Preface: There are many ways to do file based IO in Linux. The oldest and most basic are the read(2) and write(2) system calls.
io_uring is a system call interface for Linux. It was first introduced in upstream Linux Kernel version 5.1 in 2019 . It enables an application to initiate system calls that can be performed asynchronously.
Background: In the Linux kernel, reference counting (refcount) has become a default mechanism that manages resource objects. A refcount of a tracked object is incremented when a new reference is assigned and decremented when a reference becomes invalid.
io_uring is a new asynchronous I/O API for Linux created by Jens Axboe from Facebook. It aims at providing an API without the limitations of the current select(2), poll(2), epoll(7) or aio(7) family of system calls.
Reference counting allows clients of your library to keep reference objects created by your library on the heap and allows you to keep track of how many references are still active. When the reference count goes to zero you can safely free the memory used by the object.
The kernel implements reference counting, so the kernel object is not closed until all the file handles pointing to it are closed.
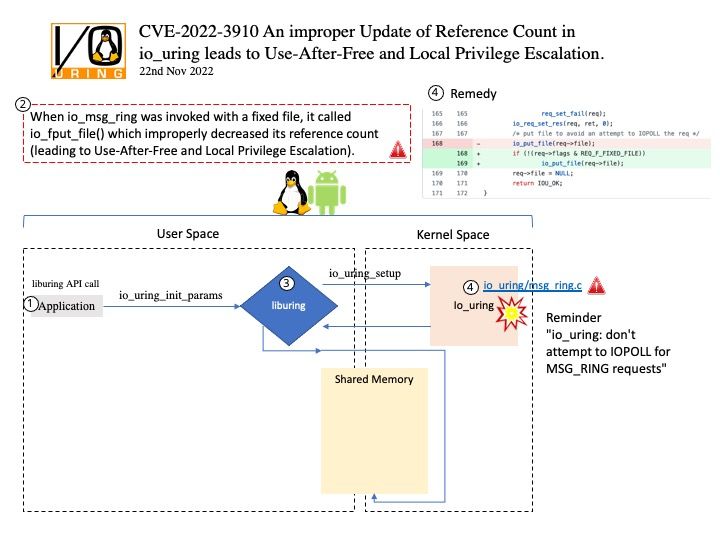
Vulnerability details: Use After Free vulnerability in Linux Kernel allows Privilege Escalation. An improper Update of Reference Count in io_uring leads to Use-After-Free and Local Privilege Escalation. When io_msg_ring was invoked with a fixed file, it called io_fput_file() which improperly decreased its reference count (leading to Use-After-Free and Local Privilege Escalation).
Solution: Applying the patch fc7222c3a9f56271fba02aabbfbae999042f1679 is able to eliminate this problem.
Official announcement: Please refer to the link for details – https://github.com/torvalds/linux/commit/fc7222c3a9f56271fba02aabbfbae999042f1679