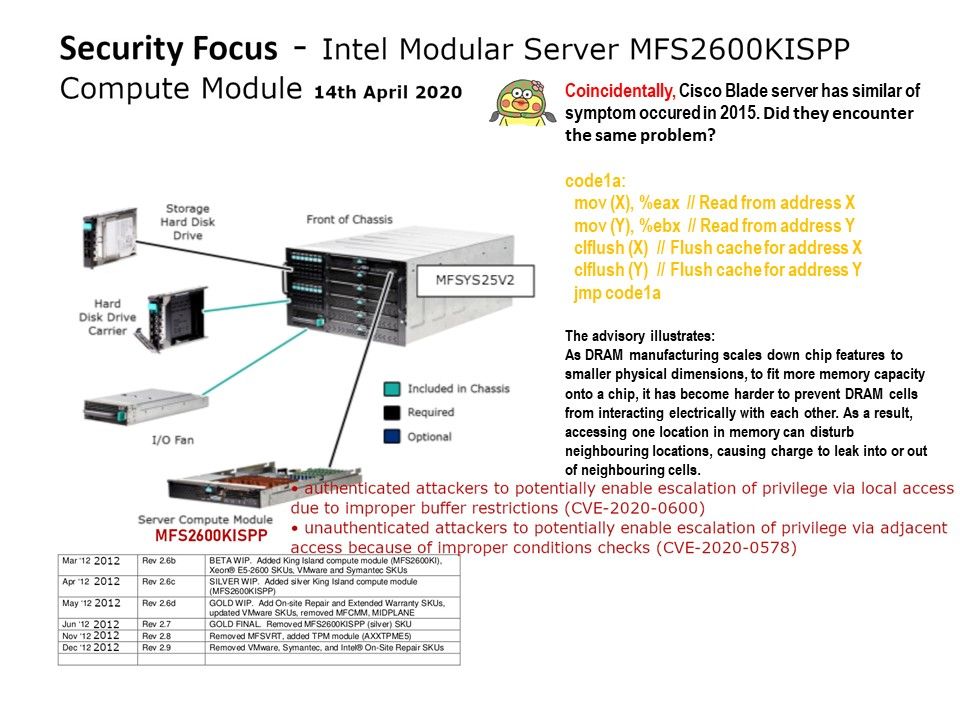
.jpg?width=1920&height=1080&fit=bounds)