Preface: Most memory corruption is actually due to heap corruption. To find where the memory address is modified.
- Set a data breakpoint 0x00408000
- When you hit the breakpoint, use the memory window to view meory contents starting at 0x00408000.
STR instructions store a register value into memory. The memory address to load from or store to is at an offset from the register Rn . The offset is specified by the register Rm and can be shifted left by up to 3 bits using LSL . The value to load or store can be a byte, halfword, or word.
std::unique_ptr is a smart pointer that owns and manages another object through a pointer and disposes of that object when the unique_ptr goes out of scope.
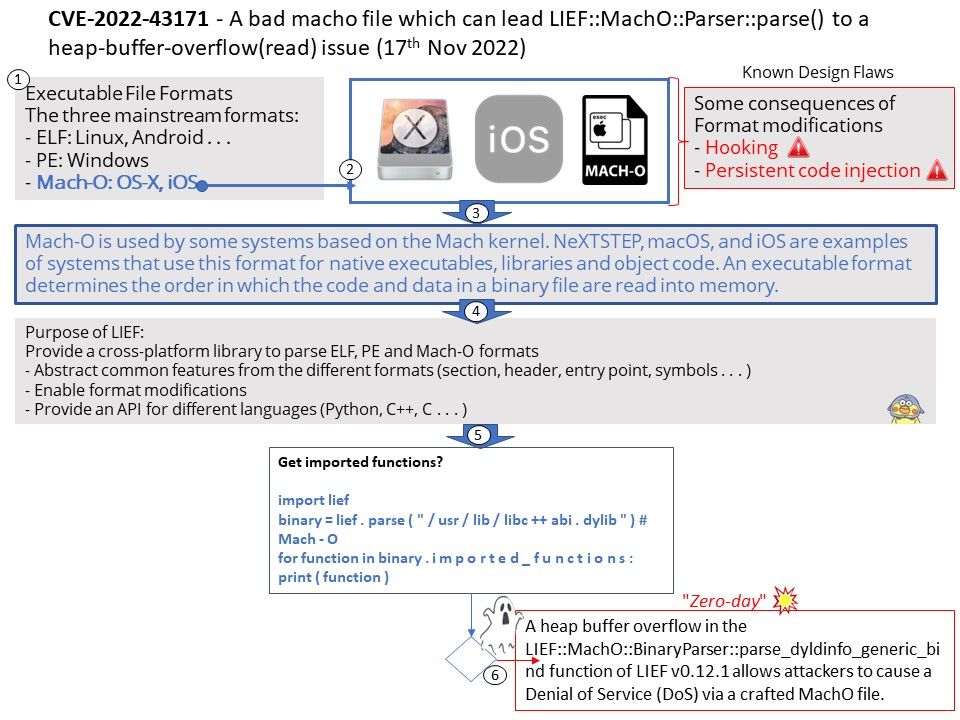
Background: Mach-O, short for Mach object file format, is a file format for executables, object code, shared libraries, dynamically-loaded code, and core dumps. An executable format determines the order in which the code and data in a binary file are read into memory.
Mach-O is used by some systems based on the Mach kernel. NeXTSTEP, macOS, and iOS are examples of systems that use this format for native executables, libraries and object code.
With the introduction of Mac OS X 10.6 platform the Mach-O file underwent a significant modification that causes binaries compiled on a computer running 10.6 or later to be (by default) executable only on computers running Mac OS X 10.6 or later.
Vulnerability details: A heap buffer overflow in the LIEF::MachO::BinaryParser::parse_dyldinfo_generic_bind function of LIEF v0.12.1 allows attackers to cause a Denial of Service (DoS) via a crafted MachO file.
Official announcement: Please refer to the link for details – https://github.com/lief-project/LIEF/issues/782